...
- Export Restful API interface to support configuration of MWAN3, Firewall & NAT, IpSec.
- Site-to-Site tunnels across edges & edges & central orchestrators and application managers
SDEWAN Service
SDEWAN service restful API provides the capability to list available SDEWAN services, get service status and execute service operation.
Common Error code:
...
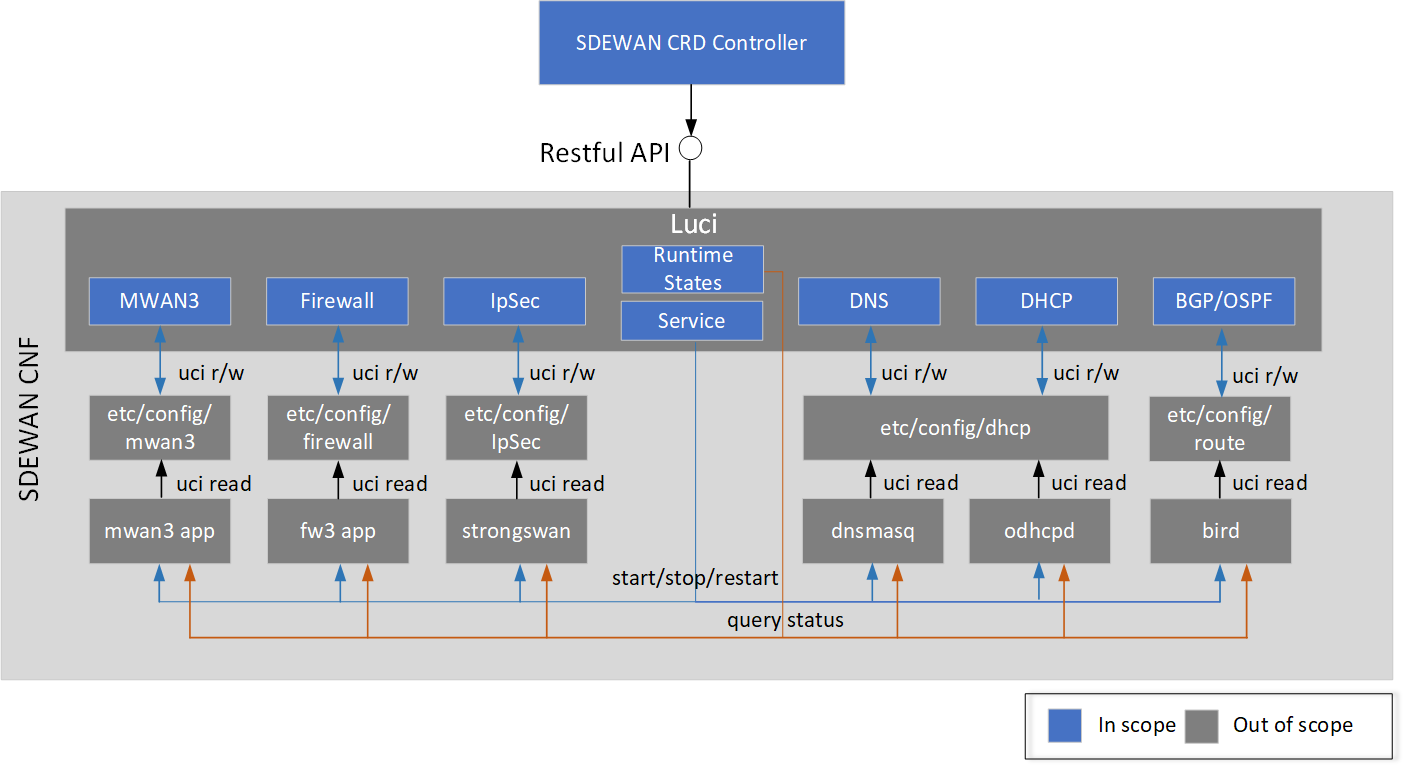
Architecture
SDEWAN CNF enhances OpenWRT Luci web interface with SDEWAN controllers to provide Restful API for network functions' configuration and control.
CNF includes below modules:
- MWAN3: mwan3 configuration for multiple WAN links’ management
- Firewall: fw3 configuration for firewall rule, NAT rule.
- IpSec: strongswan configuration to setup security tunnel between CNFs
- DNS/DHCP: dnsmasq configuration for DNS and DHCP (ip4) or odhcpd configuration for DHCP (ip6)
- BGP/OSPF: bird configuration for BGP/OSPF auto routing
- Service: manage (e.g. start, stop, restart etc.) lifecycle of network function applications (e.g. mwan3, fw3, strongswan etc.)
- Runtime States: exports system log for debugging
APIs
Common Error code:
| Code | Description |
|---|---|
| 400 | Bad request |
| 401 | unauthorized -the security token is not provides or expired. |
| 404 | resource not found |
Error Response:
| Name | In | Type | Description |
|---|---|---|---|
| message | body | string | error message |
SDEWAN Service
SDEWAN service restful API provides the capability to list available SDEWAN services, get service status and execute service operation.
PUT /cgi-bin/luci/sdewan/v1/services/{service-name}/
Execute a operation for a service
Request:
Request Parameters
Name In Type Description service-name path string service name, valid value are "mwan3", "firewall", "ipsec" action body string action to be executed. valid value are "start", "stop", "restart", "reload" Request Example
{
"action": "start"
}
Response
- Normal response code: 200
- Error response code: 400 (e.g. invalid action)
Response Parameters
Name In Type Description result body string operation execution result Response Example
{
"result": "success"
}
GET /cgi-bin/luci/sdewan/v1/services
Lists all available sdewan services supported by SDEWAN CNF
Request: N/A
Response
- Normal response codes: 200
Response Parameters
Name In Type Description services body array a list of supported service - Response Example
{
"services": ["mwan3", "firewall", "ipsec"]
}
SDEWAN Interface
SDEWAN interface API provide network interfaces information and control to up/down a network interface
PUT /cgi-bin/luci/sdewan/v1/interfaces/{interface}/
Execute a operation for a service
Request:
Request Parameters
Name In Type Description interface path string interface name, e.g. "eth0" action body string action to be executed. valid value are "up", "down" Request Example
{
"action": "up"
}
Response
- Normal response code: 200
- Error response code: 400 (e.g. invalid action), 404 (e.g. interface not found)
Response Parameters
Name In Type Description result body string operation execution result Response Example
{
"result": "success"
}
GET /cgi-bin/luci/sdewan/v1/interfaces
Lists all available network interfaces of the SDEWAN CNF
Request: N/A
Response
- Normal response codes: 200
Response Parameters
Name In Type Description interfaces body array a list of available network interfaces ip_address body array ip address of the interface ip6_address body array ipv6 address of the interface mac_address body string mac address of the interface status body string interface status, valid value are "UP", "DOWN" received_packets body string number of received packets send_packets body string number of send packaets - Response Example
{"interfaces": [
{ "ip_address: ["10.0.0.1"],
"name":"eth0",
"status":"UP",
"send_packets":"19148",
"mac_address":"22:22:22:22:22:22",
"receive_packets":"20923" }
]}
GET /cgi-bin/luci/sdewan/v1/interfaces/{interface-name}
get information of a network interfaces of the SDEWAN CNF
Request: N/A
Response
- Normal response codes: 200
Response Parameters
Name In Type Description interface-name path string interface name ip_address body array ip address of the interface ip6_address body array ipv6 address of the interface mac_address body string mac address of the interface status body string interface status, valid value are "UP", "DOWN" received_packets body string number of received packets send_packets body string number of send packaets - Response Example
{ "ip_address: ["10.0.0.1"],
"name":"eth0",
"status":"UP",
"send_packets":"19148",
"mac_address":"22:22:22:22:22:22",
"receive_packets":"20923" }
MWAN3
OpenWRT MWAN3 configuration includes below sections:
- Global: common configuration special used to configure routable loopback address (for OpenWRT 18.06)
- Interface: define how each WAN interface is tested for up/down status
- Member: represents an interface with a metric and a weight value
- Policy: defines how traffic is routed through the different WAN interface(s)
- Rule: describes what traffic to match and what policy to assign for that traffic.
SDEWAN CNF will be created with Global and Interface sections initialized based on CNF allocated interfaces.
SD-EWAN MWAN3 CNF API provides support to get/create/update/delete MWAN3 Rule, Policy (with Member).
MWAN3 Policy
POST /cgi-bin/luci/sdewan/mwan3/v1/policies
create a new policy
Request:
Request Parameters: same with PUT's request
- Request Example: same with PUT's example
Response
- Normal response codes: 201
- Error response codes: 400, 401
PUT /cgi-bin/luci/sdewan/mwan3/v1/policies/{policy-name}
update a policy
Request:
Request Parameters:
Name In Type Description policy-name path string policy name members body array policy members interface body string member interface name metric body int (optional) default: 1, members within one policy with a lower metric have precedence over higher metric members weight body int (optional) default: 1, members with same metric will distribute load based on this weight value - Request Example
PUT /cgi-bin/luci/sdewan/mwan3/v1/policies/balanced
{
"members": [
{
"interface": "net1",
"metric" 1,
"weight": 2
}
{
"interface": "net2",
"metric" 1,
"weight": 1
}
]
}
Response
- Normal response codes: 204
- Error response codes: 400, 401, 404
GET /cgi-bin/luci/sdewan/mwan3/v1/policies
Lists all defined policies
Request: N/A
Response
- Normal response codes: 200
Response Parameters
Name In Type Description policies body array a list of defined policies - Response Example
{
"policies": [{
"name":"balanced",
"members": [
{
"interface": "net1",
"metric" 1,
"weight": 2
}
{
"interface": "net2",
"metric" 1,
"weight": 1
}
]
}
]
}
GET /cgi-bin/luci/sdewan/mwan3/v1/policies/{policy-name}
Get a policy
Request: N/A
Request Parameters
Name In Type Description policy-name path string policy name
Response
- Normal response codes: 200
- Error response code: 404
Response Parameters
Name In Type Description name body string policy name members body array policy members interface body string member interface name metric body int (optional) default: 1, members within one policy with a lower metric have precedence over higher metric members weight body int (optional) default: 1, members with same metric will distribute load based on this weight value - Response Example
{
"name": "balanced",
"members": [
{
"interface": "net1",
"metric" 1,
"weight": 2
}
{
"interface": "net2",
"metric" 1,
"weight": 1
}
]
}
DELETE /cgi-bin/luci/sdewan/mwan3/v1/policies/{policy-name}
delete a policy
Request:
Request Parameters
Name In Type Description policy-name path string policy name
Response
- Normal response codes: 200
- Error response codes: 401, 404
MWAN3 Rule
POST /cgi-bin/luci/sdewan/mwan3/v1/rules
create a new rule
Request:
Request Parameters: same with PUT's request
- Request Example: same with PUT's example
Response
- Normal response codes: 201
- Error response codes: 400, 401
PUT /cgi-bin/luci/sdewan/mwan3/v1/rules/{rule-name}
update a policy
Request:
Request Parameters
Name In Type Description rule-name path string rule name policy body string policy used for the rule src_ip body string (optional) source ip address src_port body string (optional) source port or port range dest_ip body string (optional) destination ip address dest_port body string (optional) destination port or port range proto body string (optional) protocol for the rule. Valid values: "tcp", "udp", "icmp", "all" family body string (optional) address family. Valid values: "ipv4", "ipv6", "all" sticky body string (optional) default: 0, allow traffic from the same source ip address within the timeout limit to use same wan interface as prior session timeout body int (optional) default: 600, Stickiness timeout value in seconds - Request Example
PUT /cgi-bin/luci/sdewan/mwan3/v1/rules/default_rule
{
"dest_ip": "0.0.0.0/0",
"policy": "balanced"
}
Response
- Normal response codes: 204
- Error response codes: 400, 401, 404
Error Response:
...
GET /cgi-bin/luci/sdewan/mwan3/v1/servicesrules
Lists all available sdewan services supported by SDEWAN CNFdefined rules
Request: N/A
Response
- Normal response codes: 200
Response Parameters
Name In Type Description servicesrules body array a list of supported servicedefined rules - Response Example
{
"services": ["mwan3", "firewall", "ipsec"
"rules": [
{
"name":"default_rule",
"dest_ip": "0.0.0.0/0",
"policy": "balanced"
}
]
}
PUT GET /cgi-bin/luci/sdewan/mwan3/v1/servicerules/{servicerule-name}/
Execute a operation for a service
Request:
Get a rule
Request: N/A
Request Parameters
Name In Type Description rule-name path string rule name Request Parameters
Name In Type Description service path string service name, valid value are "mwan3", "firewall", "ipsec" action body string action to be executed. valid value are "start", "stop", "restart", "reload" Response Example
{
"action": "start"
}
Response
- Normal response codecodes: 200
- Error response code: 400 (e.g. invalid action)404
Response Parameters
Name In Type Description resultDescription name body string rule name policy body string operation execution result Response Example
{
"result": "success"
}
MWAN3
OpenWRT MWAN3 configuration includes below sections:
- Global: common configuration special used to configure routable loopback address (for OpenWRT 18.06)
- Interface: define how each WAN interface is tested for up/down status
- Member: represents an interface with a metric and a weight value
- Policy: defines how traffic is routed through the different WAN interface(s)
- Rule: describes what traffic to match and what policy to assign for that traffic.
SDEWAN CNF will be created with Global and Interface sections initialized based on CNF allocated interfaces.
SD-EWAN MWAN3 CNF API provides support to get/create/update/delete MWAN3 Rule, Policy (with Member).
MWAN3 Policy
GET /cgi-bin/luci/sdewan/mwan3/v1/policies
Lists all defined policies
Request: N/A
Response
...
Response Parameters
...
policy used for the rule src_ip body string (optional) source ip address src_port body string (optional) source port or port range dest_ip body string (optional) destination ip address dest_port body string (optional) destination port or port range proto body string (optional) protocol for the rule. Valid values: "tcp", "udp", "icmp", "all" family body string (optional) address family. Valid values: "ipv4", "ipv6", "all" sticky body string (optional) default: 0, allow traffic from the same source ip address within the timeout limit to use same wan interface as prior session timeout body int (optional) default: 600, Stickiness timeout value in seconds - Response Example
#ipv4 example
{
"name":"default_rule",
"dest_ip": "0.0.0.0/0",
"policy": "balanced"
}
#ipv6 example
{
"name":"default_ipv6_rule",
"dest_ip": "fdca:f00:ba3::/64",
"policy": "balanced"
}
DELETE
...
{
"policies": [
{
"name":"balanced",
"members": [
{
"interface": "net1",
"metric" 1,
"weight": 2
}
{
"interface": "net2",
"metric" 1,
"weight": 1
}
]
}
]
}
GET /cgi-bin/luci/sdewan/mwan3/v1/policy/{policy}
Get a policy
Request: N/A
Request Parameters
...
Response
rules/{rule-name}
delete a rule
Request:
Request
- Normal response codes: 200
- Error response code: 404
Response Parameters
Response ExampleName In Type Description rule-name bodypath string policy namerule name members body array policy members interface body string member interface name metric body int (optional) default: 1, members within one policy with a lower metric have precedence over higher metric members weight body int (optional) default: 1, members with same metric will distribute load based on this weight value {
"name": "balanced",
"members": [
{
"interface": "net1",
"metric" 1,
"weight": 2
}
{
"interface": "net2",
"metric" 1,
"weight": 1
}
]
}
Response
- Normal response codes: 200
- Error response codes: 401, 404
Firewall
OpenWRT Firewall configuration includes below sections:
- Default: declares global firewall settings which do not belong to specific zones
- Include: used to enable customized firewall scripts
- Zone: groups one or more interfaces and serves as a source or destination for forwardings, rules and redirects.
- Forwarding: control the traffic between zones
- Redirect: defines port forwarding (NAT) rules
- Rule: defines basic accept, drop, or reject rules to allow or restrict access to specific ports or hosts.
SDEWAN CNF will be created with Default sections initialized. Include section will not be implemented in this release.
SD-EWAN Firewall API provides support to get/create/update/delete Firewall Zone, Redirect, Rule and Forwardings
Zone
POST /cgi-bin/luci/sdewan/mwan3firewall/v1/policyzones
create a new policyzone
Request:
Request Parameters: same with GETPUT's response request
- Request Example: same with GETPUT's response example
Response
- Normal response codes: 201
- Error response codes: 400, 401
...
PUT /cgi-bin/luci/sdewan/mwan3firewall/v1/policyzones/{policyzone-name}
update a policyzone
Request:
Request Parameters:
Name In Type Description policy path string policy name members body array policy members interface body string member interface name metric body int (optional) default: 1, members within one policy with a lower metric have precedence over higher metric members weight body int (optional) default: 1, members with same metric will distribute load based on this weight value {
"members": [
{
"interface": "net1",
"metric" 1,
"weight": 2
}
{
"interface": "net2",
"metric" 1,
"weight": 1
}
]
}
Response
- Normal response codes: 204
- Error response codes: 400, 401, 404
Parameters:
Name In Type Description zone-name path string zone name network body array List of interfaces attached to this zone masq body boolean Specifies whether outgoing zone traffic should be masqueraded. "0" or "1" masq_src body string Limit masquerading to the given source subnets. masq_dest body string Limit masquerading to the given destination subnets masq_allow_invalid body boolean whether add DROP INVALIDrulesmtu_fix body boolean Enable MSS clamping for outgoing zone traffic input body string Default policy ( ACCEPT,REJECT,DROP) for incoming zone traffic.forward body string Default policy ( ACCEPT,REJECT,DROP) for forwarded zone traffic.output body string Default policy ( ACCEPT,REJECT,DROP) for output zone traffic.family body string The protocol family ( ipv4,ipv6orany) these iptables rules are for.subnet body string List of IP subnets attached to this zone extra_src body string Extra arguments passed directly to iptables for source classification rules. etra_dest body string Extra arguments passed directly to iptables for destination classification rules. - Request Example
PUT
...
/cgi-bin/luci/sdewan/mwan3/v1/
...
zones/wan
{
...
delete a policy
Request:
"network":"wan",
"input": "REJECT",
"output": "ACCEPT",
"forward": "REJECT",
"masq": "1",
"mtu_fix": "1"
}
Request Parameters
Name In Type Description policy path string policy name
Response
- Normal response codes: 200204
- Error response codes: 400, 401, 404
MWAN3 Rule
GET /cgi-bin/luci/sdewan/mwan3firewall/v1/ruleszones
Lists all defined ruleszones
Request: N/A
Response
- Normal response codes: 200
Response Parameters
Name In Type Description ruleszones body array a list of defined ruleszones - Response Example
{
"ruleszones": [{
"name":"wan",
"network":"wan",
"input": "REJECT",
"output": "ACCEPT",
"forward": "default_ruleREJECT",,
"dest_ipmasq": "0.0.0.0/01",
"policymtu_fix": "balanced1"
}
]
}
GET /cgi-bin/luci/sdewan/mwan3firewall/v1/rulezones/{rulezone-name}
Get a rulezone
Request: N/A
Request Parameters
...
Response
...
Response Parameters
...
A
Request Parameters
Name In Type Description zone-name path string zone name
Response
- Normal response codes: 200
- Error response code: 404
Response Parameters
Name In Type Description name body string (Required) zone name network body array List of interfaces attached to this zone masq body boolean Specifies whether outgoing zone traffic should be masqueraded. "0" or "1" masq_src body string Limit masquerading to the given source subnets. masq_dest body string Limit masquerading to the given destination subnets masq_allow_invalid body boolean whether add DROP INVALIDrulesmtu_fix body boolean Enable MSS clamping for outgoing zone traffic input body string Default policy ( ACCEPT,REJECT,DROP) for incoming zone traffic.forward body string Default policy ( ACCEPT,REJECT,DROP) for forwarded zone traffic.output body string Default policy ( ACCEPT,REJECT,DROP) for output zone traffic.family body string The protocol family ( ipv4,ipv6orany) these iptables rules are for.subnet body string List of IP subnets attached to this zone extra_src body string Extra arguments passed directly to iptables for source classification rules. etra_dest body string Extra arguments passed directly to iptables for destination classification rules. - Response Example
{
"name":"wan",
"network":"wan",
"input": "REJECT",
"output": "ACCEPT",
"forward": "REJECT",
"masq": "1",
"mtu_fix": "1",
}
DELETE /cgi-bin/luci/sdewan/firewall/v1/zones/{zone-name}
delete a zone
Request:
Request Parameters
Name In Type Description zone-name path string zone name
Response
- Normal response codes: 200
- Error response codes: 401, 404
Redirect
...
{
"name":"default_rule",
"dest_ip": "0.0.0.0/0",
"policy": "balanced"
...
POST /cgi-bin/luci/sdewan/mwan3firewall/v1/ruleredirects
create a new ruleredirect
Request:
Request Parameters: same with GETPUT's response request
- Request Example: same with GETPUT's response example
Response
- Normal response codes: 201
- Error response codes: 400, 401
...
PUT /cgi-bin/luci/sdewan/mwan3firewall/v1/ruleredirects/{ruleredirect-name}
update a policyredirect
Request:
Request Parameters:
Request ExampleName In Type Description rule path string rule name
policy used for the ruleredirect-name path string redirect name src body string (Required for DNAT) traffic source zone src_ip body string Match incoming traffic from the specified source ip address. src_dip body string
ip(Required for SNAT) For DNAT, match incoming traffic directed at the given destination ip address. For SNAT rewrite the source address to the given address. src_
bodymac body string (optional) source ip address src_port body string (optional) source port or port range dest_ip body string (optional) destination ip address dest_port body string (optional) destination port or port range proto body string (optional) protocol for the rule. Valid values: "tcp", "udp", "icmp", "all" family body string (optional) address family. Valid values: "ipv4", "ipv6", "all" sticky body string (optional) default: 0, allow traffic from the same source ip address within the timeout limit to use same wan interface as prior session timeout body int (optional) default: 600, Stickiness timeout value in seconds {
"dest_ip": "0.0.0.0/0",
"policy": "balanced"
}
Response
- Normal response codes: 204
- Error response codes: 400, 401, 404
string Match incoming traffic from the specified mac address. src_port body port or range Match incoming traffic originating from the given source port or port range on the client host. src_dport body port or range For DNAT, match incoming traffic directed at the given destination port or port range on this host. For SNAT rewrite the source ports to the given value. proto body string Match incoming traffic using the given protocol. Can be one of tcp,udp,tcpudp,udplite,icmp,esp,ah,sctp, oralldest body string Specifies the traffic destination zone. Must refer to one of the defined zone names. dest_ip body string For DNAT, redirect matches incoming traffic to the specified internal host. For SNAT, it matches traffic directed at the given address. dest_port body port or range For DNAT, redirect matched incoming traffic to the given port on the internal host. For SNAT, match traffic directed at the given ports. mark body string match traffic against the given firewall mark target body string (Required) NAT target: SNAT, DNAT family body string Protocol family ( ipv4,ipv6orany) to generate iptables rules for- Request Example
PUT
...
/cgi-bin/luci/sdewan/mwan3/v1/
...
redirects/dnat_lan
{
...
delete a rule
Request:
Request Parameters
...
Response
- Normal response codes: 200
- Error response codes: 401, 404
Firewall
OpenWRT Firewall configuration includes below sections:
- Default: declares global firewall settings which do not belong to specific zones
- Include: used to enable customized firewall scripts
- Zone: groups one or more interfaces and serves as a source or destination for forwardings, rules and redirects.
- Forwarding: control the traffic between zones
- Redirect: defines port forwarding (NAT) rules
- Rule: defines basic accept, drop, or reject rules to allow or restrict access to specific ports or hosts.
SDEWAN CNF will be created with Default sections initialized. Include section will not be implemented in this release.
SD-EWAN Firewall API provides support to get/create/update/delete Firewall Zone, Redirect, Rule and Forwardings
Zone
"src":"wan",
"src_dport":"19900",
"dest":"lan",
"dest_ip":"192.168.1.1",
"dest_port":"22",
"proto":"tcp",
"target":"DNAT"}
Response
- Normal response codes: 204
- Error response codes: 400, 401, 404
GET /cgi-bin/luci/sdewan/firewall/v1/zonesredirects
Lists all defined zonesredirects
Request: N/A
Response
- Normal response codes: 200
Response Parameters
Name In Type Description zonesredirects body array a list of defined zonesredirects - Response Example
{
"zonesredirects": [{
"name":"dnat_lan",
"src":"wan",,
"networksrc_dport":"wan19900",,
"inputdest":"REJECTlan","output": "ACCEPT",
"forward": "REJECT",
"masq": "1",
"mtu_fix": "1"
,
"dest_ip":"192.168.1.1",
"dest_port":"22",
"proto":"tcp",
"target":"DNAT"}
]
}
GET /cgi-bin/luci/sdewan/firewall/v1/zoneredirects/{zoneredirect-name}
Get a zoneredirect
Request: N/A
- Normal response codes: 200
- Error response code: 404
Request Parameters
Name In Type Description zone path string zone name
Response
Response Parameters
Response Example
bodyName In Type Description redirect-name path string (Required) zone name network body array List of interfaces attached to this zone masq body boolean Specifies whether outgoing zone traffic should be masqueraded. "0" or "1" masq_src body string Limit masquerading to the given source subnets. masq_dest body string Limit masquerading to the given destination subnets masq_allow_invalid body boolean whether add DROP INVALIDrulesmtu_fix body boolean Enable MSS clamping for outgoing zone traffic input body string Default policy ( ACCEPT,REJECT,DROP) for incoming zone traffic.forward body string Default policy ( ACCEPT,REJECT,DROP) for forwarded zone traffic.output body string Default policy ( ACCEPT,REJECT,DROP) for output zone traffic.family body string The protocol family ( ipv4,ipv6orany) these iptables rules are for.subnet body string List of IP subnets attached to this zone extra_src body string Extra arguments passed directly to iptables for source classification rules. etra_dest body string Extra arguments passed directly to iptables for destination classification rules. {
"name":"wan",
"network":"wan",
"input": "REJECT",
"output": "ACCEPT",
"forward": "REJECT",
"masq": "1",
"mtu_fix": "1",
}
POST /cgi-bin/luci/sdewan/firewall/v1/zone
create a new zone
Request:
...
Request Parameters: same with GET's response request
...
Response
- Normal response codes: 201
- Error response codes: 400, 401
PUT /cgi-bin/luci/sdewan/firewall/v1/zone/{zone}
update a zone
Request:
Request Parameters:
...
{
"network":"wan",
"input": "REJECT",
"output": "ACCEPT",
"forward": "REJECT",
"masq": "1",
"mtu_fix": "1"
}
redirect name
Response
- Normal response codes: 200
- Error response code: 404
Response Parameters
Name In Type Description name body string (Required) forwarding name src body string (Required for DNAT) traffic source zone src_ip body string Match incoming traffic from the specified source ip address. src_dip body string (Required for SNAT) For DNAT, match incoming traffic directed at the given destination ip address. For SNAT rewrite the source address to the given address. src_mac body string Match incoming traffic from the specified mac address. src_port body port or range Match incoming traffic originating from the given source port or port range on the client host. src_dport body port or range For DNAT, match incoming traffic directed at the given destination port or port range on this host. For SNAT rewrite the source ports to the given value. proto body string Match incoming traffic using the given protocol. Can be one of tcp,udp,tcpudp,udplite,icmp,esp,ah,sctp, oralldest body string Specifies the traffic destination zone. Must refer to one of the defined zone names. dest_ip body string For DNAT, redirect matches incoming traffic to the specified internal host. For SNAT, it matches traffic directed at the given address. dest_port body port or range For DNAT, redirect matched incoming traffic to the given port on the internal host. For SNAT, match traffic directed at the given ports. mark body string match traffic against the given firewall mark target body string (Required) NAT target: SNAT, DNAT family body string Protocol family ( ipv4,ipv6orany) to generate iptables rules for- Response Example
{
"name":"dnat_lan",
"src":"wan",
"src_dport":"19900",
"dest":"lan",
"dest_ip":"192.168.1.1",
"dest_port":"22",
"proto":"tcp",
"target":"DNAT"}
DELETE
Response
- Normal response codes: 204
- Error response codes: 400, 401, 404
DELETE /cgi-bin/luci/sdewan/firewall/v1/zone/{zone}
delete a zone
Request:
Request Parameters
...
Response
- Normal response codes: 200
- Error response codes: 401, 404
Redirect
GET /cgi-bin/luci/sdewan/firewall/v1/redirectsLists all defined redirects
Request: N/A
Response
/{redirect-name}
delete a redirect rule
Request:
Request
- Normal response codes: 200
Response Parameters
redirectsName In Type Description
bodyredirect-name path array a list of defined redirectsstring redirect name
Response
...
- Normal response codes: 200
- Error response codes: 401, 404
Rule
POST /cgi-bin/luci/sdewan/firewall/v1/rules
create a new rule
Request:
Request Parameters: same with PUT's request
- Request Example: same with PUT's example
Response
- Normal response codes: 201
- Error response codes: 400, 401
PUT
...
{
"redirects": [
{
"name":"DNAT-LAN",
"src":"wan",
"src_dport":"19900",
"dest":"lan",
"dest_ip":"192.168.1.1",
"dest_port":"22",
"proto":"tcp",
"target":"DNAT"
}
]
}
GET /cgi-bin/luci/sdewan/firewall/v1/redirectrules/{redirectrule-name}
Get update a redirectrule
Request: N/A
- Normal response codes: 200 Error response code
Request Parameters
Name In Type Description redirect path string redirect name
Response
:
404Response Parameters
Response Example
bodyName In Type Description rule-name
(Required) forwarding namepath string
for DNATrule name src body string (Required
.) traffic source zone src_ip body string Match incoming traffic from the specified source ip address
dipsrc_ mac body string (Required for SNAT) For DNAT, match incoming traffic directed at the given destination ip address. For SNAT rewrite the source address to the given address. src_mac body string
mac address.Match incoming traffic from the specified src_port body port or range Match incoming traffic originating from the given source port or port range on the client host.
dportmac address src_
For DNAT, matchport body port or range
directed at the given destinationMatch incoming traffic
on this host. For SNAT rewrite the source ports to the given value.from the specified source port or port range
Specifies theproto body string Match incoming traffic using the given protocol. Can be one of tcp,udp,tcpudp,udplite,icmp,esp,ah,sctp, orallicmp_type body string For protocol icmpselect specific icmp types to match.dest body string
.traffic destination zone. Must refer to one of the defined zone names
For DNAT, redirect matches incoming traffic to the specified internal host. For SNAT, it matches traffic directed at the given address., or * for any zone dest_ip body string
bodyMatch incoming traffic directed to the specified destination ip address dest_port
For DNAT, redirect matched incoming traffic to the given port on the internal host. For SNAT, matchbody port or range
ports.Match incoming traffic directed at the given
NAT target: SNAT, DNATdestination port or port range mark body string If specified, match traffic against the given firewall mark target body string (Required) family body string Protocol family ( ipv4,ipv6orany) to generate iptables rules for{
"name":"DNAT-LAN",
"src":"wan",
"src_dport":"19900",
"dest":"lan",
"dest_ip":"192.168.1.1",
"dest_port":"22",
"proto":"tcp",
"target":"DNAT"}
POST /cgi-bin/luci/sdewan/firewall/v1/redirect
create a new redirect
Request:
...
Request Parameters: same with GET's response request
Firewall action ( ACCEPT,REJECT,DROP,MARK,NOTRACK) for matched trafficset_mark body string Zeroes out the bits given by mask and ORs value into the packet mark. set_xmark body string Zeroes out the bits given by mask and XORs value into the packet mark family body string Protocol family ( ipv4,ipv6orany) to generate iptables rules forextra body string Extra arguments to pass to iptables. Useful mainly to specify additional match options, such as -m policy --dir infor IPsec.- Request Example
PUT
...
Response
- Normal response codes: 201
- Error response codes: 400, 401
...
/cgi-bin/luci/sdewan/
...
mwan3/v1/
...
update a redirect
Request:
rules/reject_lan_80
{
"src
Request Parameters:
Name In Type Description redirect path string redirect name {other params} body same with GET response Request Example{
"src":"wan",
"src_dport":"19900",
"dest
,":"lan"
,
dest"
1src_ip": "192.168.1.
2",
dest"
22src_port": "
80",
"proto":"tcp",
DNAT"target":"
REJECT"
}
Response
- Normal response codes: 204
- Error response codes: 400, 401, 404
DELETE /cgi-bin/luci/sdewan/firewall/v1/redirect/{redirect}
delete a redirect rule
Request:
Request Parameters
...
Response
- Normal response codes: 200
- Error response codes: 400, 401, 404
...
GET /cgi-bin/luci/sdewan/firewall/v1/rules
...
- Normal response codes: 200
Response Parameters
Name In Type Description rules body array a list of defined rules - Response Example
REJECT{
"rules": [{
"name":"
LANreject_
lan_80"
"src":"lan",
"src_ip": "192.168.1.2",
"src_port": "80",
"proto":"tcp",
"target":"REJECT"
}
]
}
GET /cgi-bin/luci/sdewan/firewall/v1/rulerules/{rule-name}
Get a rule
Request: N/A
Request Parameters
Name In Type Description rule-name path string rule name
Response
- Normal response codes: 200
- Error response code: 404
Response Parameters
Response ExampleName In Type Description name body string (Required) rule name src body string (Required) traffic source zone src_ip body string Match incoming traffic from the specified source ip address src_mac body string (Required) forwarding name src body string (Required) traffic source zone dest body string (Required) traffic destination zone family body string Protocol family ( ipv4,ipv6orany) to generate iptables rules for.{
"name":"REJECT_LAN_80"
"src":"lan",
"src_ip": "192.168.1.2",
"src_port": "80",
"proto":"tcp",
"target":"REJECT"
}
POST /cgi-bin/luci/sdewan/firewall/v1/rule
create a new rule
Request:
...
Request Parameters: same with GET's response request
string Match incoming traffic from the specified mac address src_port body port or range Match incoming traffic from the specified source port or port range proto body string Match incoming traffic using the given protocol. Can be one of tcp,udp,tcpudp,udplite,icmp,esp,ah,sctp, orallicmp_type body string For protocol icmpselect specific icmp types to match.dest body string traffic destination zone. Must refer to one of the defined zone names, or * for any zone dest_ip body string Match incoming traffic directed to the specified destination ip address dest_port body port or range Match incoming traffic directed at the given destination port or port range mark body string If specified, match traffic against the given firewall mark target body string (Required) Firewall action ( ACCEPT,REJECT,DROP,MARK,NOTRACK) for matched trafficset_mark body string Zeroes out the bits given by mask and ORs value into the packet mark. set_xmark body string Zeroes out the bits given by mask and XORs value into the packet mark family body string Protocol family ( ipv4,ipv6orany) to generate iptables rules forextra body string Extra arguments to pass to iptables. Useful mainly to specify additional match options, such as -m policy --dir infor IPsec.- Response Example
{
"name":"reject_lan_80"
...
Response
- Normal response codes: 201
- Error response codes: 400, 401
PUT /cgi-bin/luci/sdewan/firewall/v1/rule/{rule}
update a rule
Request:
- Normal response codes: 204 Error response codes: 400, 401, 404
Request Parameters:
Name In Type Description rule path string rule name {other params} body same with GET response Request Example{"src":"lan",
"src_ip": "192.168.1.2",
"src_port": "80",
"proto":"tcp",
"target":"REJECT"
}
Response
DELETE /cgi-bin/luci/sdewan/firewall/v1/rulerules/{rule-name}
delete a firewall rule
Request:
Request Parameters
Name In Type Description rule-name path string rule name
Response
- Normal response codes: 200
- Error response codes: 401, 404
Forwarding
GET POST /cgi-bin/luci/sdewan/firewall/v1/forwardings
Lists all defined forwardings
...
create a new forwarding
Request:
Request Parameters: same with PUT's request
- Request Example: same with PUT's example
Response
- Normal response codes: 201
- Error response codes: 200: 400, 401
PUT /cgi-bin/luci/sdewan/firewall/v1/forwardings/{forwarding-name}
update a forwarding
Request:
Request Parameters:Response Parameters
Name In Type Description forwarding-name path string forwarding name src body string (Required) traffic source zone dest body string (Required) traffic destination zone familyforwardings body array a list of defined forwardings string Protocol family ( ipv4,ipv6orany) to generate iptables rules for.- Request Example
PUT /cgi-bin/luci/sdewan/mwan3/v1/forwardings/lan_wan
Response Example{
{
"forwardings": [{
"name":"lan-wan",
"src":"lan",
"dest": "wan"
}
]
}
Response
- Normal response codes: 204
- Error response codes: 400, 401, 404
GET /cgi-bin/luci/sdewan/firewall/v1/forwarding/{forwarding}
Get a forwarding
Request: N/A
/forwardings
Lists all defined forwardings
Request: N/A
Request Parameters
...
Response
- Normal response codes: 200Error response code: 404
Response Parameters
nameName In Type Description forwardings body string (Required) forwarding name src body string (Required) traffic source zone dest body string (Required) traffic destination zone family body string Protocol family ( ipv4,ipv6orany) to generate iptables rules for.array a list of defined forwardings - Response ExampleResponse Example
{
"forwardings": [{
{
"name":"lan-_wan",
"src":"lan",
"dest": "wan"
}
POST /cgi-bin/luci/sdewan/firewall/v1/forwarding
create a new forwarding
Request:
...
Request Parameters: same with GET's response request
}
]
}
GET
...
Response
- Normal response codes: 201
- Error response codes: 400, 401
PUT /cgi-bin/luci/sdewan/firewall/v1/forwardingforwardings/{forwarding-name}
update Get a forwarding
Request: N/A
Request Parameters
Name In Type Description forwarding-name path string forwarding name
Response
- Normal response codes: 200
- Error response code: 404
Response Parameters
Name In Type Description forwarding path string forwarding name {other params} body same with GET response name body string (Required) forwarding name src body string (Required) traffic source zone dest body string (Required) traffic destination zone family body string Protocol family ( ipv4,ipv6orany) to generate iptables rules for.- Response ExampleRequest Example
{
"name":"lan_wan",
{
"src":"lan",
"dest": "wan"
}
Response
- Normal response codes: 204 Error response codes: 400, 401, 404
DELETE /cgi-bin/luci/sdewan/firewall/v1/forwardingforwardings/{forwarding-name}
delete a forwarding rule
...
Request Parameters
Name In Type Description forwarding-name path string forwarding name
...