Table of Contents
Introduction
The guide covers the installation details which are related to Enterprise Applications on Lightweight 5G Telco Edge (EALTEdge) Blueprint.
...
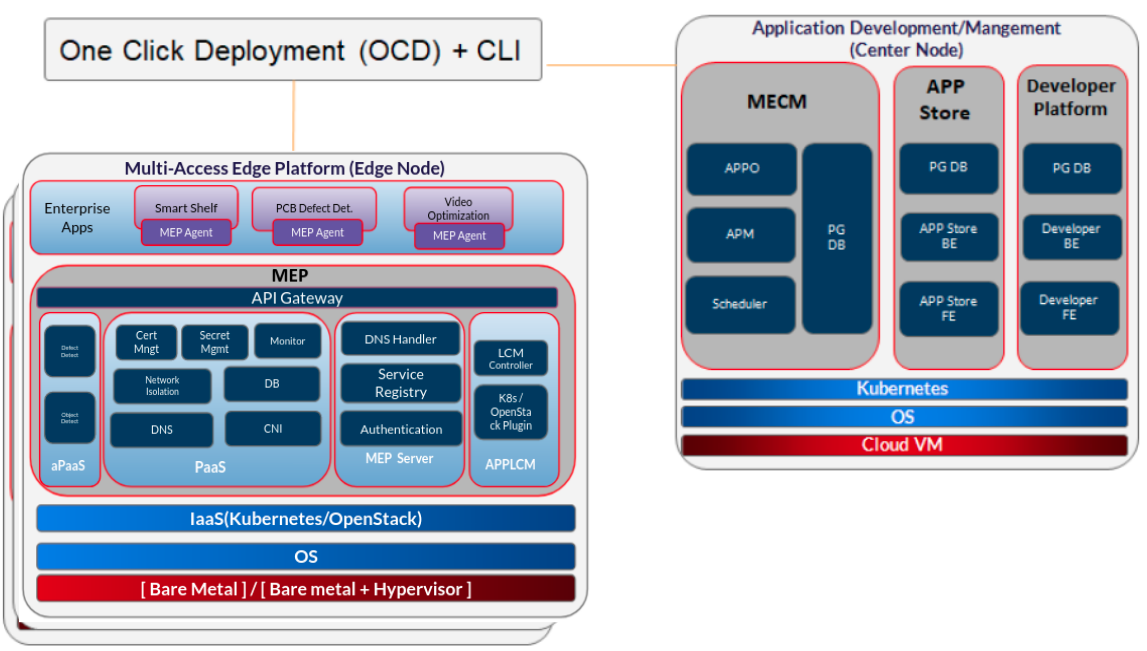
The CENTER Node is a K8s Cluster and EDGE Node is a K3s K8s Cluster.
How to use this document
...
Note: For Development environment two nodes is sufficient, where one node plays a dual role of One-Click Deployment Node and MECM Node with other as MEC Host.
Figure: EALTEdge Deployment Architecture
Note: EALTEdge Blueprint Deployment has been tested on Cloud VM and is not tested on Bare-Metal Environment. Though, theoretically deployment should work in bare metal, provided hardware and software prerequisites are met. Kindly refer R4 R5 - Test Documentation of Enterprise Applications on Lightweight 5G Telco Edge (EALTEdge) to get details on the tested deployment.
...
- Virtual Machines preinstalled with Ubuntu 16.04 / 18.04 for MECM Node.
- Virtual Machines preinstalled with Ubuntu 16.04 / Ubuntu 18.04 or CentOS 7.X for MEC Host Nodes
- root user created in the Deployment Node, MEC Node and MEC Host Node.
- SSH Server running in all the Nodes.
- Ansible > 2.10.5 7 installed in One Click Deployment Node (Jump Host)
- git installed in Jump Host.
- Kubespray code is downloaded (https://github.com/kubernetes-sigs/kubespray.git)
- GO Lang (version greater than 1.14.2) installed in Jump Host, required for CLI.
Database Prerequisites
Schema scripts
N/A
Other Installation Requirements
Jump Host Requirements
Database Prerequisites
Schema scripts
N/A
Other Installation Requirements
Jump Host Requirements
Network Requirements
- Internet connectivity in OCD Host, CENTER and EDGE Nodes.
- The CENTER Node and EDGE Node should be able to ping each other.
...
For Virtual Deployment minimum three2 Virtual machines(OCD and Center node can be deploy on same VM or in different VMs), following are the virtual machines and their usage
...
All the nodes should have internet connectivity , network interface and network connectivity between the VM's.
Standard Deployment Overview
...
Login to the Jump Host and perform the below steps:
- Install Ansible > 2.910.6 7 [ https://docs.ansible.com/ansible/latest/installation_guide/intro_installation.html]
- Install git
- Install GoLang > 1.14+
- Git clone the Kubespray repo. [https://github.com/kubernetes-sigs/kubespray.git]
- Install python3 and pip3
- cd kubespray && pip install -r requirements.txt
- python3 and pip3
Jump Jump Host Pre-Configurations for Center Components Installation
...
1. Generate public key : #ssh-keygen -t rsa
2. Setup password-less login from ocd to center and ocd to edge.
sshpass -p <password> Copy the ssh key to all the nodes in the MECM Cluster, using ssh-copy-id . (example : #ssh-copy-id root@159.178.17.16)
3. Kubespray configuration
cd kubespray && cp -rfp inventory/sample inventory/mycluster
Update ansible inventory file provided in kubesrpay repo with MECM Cluster node IP's
4. Review and Change Parameters
cat inventory/mycluster/group_vars/all/all.yml
cat inventory/mycluster/group_vars/k8s-cluster/k8s-cluster.yml
Installing Mode : EALTEdge using Ansible-Playbooks
1. git clone the ealt-edge repo, to download the software to install the EALTEdge Environment.
root@akraino-mec-0002:~# git clone "https://gerrit.akraino.org/r/ealt-edge"
2. go to the below directory
root@akraino-mec-0002:~# cd ealt/infra/playbooks
3. Modify the Configuration File : ealt-inventory.ini with the details of CENTER and EDGE Nodes.
root@akraino-mec-0002:~# vi ealt-inventory.ini
4. Execute the below command
**Setup environment -
root@akraino-mec-0002:~# ansible-playbook ealt-all.yml -i ealt-inventory.ini --extra-vars "operation=install"
Once the execution is completed in console will see prompt "EALTEdge Environment Installed , Components Install CENTER and EDGE Nodes Successfully"
Other Options:
-p <ssh-port> -o StrictHostKeyChecking=no root@<node_ip>
3. Review and Change Parameters
For EdgeGallery MUNO Mode
ealt-edge/ocd/infra/playbooks/muno-config/controller/hosts-muno-controller
ealt-edge/ocd/infra/playbooks/muno-config/controller/var.yml
ealt-edge/ocd/infra/playbooks/muno-config/edge/hosts-muno-edge
ealt-edge/ocd/infra/playbooks/muno-config/edge/var.yml
For EdgeGallery AIO Mode
ealt-edge/ocd/infra/playbooks/hosts-aio
ealt-edge/ocd/infra/playbooks/var.yml
For EALT-EDGE stack:
ealt-edge/ocd/infra/playbooks/ealt-inventory.ini
Installing Mode : EALTEdge using Ansible-Playbooks
1. git clone the ealt-edge repo, to download the software to install the EALTEdge Environment.
root@akraino-mec-0001:~# git clone "https://gerrit.akraino.org/r/ealt-edge"
2. go to the below directory
root@akraino-mec-0001:~# cd ealt-edge/ocd/infra/playbooks
3. Modify the Configuration File :
ealt-inventory.ini with the details of CENTER and EDGE Nodes.
For Edge Gallery installation:
MUNO-Mode:
Execute the below command:
cd ealt-edge/ocd/infra/playbooks
ansible-playbook -i muno-config/controller/hosts-muno-controller ealt-eg-muno-controller.yml To Install only Edge node
root@akraino-mec-0002:~# ansible-playbook ealt-all.yml -i ealt-inventory.ini --tags "edge" --extra-vars "operation=install"
Snapshot Deployment Overview
Not Applicable
Special Requirements for Virtual Deployments
N/A
Install Jump Host
N/A
Verifying the Setup - VM's
N/A
Upstream Deployment Guide
Upstream Deployment Key Features
N/A
Special Requirements for Upstream Deployments
N/A
Scenarios and Deploy Settings for Upstream Deployments
N/A
Including Upstream Patches with Deployment
N/A
Running
N/A
Interacting with Containerized Overcloud
N/A
Verifying the Setup
Verifying EALTEdge Deployment
Currently the verification is manually done.
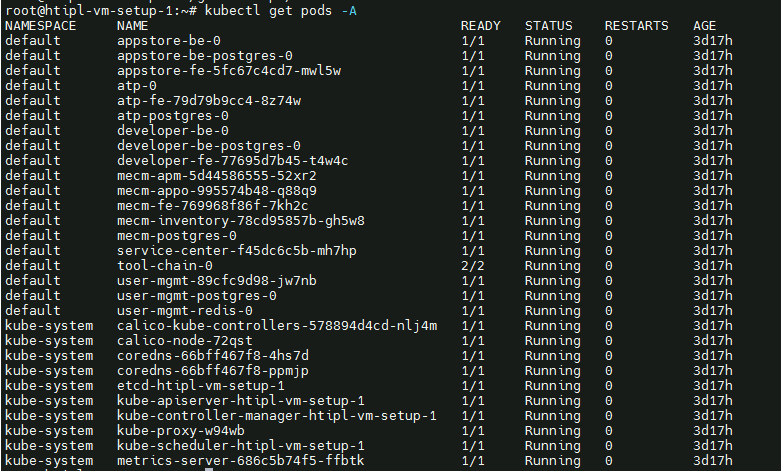
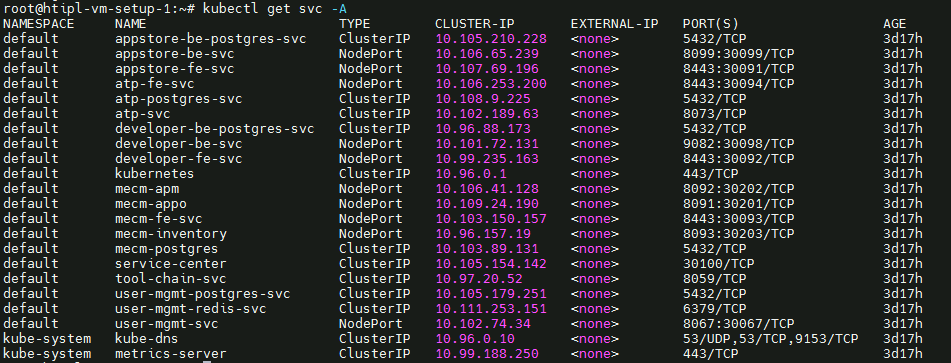
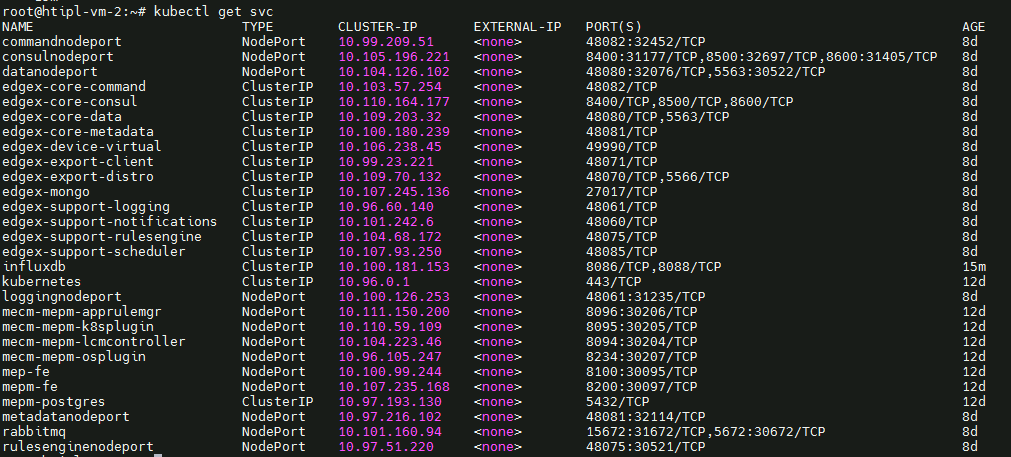
- Login to the Center Node and check whether K8S cluster is installed.
- Check the below mentioned components and services are running as Pods / Services in Kubernetes cluster
- PostgresSQL
- AppLCM
- Appo
- Inventory
- Apm
- MECM - FrontEnd
- Appstore
- Developer Portal
- Service Center
- User Management
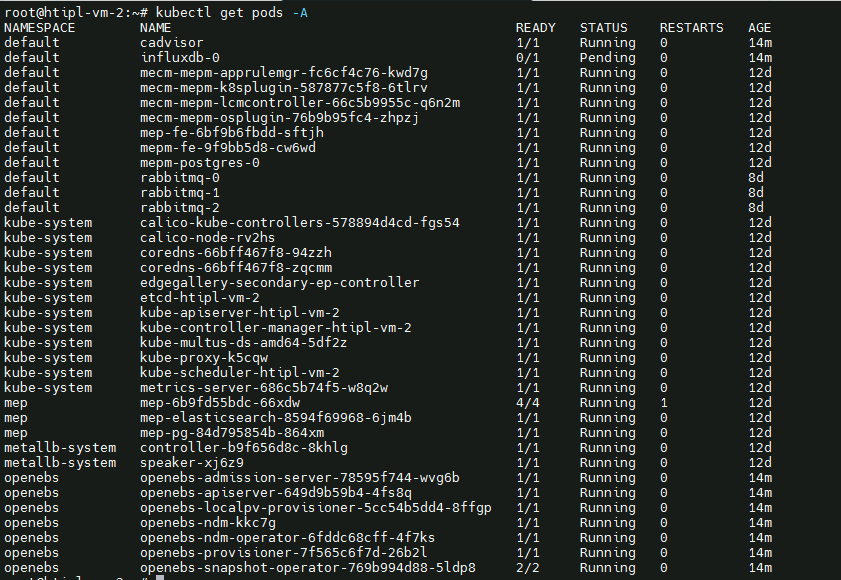
- Login to Edge Host and check K3S is installed.
Components and Services running in CENTER Node
Components and Services running EDGE Node
Developer Guide and Troubleshooting
Uninstall Guide
Using Ansible Playbooks
-e "ansible_user=root"
ansible-playbook -i muno-config/edge/hosts-muno-edge ealt-eg-muno-edge.yml --extra-vars "operation=install" -e "ansible_user=root"
For AIO mode:
Execute the below command
cd ealt-edge/ocd/infra/playbooks
ansible-playbook ealt-eg-aio-latest.yml -i hosts-aio --extra-vars "operation=install" -e ansible_user=root"
Installation of ealt-edge stack:
ansible-playbook ealt-all.yml -i ealt-inventory.ini --extra-vars "operation=install"
Once the execution is completed in console will see prompt "EALTEdge Environment Installed , Components Install CENTER and EDGE Nodes Successfully"
Snapshot Deployment Overview
N/A
Special Requirements for Virtual Deployments
N/A
Install Jump Host
N/A
Verifying the Setup - VM's
N/A
Upstream Deployment Guide
Upstream Deployment Key Features
N/A
Special Requirements for Upstream Deployments
N/A
Scenarios and Deploy Settings for Upstream Deployments
N/A
Including Upstream Patches with Deployment
N/A
Running
N/A
Interacting with Containerized Overcloud
N/A
Verifying the Setup
Verifying EALTEdge Deployment
Currently the verification is manually done.
- Login to the Center Node and check whether K8S cluster is installed.
Components and Services running in CENTER Node
Components and Services running EDGE Node
Deploy Application in EALTEdge
- Login to MECM Portal https://ip:30093
1.1 click on Systems ->App LCM ->New Registration
Name: Applcm(any general name)
IP: applcm"public ip"
Port: 30204
1.2. click on Systems ->App Rule -> New Registration
Name: Apprule(any general name)
IP: applcm"public ip"
Port: 30206
1.3. click on Systems ->App Store ->New Registration
App Store Name: appstore(any general name)
IP: Appstore public ip
Port: 30099
Appstore Repo: {HarborIP:443}(192.168.1.1:443)
Repo Name: appstore(any general name)
Repo Username: admin(harbor user name)
Repo Password: Harbor@edge(harbor password)
Vendor: vendor(any general name)
2. log in to MECM Portal https://ip:30093
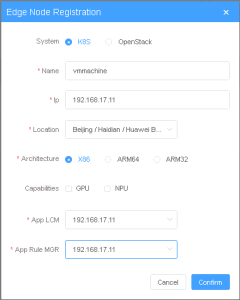
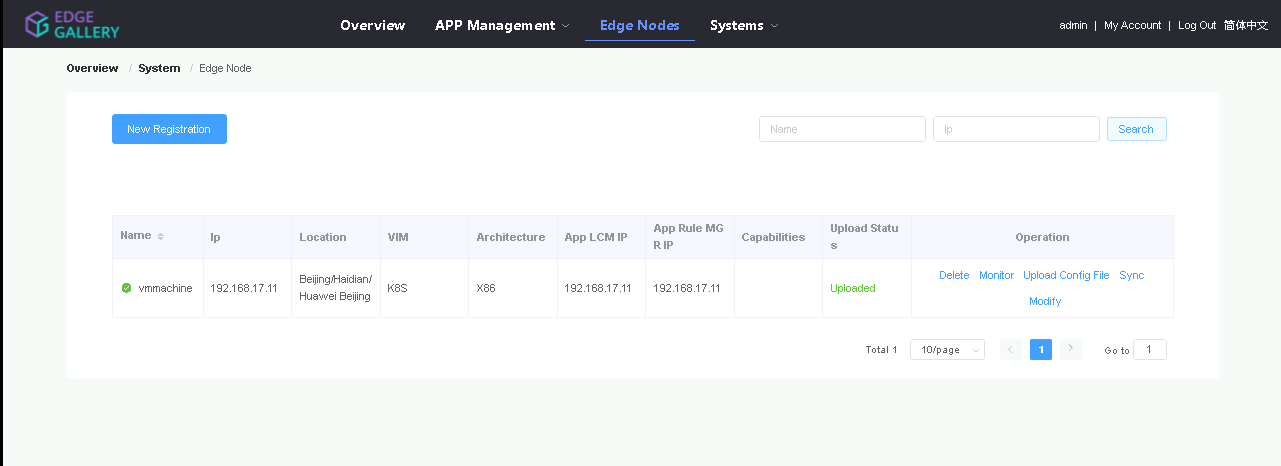
2.1. Add k8s node:
Click on Edge Nodes ->New Rgistration
System: k8s
Name: edge1(any general name)
IP: edge public IP
Location: Select from the drop-down
Architecture: x86
Capabilities: select none
App LCM: Select edge IP from the drop-down box
App Rule MGR: Select edge IP from the drop-down box
2.2. Download /root/.kube/config file from edge node
And click on Upload config file to upload.
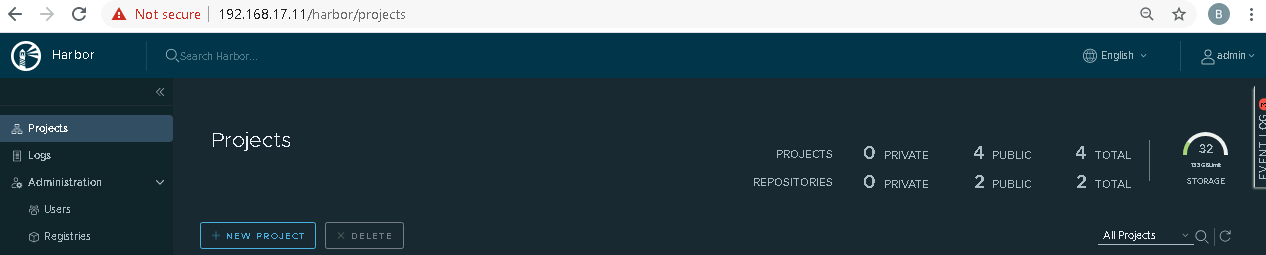
3. log in to harbor Portal https://ip:443
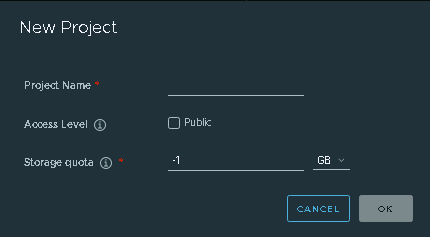
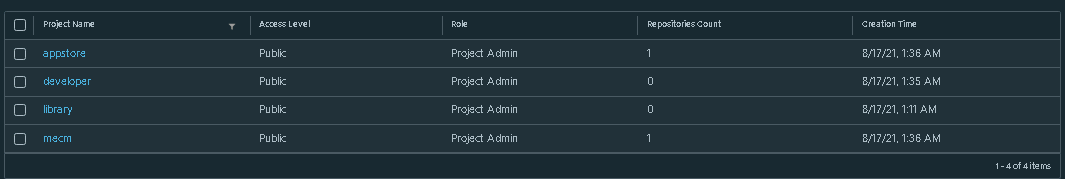
3.1. Add three new projects
3.2. Those three projects' names are appstore, developer, and mecm. And select access level to the public.
3.3. Final page will look like the below screenshot.
4. log in to Developer Portal https://ip:30092
4.1. Add sandbox env to deploy application before publishing
Click System ->Host Management ->Add Host
.
Name: general name
System: k8s
Lcmip: sandbox ip(for testing purpose can provide edge ip, if no sandbox env)
mecHost: sandbox ip(for testing purpose can provide edge ip, if no sandbox env)
Port: 30204
Protocol: https
Architecture: X86
Status: Normal
Port Range: leave as it is
Address: Bangalore
UploadConfig File: upload sandboxenvkubeconfig file
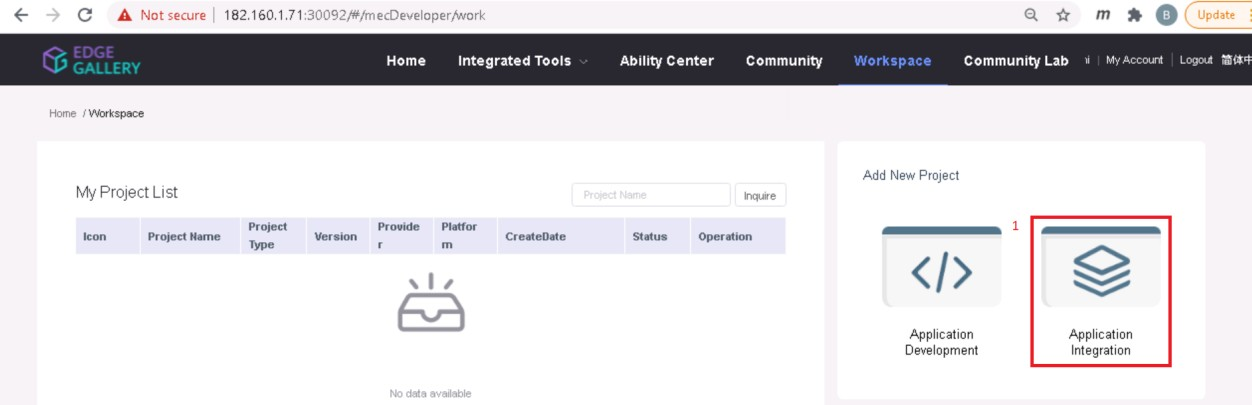
4.2 Click on Workspace -> Create Project -> Application Integration -> Start
- Go to Application Integration
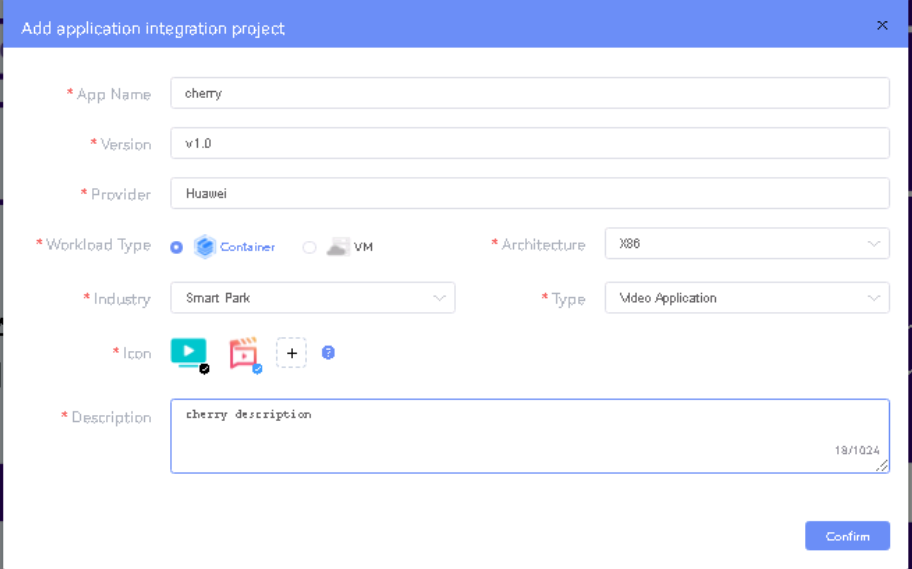
- Provide App Name, Version, Provider, Workload Type, Architecture, Industry, Type.
- Upload Icon, provide Description. And click on confirm.
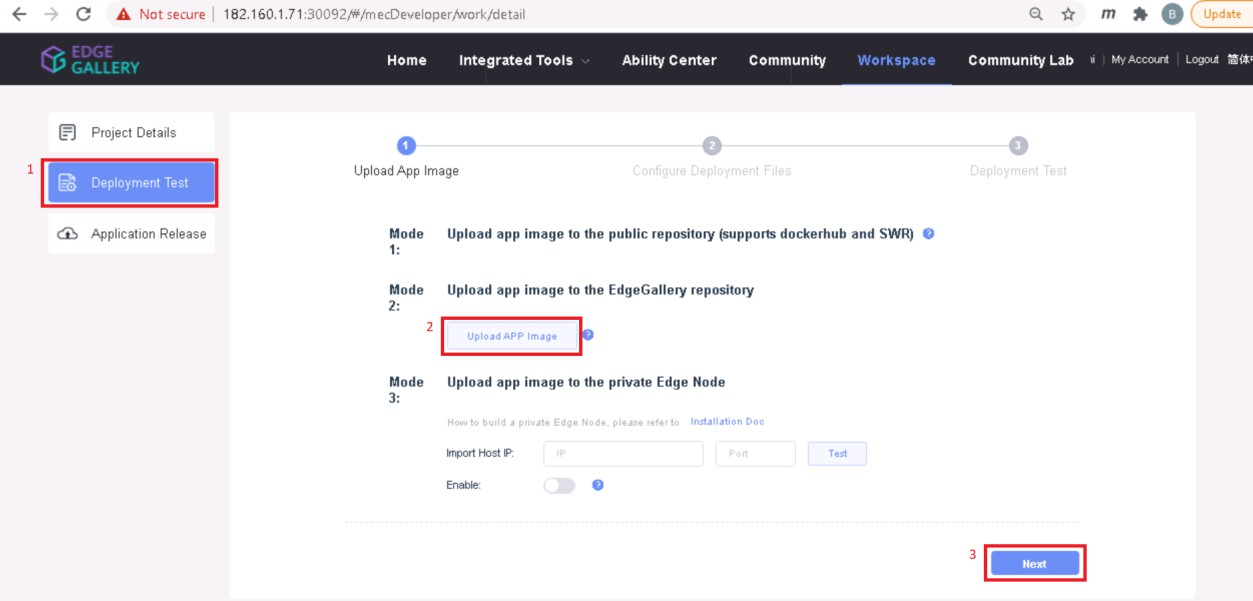
4.3. Now click on Deployment Test.
- Upload Docker images directly from the portal by clicking on Upload App Image.
- docker save -o <path-to-save>/<repo-name>.tar <repo-name>:<tag>
After that you can take tar file from path and upload image.
Or, directly push Docker images to Harbor repo (takes lesser time, preferred). Following command for pushing an image in Harbor:
- cat /etc/docker/daemon.json (execute this command in Edge gallery installed machine, to get an IP)
- docker tag <repo-name>:<tag> <IP>/developer/<repo-name>:<tag>
- docker push <IP>/developer/<repo-name>:<tag>
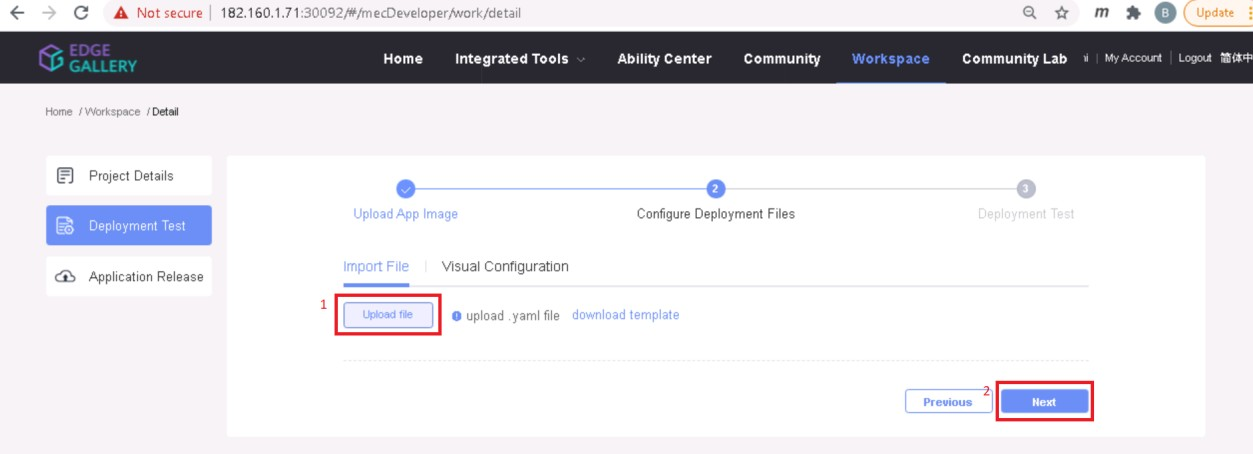
- Click next, upload deployment yaml file now.
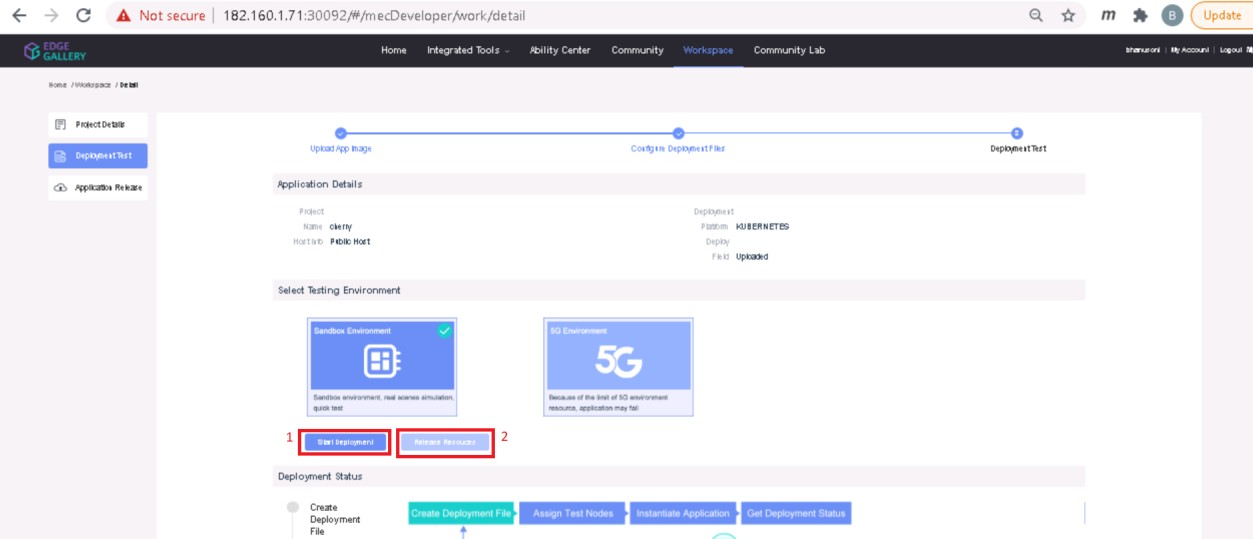
- After config upload, click next and click start deployment
- After Deployment is successful, click on Release Recourses
Note:
- While Deployment test if any error happens, open ATP portal (https://ip:30094) in another tab of the browser, sign in, come back to the developer portal and re run deployment test
- gitee.com/edgegallery/applications repo provides A lot of applications with their logo, deployment YAML & user guides
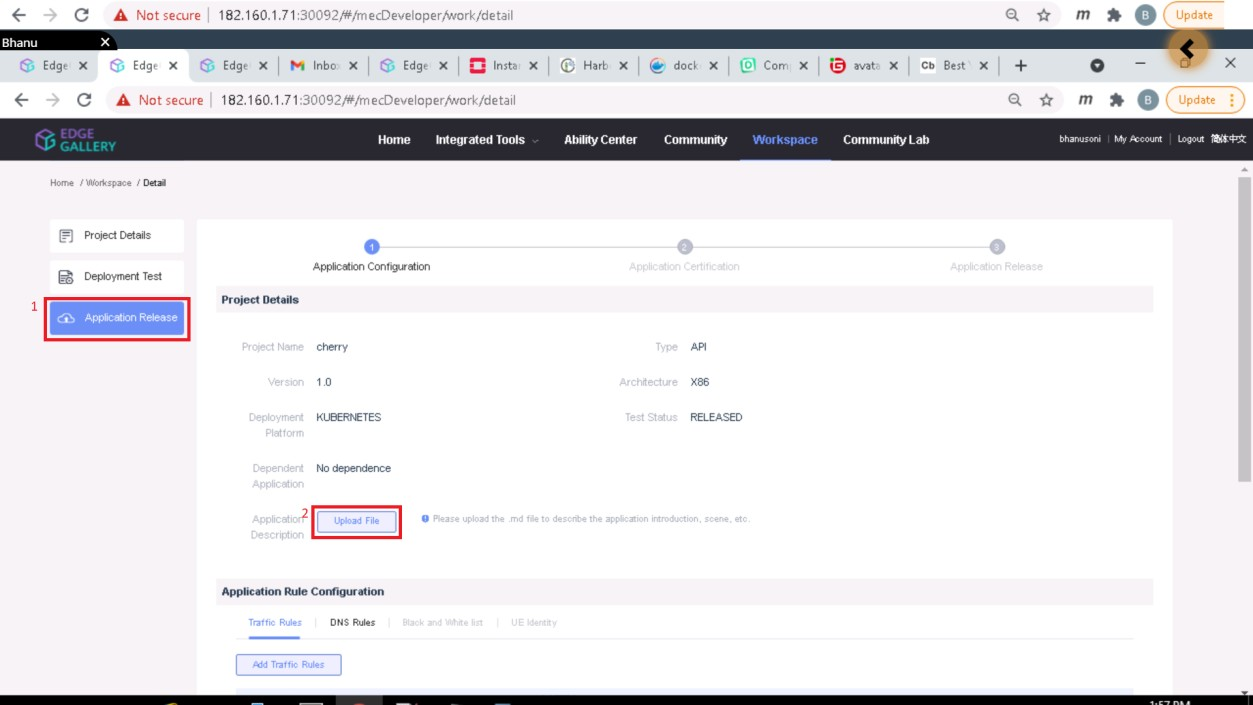
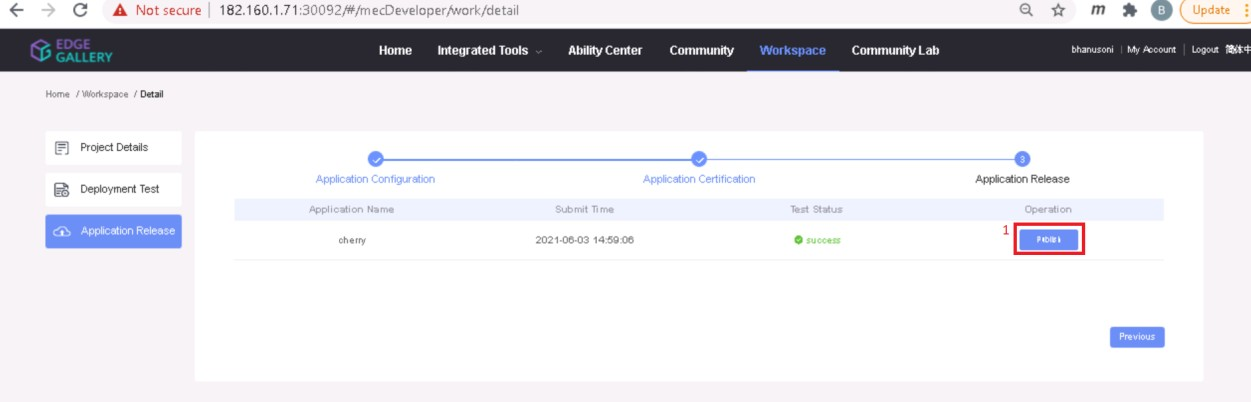
3.4. Now click on Application Release
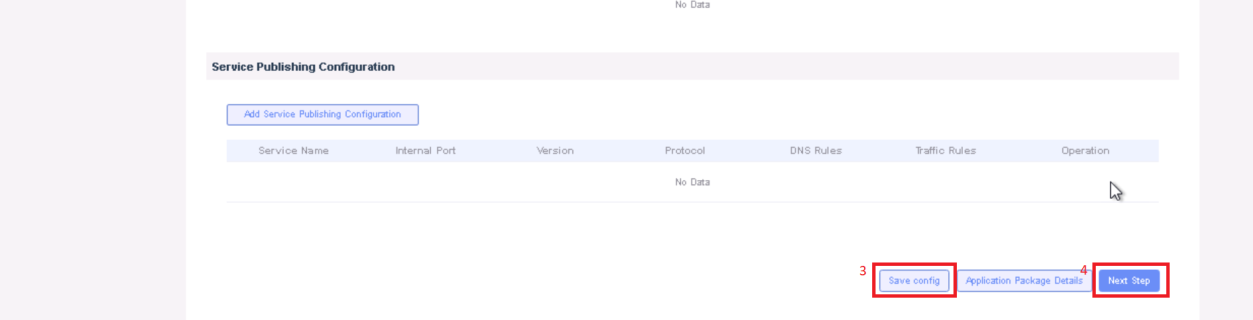
Upload file for Application Description
Click save config
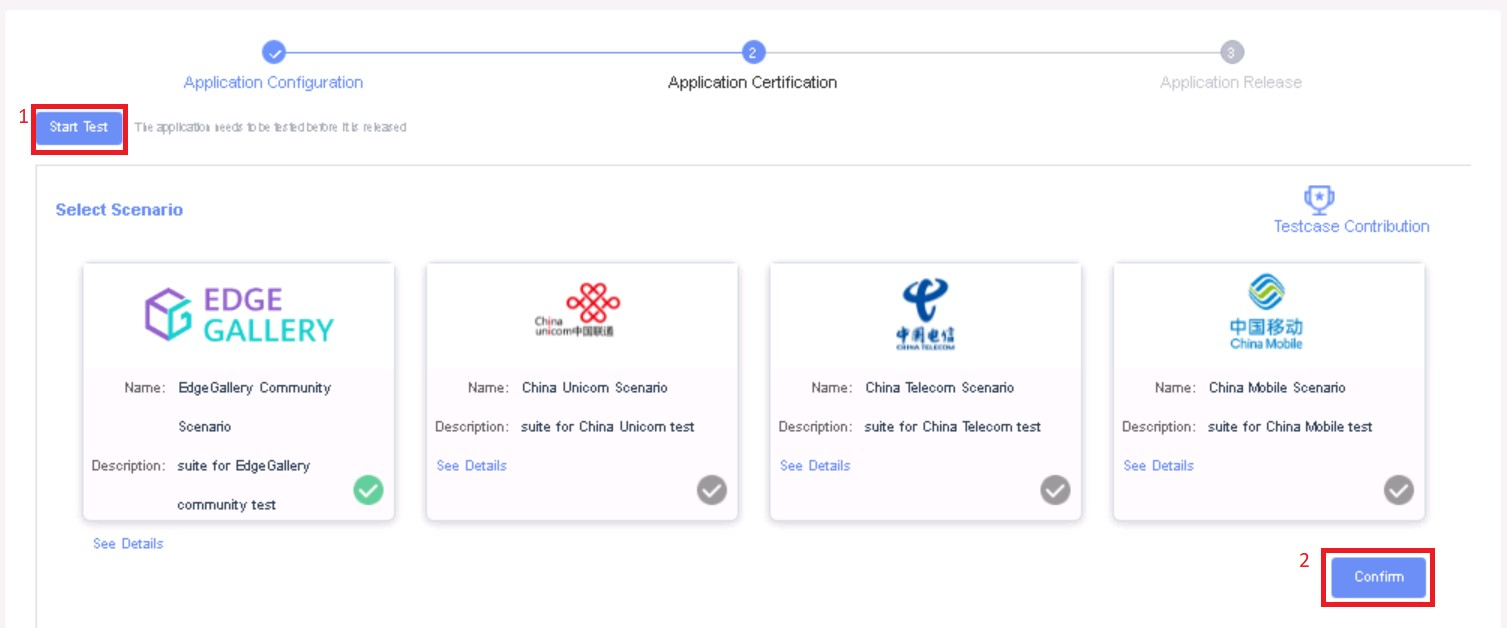
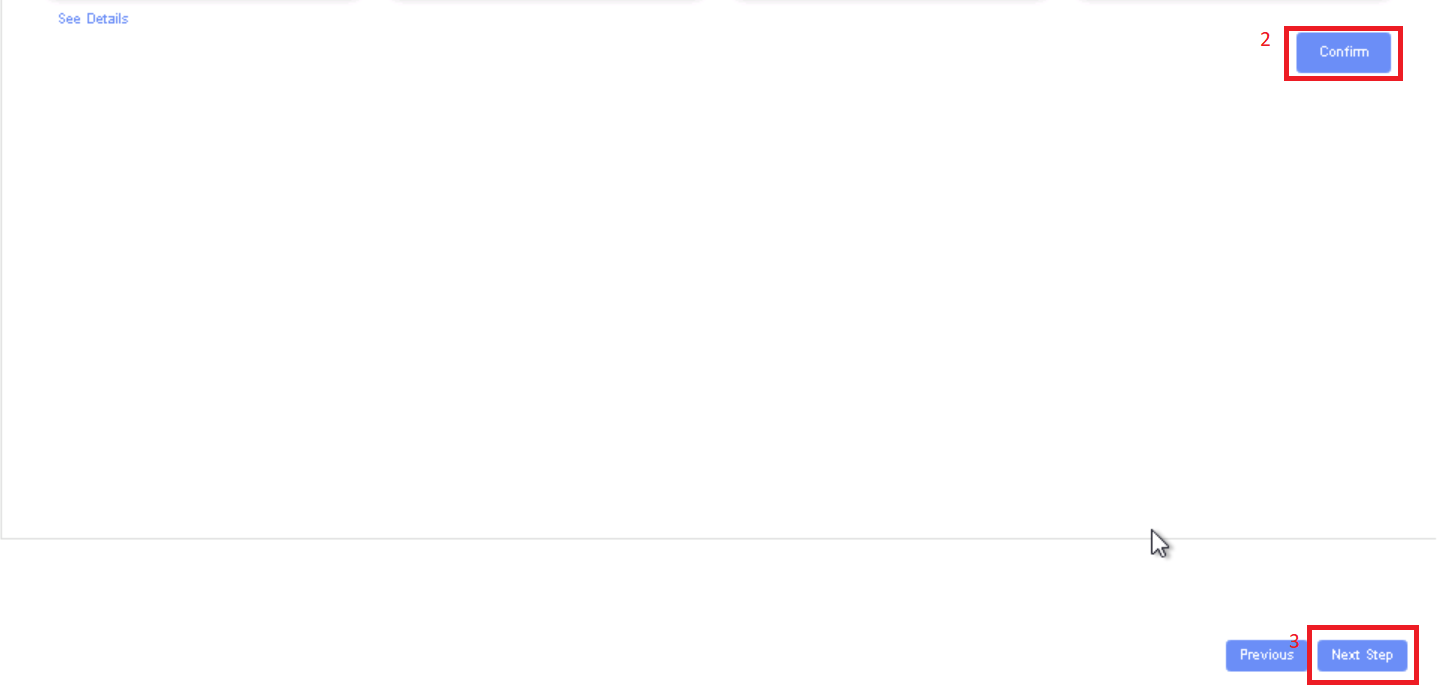
Click Next Step, click Start Test, scroll down to find & click the Start Test button, then confirm. Once the testing is complete click on Next Step
click publish to publish an application to AppStore. Go to https://<IP>:30091 and App Warehouse to confirm that the application is successfully ported.
Developer Guide and Troubleshooting
Uninstall Guide
Using Ansible Playbooks
For EALT-EDGE stack
root@akraino-mec-0001:~#ansible-playbook ealt-all-uninstall.yml -i ealt-inventory.ini --extra-vars "operation=uninstall"
For MUNO Mode
root@akraino-mec-0001:~#ansible-playbook -i muno-config/controller/hosts-muno-controller ealt-eg-muno-controller.yml --extra-vars "operation=uninstall" -e "ansible_user=root"
root@akraino-mec-0001:~#ansible-playbook -i muno-config/edge/hosts-muno-edge ealt-eg-muno-edge.yml root@akraino-mec-0002:~#ansible-playbook ealt-all-uninstall.yml -i ealt-inventory.ini --extra-vars "operation=uninstall" -e "ansible_user=root"
For AIO Mode
root@akraino-mec-00020001:~#ansible-playbook ealt -all-uninstall.yml -i ealt-inventory.ini --tags "edge" i hosts-aio ealt-eg-aio-latest.yml --extra-vars "operation=uninstall" -e "ansible_user=root"
Vault documentation
**This document explains how to generate certificate by using vault and cert manager**
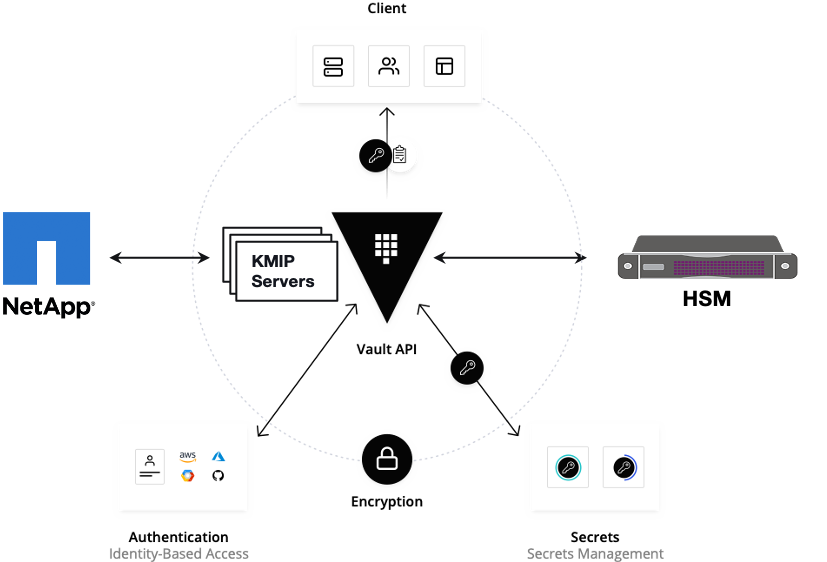
##Cluster Architecture

##Make a cluster
##The Image try to put with reference to our environment, with reference to EALT Edge. Can make a picture where Vault will be running in MEC Host (as Root CA) , ##Cert Manager and Applications (App1, App2)
##1. Add helm repo
```
helm repo add hashicorp https://helm.releases.hashicorp.com
helm install vault hashicorp/vault
```
##2. Generate root token and Unseal Key
```
kubectl exec vault-0 -- vault operator init -key-shares=1 -key-threshold=1 -format=""
```
##Note: Root token we will use when we will login vault pod, Unseal Key and Root token will looks like below ex-
##Unseal Key 1: QcTX47IacKidIjFWSrkGLiQG1fwaqoInEz0SqAZ7rMs=
##Initial Root Token: s.A0SXgscZxbCeJRd1AjsVzvUU
...
##Now get ca certificate use below command
```
curl http://10.43.130.35:8200/v1/pki/ca/pem
```
##10.43.130.35 is your vault ip, need to replace with latest vault ip
Troubleshooting
Error Message Guide
Error: Most of mecm-pods down state including service center pod,
In service center pod logs , "decryption password incorrect" issue
Solution: Please use common_pwd in config.yaml as te9Fmv%qaq
N/A
Maintenance
Blueprint Package Maintenance
...
| S. No | Software | Type | Version | License Information | Remarks |
| 1. | Docker | CRI | 18.09 | Apache 2.0 license | No code modifications done |
| 2. | K8s | Orchestration | 1.18.7+ | Apache 2.0 license | No code modifications done |
| 3. | Edge Gallery | Opensource MEC platform | 1.1.1 | Apache 2.0 license | Open Source MEC Platform |
...