...
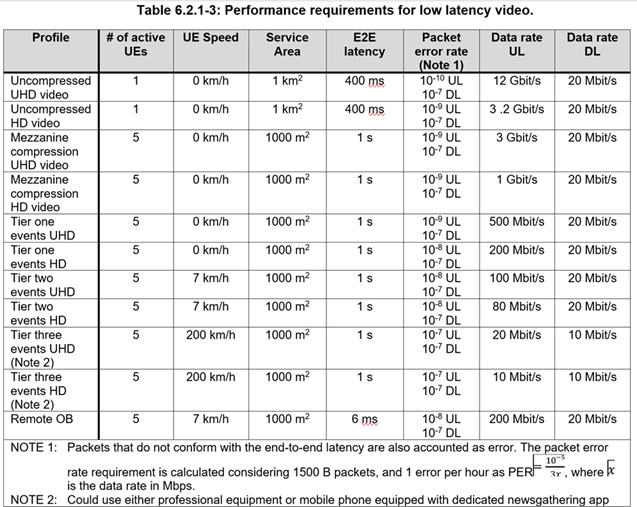
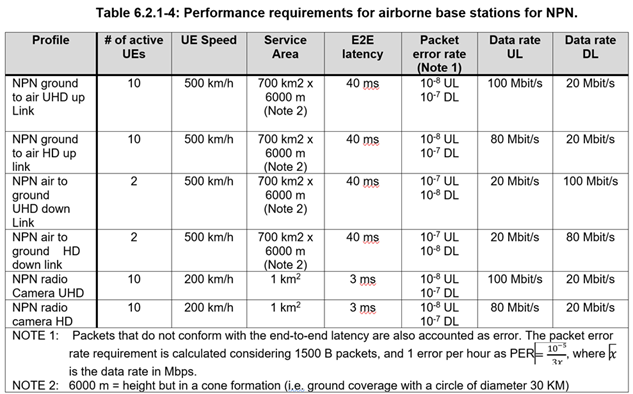
Attached below 5G General Performance Requirements for Video Production Applications & Airborne Base Stations for NPN (Non Public Network)
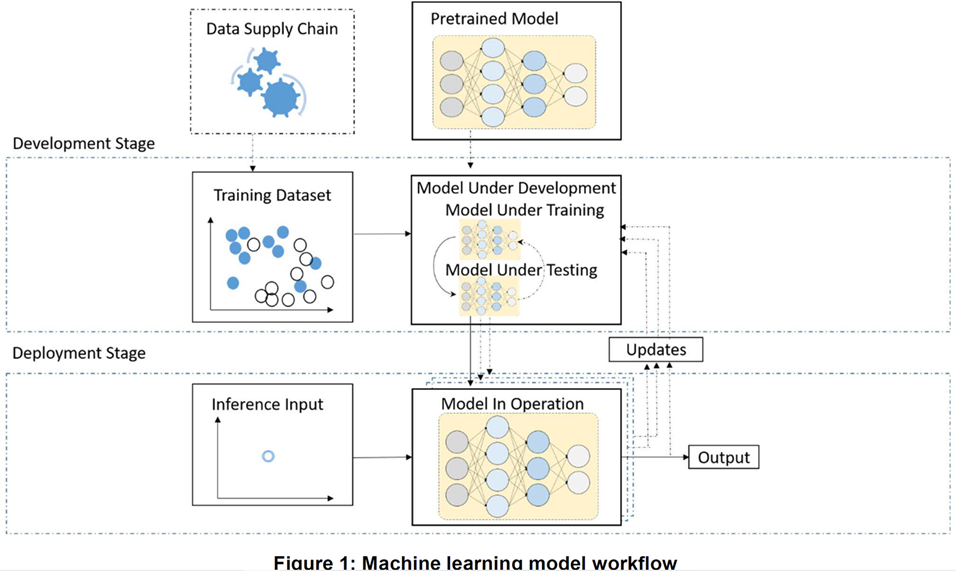
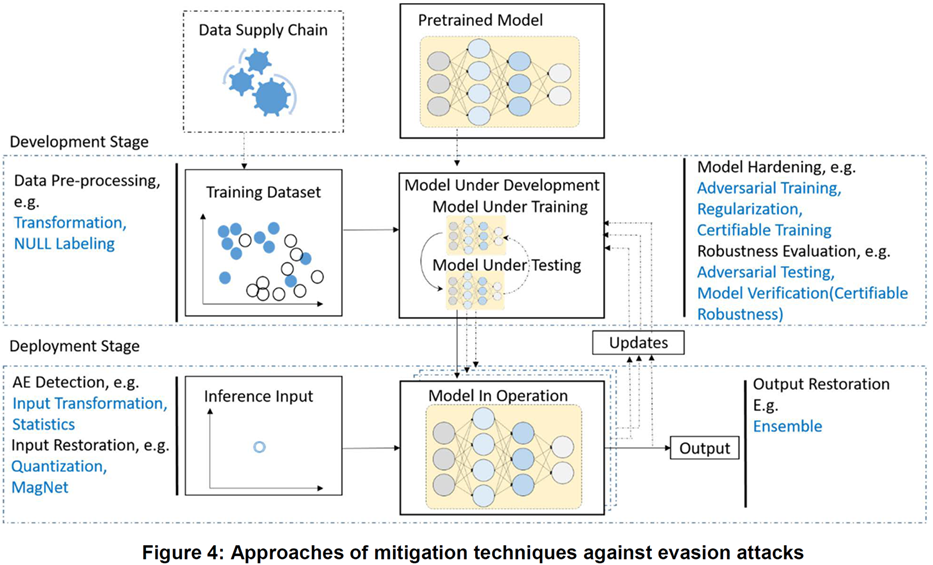
Attack types related to Securing AI and related to it Mitigation Strategies are classified into two (2) main Categories, i.e. Training Attacks which occur during Development Stage and Inference Attacks which occur during Deployment Stage. Training Attacks include Poisoning Attacks and Backdoor Attacks while Inference Attacks include Evasion Attacks and Reverse Engineering Attacks. Model Stealing Attacks and Data Extraction Attacks are two (2) subtypes of Reverse Engineering Attacks. Some State-of-the-Art Adversarial ML papers & reports provide more details of existing attacks against Deep Learning (DL) Systems.
Assessment summary and Recommendation to Akraino TSC: Overall assessment is that the BP's Documentation for Akraino Rel 4 is well prepared and thorough for each Part. There is a good overview on the overall Solution and related UCs. Therein, it is recommended to the Akraino TSC to deem the BP's Rel. 4 Documentation as accepted.
...