...
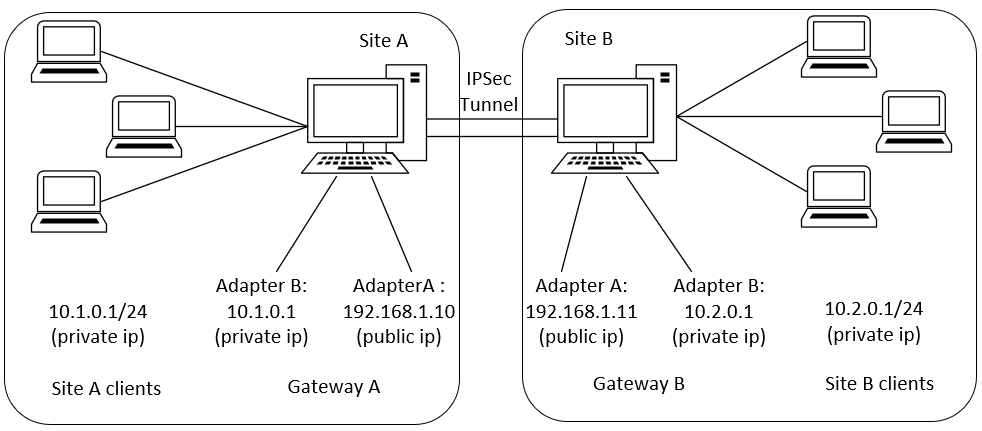
In this scenario, both sites have static public IP address and setup a tunnel between sites. After the tunnel is established, the clients within the site should be able to ping the clients on the other side through the tunnel. The tunnel is authenticated through pre-shared key.
...
Scenario Description:
Tunnel between site A and site B
Suppose there are two sites A and B. A comes with the subnet 10.1.0.1/24, B comes with the subnet 10.2.0.1/24
Gateway for A is 192.168.1.10
Gateway for B is 192.168.1.11
A and B would like to establish a tunnel
10.1.0.1/24 == 10.2.0.1/24
CRs for the scenario:
| Code Block | ||||||
|---|---|---|---|---|---|---|
| ||||||
apiVersion: sdewan.akraino.org/v1alpha1
kind: IpsecProposal
metadata:
name: test_proposal_1
namespace: default
labels:
sdewanPurpose: cnf-1
spec:
encryption_algorithm: aes128
hash_algorithm: sha256
dh_group: modp3072
status:
appliedVersion: "1"
appliedTime: "2020-04-12T09:28:38Z"
inSync: True
|
| Code Block | ||||||
|---|---|---|---|---|---|---|
| ||||||
apiVersion: sdewan.akraino.org/v1alpha1
kind: IpsecSite
metadata:
name: siteA
namespace: default
labels:
sdewanPurpose: cnf-1
spec:
remote: 192.168.1.11
authentication_method: psk
pre_shared_key: test123
crypto_proposal:
- test_proposal_1
connections | ||||||
| Code Block | ||||||
| ||||||
apiVersion: sdewan.akraino.org/v1alpha1 kind: IPSecSite metadata: name: siteA spec: sites: - name: siteA gateway: 192.168.1.11 pre_shared_key: test123 authentication_method: psk local_identifier: @sun.strongswan.org remote_identifier: @moon.strongswan.org crypto_proposal: - proposal1 force_crypto_proposal: "0" connections: - name: connA type: tunnel mode: start local_subnet: 10.1.0.1/24 local_sourceip: 192.168.1.10 remote_subnet: 10.2.0.1/24 crypto_proposal: - proposal1 proposals: - connection_name: proposal1connection_A encryption_algorithmtype: aes128tunnel hash_algorithmmode: sha256start dhlocal_group: modp3072 |
IPSec CR for gateway B:
subnet: 10.1.0.1/24
remote_subnet: 10.2.0.1/24
crypto_proposal:
- test_proposal_1
status:
appliedVersion: "1"
appliedTime: "2020-04-12T09:28:38Z"
inSync: True |
| Code Block | ||||||
|---|---|---|---|---|---|---|
| ||||||
apiVersion: sdewan.akraino.org/v1alpha1
kind: IpsecSite
metadata:
name: siteB
namespace: default
labels | ||||||
| Code Block | ||||||
| ||||||
apiVersion: sdewan.akraino.org/v1alpha1 kind: IPSecSite metadata: name: siteB spec: sites: - name: siteB gateway: 192.168.1.10 pre_shared_key: test123 authentication_method: psk local_identifier: @moon.strongswan.org remote_identifier: @sun.strongswan.org crypto_proposal: sdewanPurpose: - proposal1cnf-1 spec: remote: 192.168.1.10 authentication_method: psk force_pre_shared_key: test123 crypto_proposal: "0" - test_proposal_1 connections: - connection_name: connAconnection_B type: tunnel mode: start local_subnet: 10.2.0.1/24 localremote_sourceipsubnet: 19210.1681.1.11 remote_subnet: 10.1.0.0.1/24 crypto_proposal: - proposal1 proposalstest_proposal_1 status: - nameappliedVersion: proposal1"1" encryption_algorithm: aes128 hash_algorithm: sha256 dh_group: modp3072appliedTime: "2020-04-12T09:28:38Z" inSync: True |
NAT CR:
| Code Block |
|---|
Rest calls:
...
{ { "name": “siteA", "gatewayremote":"192.168.1.11", "crypto_proposal": "proposal1test_proposal_1", "pre_shared_key": "test123", "authentication_method": "psk", "local_identifier": "@moon.strongswan.org", "connections": [ { "name": "connection_A", "type": "tunnel", "remote_identifiermode": "@sun.strongswan.org", "connections": [ { "name": "connA", "type": "tunnel", "mode": "start", "start", "local_subnet": "10.1.0.1/24", "remote_subnet": "10.2.0.1/24", "crypto_proposal": "proposal1test_proposal_1" } ] }, { "name": "siteB", "gateway":"192.168.1.10", "crypto_proposal": "proposal1test_proposal_1", "pre_shared_key": "test123", "authentication_method": "psk", "remote_identifier": "@moon.strongswan.org", "local_identifier": "@sun.strongswan.org", "connections": [ { "name": "connAconnection_B", "type": "tunnel", "mode": "start", "local_subnet": "10.2.0.1/24", "remote_subnet": "10.1.0.1/24", "crypto_proposal": "proposal1test_proposal_1" } ] } ] |
|---|
...
{ "proposals": [ { "name": "proposal1", "crypto_algorithm": "aes128", "hash_algorithm": "sha256", "dh_group": "modp3072" } ] } |
|---|
Decomposed Scenario B: Host-to-Site
...
tunnel when the initiator requests an overlay IP
In this scenario, the initiator sends out a request to the responderthe responder(either a site gateway/remote host) which has a static public ip address(or dynamic pubic IP with static domain name) in order to setup a tunnel between. However, this time, the roadwarrior is also going to ask for a virtual IP that assigned by the responder. After the tunnel is established, the roadwarrior should be able to ping the clients on the other side through the tunnel. The tunnel is authenticated through pre-shared key.
...
get an overlay IP and ping the clients on the other side through the tunnel. The tunnel is authenticated through pre-shared key.
Scenario Description:
Tunnel between site A and host B(Responder and Initiator)
Suppose there is one site A and one host B. A comes with the subnet 10.1.0.1/24.
Gateway for A is 192.168.1.10 which is a public ip address
Host B has no public address and want to request one from the peer(suppose the vip assigned is 10.3.0.12)
A and B would like to establish a tunnel
10.1.0.1/24 == 10.3.0.12/32
CRs for the scenario:
| Code Block | ||||||
|---|---|---|---|---|---|---|
| ||||||
apiVersion: sdewan.akraino.org/v1alpha1
kind: IpsecProposal
metadata:
name: test_proposal_1
namespace: default
labels:
sdewanPurpose: cnf-1
spec:
encryption_algorithm: aes128
hash_algorithm: sha256
dh_group: modp3072
status:
appliedVersion: "1"
appliedTime: "2020-04-12T09:28:38Z"
inSync: True
|
| Code Block | ||||||
|---|---|---|---|---|---|---|
| ||||||
apiVersion: sdewan sdewan.akraino.org/v1alpha1 kind: IPSecSite metadata: name: siteA spec: sites: - name: siteA gateway: 192.168.1.15v1alpha1 kind: IpsecSite metadata: name: siteA namespace: default labels: pre_shared_keysdewanPurpose: test123 authentication_method: pskcnf-1 spec: local_identifierremote: @sun.strongswan.org%any remoteauthentication_identifiermethod: @roadwarrior.strongswan.orgpsk pre_shared_key: test crypto_proposal: - proposal1 force_crypto_proposal: "0" test_proposal_1 connections: - connection_name: connAconnection_A type: tunnel mode: start local_subnet: 10.1.0.1/24 local_sourceip: 192.168.1.1024 remote_sourceip: 19210.3.1680.1.15/24 crypto_proposal: - proposal1 proposaltest_proposal_1 status: - nameappliedVersion: proposal1"1" encryption_algorithm: aes128 hash_algorithm: sha256 dh_group: modp3072 |
...
appliedTime: "2020-04-12T09:28:38Z"
inSync: True |
| Code Block | ||||||
|---|---|---|---|---|---|---|
| ||||||
apiVersion: sdewan sdewan.akraino.org/v1alpha1 kind: IPSecSite IpsecHost metadata: name name: roadwarriorhostB spec: sitesnamespace: default - namelabels: roadwarrior gatewaysdewanPurpose: 192.168.1.10 pre_shared_key: test123 cnf-1 spec: remote: 192.168.1.10 authentication_method: psk local_identifier: @roadwarrior.strongswan.org remote_identifier: @sun.strongswan.orgpre_shared_key: test crypto_proposal: - proposal1 force_crypto_proposal: "0" test_proposal_1 connections: - connection_name: connAconnection_A type: tunnel mode: start local_sourceip: 192.168.1.15 remote_sourceip: 192.168.1.10%config remote_subnet: 100.10.0.10/240 crypto_proposal: - proposal1 proposal: - name: proposal1 encryption_algorithm: aes128 hash_algorithm: sha256 dh_group: modp3072test_proposal_1 status: appliedVersion: "1" appliedTime: "2020-04-12T09:28:38Z" inSync: True |
NAT CR:
| Code Block |
|---|
Rest calls:
...
{ { "name": "siteA", "gatewayremote":"192.168.1.11%any", "crypto_proposal": "proposal1test_proposal_1", "pre_shared_key": "test123", "authentication_method": "psk", "local_identifier": "@moon.strongswan.org", "remote_identifier": "@sun.strongswan.org", "connections": [ { "name": "connA", "type": "tunnel", "mode": "start", "local_subnet": "10.1.0.1/24", "remote_sourceip": "192.168.1.15", "local "remote_sourceip": "19210.3.1680.1.10/24", "crypto_proposal": "proposal1test_proposal_1" } ] }, { "name": "roadwarriorhostB", "gatewayremote":"192.168.1.10", "crypto_proposal": "proposal1test_proposal_1", "pre_shared_key": "test123", "authentication_method": "psk", "remote_identifier": "@moon.strongswan.org", "local_identifier": "@sun.strongswan.org", "connections": [ { "name": "connA", "type": "tunnel", "mode": "start", "local_sourceip": "192.168.1.15", "remote_sourceip": "192.168.1.10"%config", "remote_subnet": "10.1.0.1/24", "crypto_proposal": "proposal1test_proposal_1" } ] } ] |
|---|
...
{ "proposals": [ { "name": "proposal1", "crypto_algorithm": "aes128", "hash_algorithm": "sha256", "dh_group": "modp3072" } ] } |
|---|
Decomposed Scenario C: Host
...
to host tunnel
Setup a tunnel between the host who got assigned the virtual IP and another host with PIP.
Scenario Description:
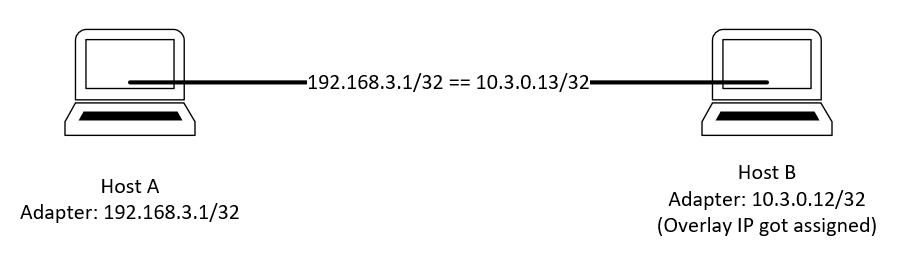
Tunnel between host A and host B
Suppose there are two hosts A and B.
A has a public ip which is 192.168.3.1
B is a host which already get a vip 10.3.0.12
A and B would like to establish a tunnel
192.168.3.1/32 == 10.3.0.12/32
CRs for the scenario
In this scenario, the initiator sends out a request to the responder(either a site gateway/remote host) which has a static public ip address(or dynamic pubic IP with static domain name) in order to setup a tunnel between. However, this time, the roadwarrior is also going to ask for a virtual IP that assigned by the responder. After the tunnel is established, the roadwarrior should be able to get an overlay IP and ping the clients on the other side through the tunnel. The tunnel is authenticated through pre-shared key.
...
:
| Code Block | ||||||
|---|---|---|---|---|---|---|
| ||||||
apiVersion: sdewan sdewan.akraino.org/v1alpha1 kind: IPSecSite IpsecProposal metadata: name: siteA spec: sites: - name: siteA gateway: any pre_shared_key: test123 name: test_proposal_1 namespace: default labels: authentication_methodsdewanPurpose: pskcnf-1 spec: localencryption_identifieralgorithm: @moon.strongswan.orgaes128 remotehash_identifieralgorithm: @roadwarrior.strongswan.orgsha256 cryptodh_proposalgroup: - proposal1 modp3072 status: appliedVersion: force_crypto_proposal"1" appliedTime: "02020-04-12T09:28:38Z" connections:inSync: True |
| Code Block | ||||||
|---|---|---|---|---|---|---|
| ||||||
apiVersion: sdewan.akraino.org/v1alpha1 kind: IpsecHost metadata: name: hostA namespace: default - namelabels: connA type: tunnelsdewanPurpose: cnf-1 spec: remote: %any modeauthentication_method: startpsk local_subnet: 10.1.0.1/24 local_sourceip: 192.168.1.10pre_shared_key: test crypto_proposal: - remote_sourceip: 10.3.0.1/24test_proposal_1 connections: crypto- connection_proposalname: connection_A type: tunnel - proposal1 proposalmode: start - nameremote_sourceip: proposal110.3.0.12 encryptioncrypto_algorithmproposal: aes128 - hash_algorithm: sha256test_proposal_1 status: appliedVersion: "1" dh_group: modp3072 |
...
appliedTime: "2020-04-12T09:28:38Z"
inSync: True |
| Code Block | ||||||
|---|---|---|---|---|---|---|
| ||||||
apiVersion: sdewan sdewan.akraino.org/v1alpha1 kind: IPSecSite IpsecHost metadata: name: hostB namenamespace: roadwarriordefault spec: siteslabels: - namesdewanPurpose: roadwarriorcnf-1 spec: gatewayremote: 192.168.3.1.10 pre_shared_key: test123 authentication_method: psk local_identifier: @roadwarrior.strongswan.org remote_identifier: @moon.strongswan.orgpre_shared_key: test crypto_proposal: - proposal1 force_crypto_proposal: "0" test_proposal_1 connections: - connection_name: connAconnection_A type: tunnel mode: start local_sourceip: %config remote_sourceip: 192.168.1.10start remotelocal_subnetsourceip: 10.13.0.1/2413 crypto_proposal: - test_proposal_1 proposal1 proposalstatus: - nameappliedVersion: proposal1"1" encryption_algorithm: aes128 hash_algorithm: sha256 dh_group: modp3072appliedTime: "2020-04-12T09:28:38Z" inSync: True |
NAT CR:
| Code Block |
|---|
Rest calls:
...
GET /cgi-bin/luci/sdewan/ipsec/v1/sites
{ { |
|---|
"name": " |
|---|
hostA", " |
|---|
remote":" |
|---|
%any", "crypto_proposal": " |
|---|
test_proposal_1", "pre_shared_key": "test123", "authentication_method": "psk", "local_identifier": "@moon.strongswan.org", "remote_identifier": "@sun.strongswan.org", "connections": [ { |
|---|
"type": "tunnel",
"mode": "start",
"local_subnet": "10.1.0.1/24"name": "connA", " |
|---|
type": " |
|---|
tunnel",
|
|---|
"mode": "start", "remote_sourceip": " |
|---|
10. |
|---|
3. |
|---|
0. |
|---|
12", "crypto_proposal": " |
|---|
test_proposal_1" } ] }, { "name": " |
|---|
hostB", " |
|---|
remote":"192.168.3.1 |
|---|
", "crypto_proposal": " |
|---|
test_proposal_1", "pre_shared_key": "test123", "authentication_method": "psk", "remote_identifier": "@moon.strongswan.org", "local_identifier": "@sun.strongswan.org", "connections": [ { "name": "connA", "type": "tunnel", "mode": "start", "local |
|---|
_sourceip": " |
|---|
10 |
|---|
.3.0. |
|---|
12", "crypto_proposal": " |
|---|
test_proposal_1" } ] } ] |
|---|
Proposal settings
GET /cgi-bin/luci/sdewan/ipsec/v1/proposals
{ "proposals": [ { |
|---|
"crypto_algorithm": "aes128", "hash_algorithm": "sha256", "dh_group": "modp3072" } ] } |
|---|
Verified Scenario:
Overall Scenario:
Here shows the overall scenario we want to achieve in the ICN SDEWAN case.
...