Introduction
ICN SDEWAN solution leverages IPSec functionality in SD-EWAN CNF to setup security tunnel to enable communication between ONAP4K8S/APPX Manager with Edge cluster or Edge cluster with Edge cluster. There are several solutions in OpenWRT to implement IPSec, include: Openswan, Racoon, and StrongSwan. ICN will use StrongSwan solution.
OpenWRT StrongSwan Basic
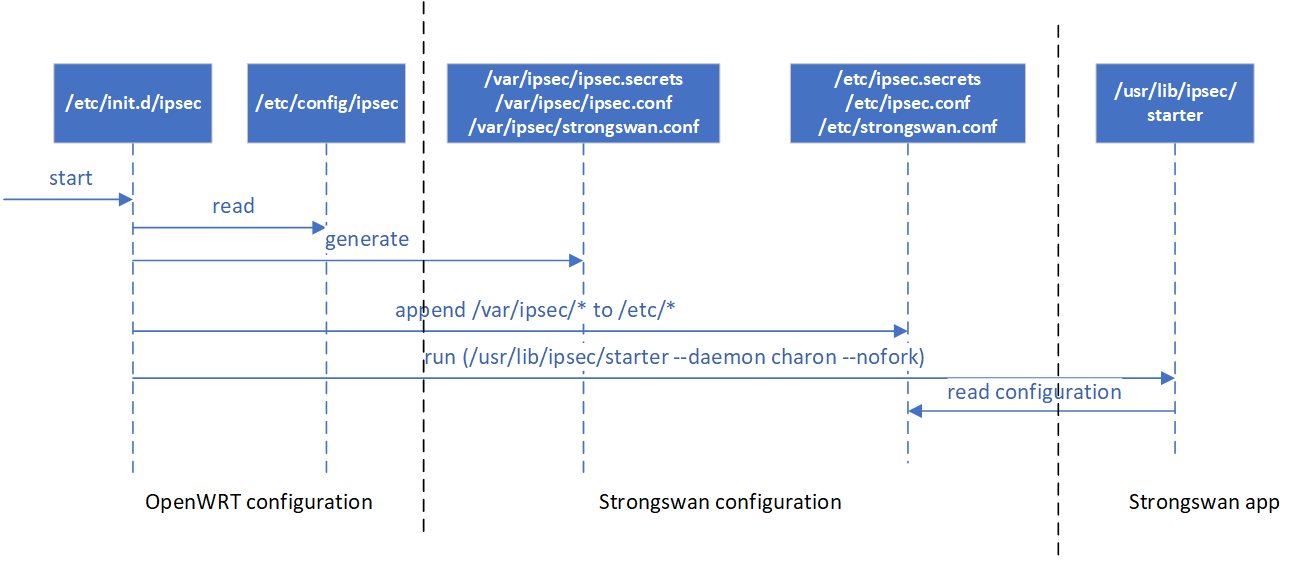
Service Start Flow:
StrongSwan application is run by command: "/etc/init.d/ipsec start", this command will generate StrongSwan's configuration (e.g. /etc/ipsec/*) based on openwrt configuration (e.g. /etc/config/ipsec) then start ipsec application as daemon, below diagram shows its flow
Configuration: OpenWRT's IPSec Configuration is defined in /etc/config/ipsec, the detail configuration content and map to StrongSwan configuration are described in below table
| Section | Option | Type | StrongSwan configuration file | StrongSwan configuration option | Validated values | Description |
|---|---|---|---|---|---|---|
| ipsec | Global configuration | |||||
| debug | int | strongswan.conf | charon.syslog | whether to enable log information | ||
| rtinstall_enabled | boolean | strongswan.conf | charon.install_routes | Install routes into a separate routing table for established IPsec tunnels. | ||
| ignore_routing_tables | list | strongswan.conf | charon.ignore_routing_tables | A space-separated list of routing tables to be excluded from route lookup. | ||
| interface | list | strongswan.conf | charon.interfaces_use | A comma-separated list of network interfaces that should be used by charon. All other interfaces are ignored. | ||
| remote | Define a group remote tunnels with same security configuration | |||||
| tunnel | list | |||||
| transport | list | |||||
| enabled | boolean | whether this configuration is enabled | ||||
| gateway | String | ipsec.secrets ipsec.conf | local_gateway/remote_gateway right | 192.168.0.5 | Defines the counter party ip address here | |
| pre_shared_key | String | ipsec.secrets | PSK | Add the PSK inside the secrets file | ||
| auth_method | String | ipsec.conf | leftauth/rightauth | pubkey, psk, eap, xauth | Defines the auth method that going to be used by two counter parties. | |
| local_identifier | String | ipsec.secrets ipsec.conf | local_identifier leftid | "C=CH, O=strongSwan, CN=peer" | Assigns a specific identifier for the itself (This identity will be send to the counter party inside the request) | |
| remote_identifier | String | ipsec.secrets ipsec.conf | remote_identifier rightid | "C=CH, O=strongSwan, CN=peerB" | Assigns a specific identifier for the counter party | |
| crypto_proposal | list | ipsec.conf | ike | default: aes128-sha256-modp3072 | Defines list of IKE/ISAKMP SA encryption/authentication algorithms to be used | |
| force_crypto_proposal | boolean | |||||
tunnel /transport | Define configuration for a tunnel or transport | |||||
| mode | String | ipsec.conf | auto | add/start/route | Sets the operation for the connection while starts. | |
| local_subnet | String | ipsec.conf | leftsubnet | 192.168.1.1/24 | Mostly used in site-to-site case. Sets the local subnet | |
| local_nat | String | ipsec.conf | leftsubnet | 192.168.1.1/24 | Mostly used in site-to-site case. Sets the local subnet | |
| local_sourceip | String | ipsec.conf | leftsourceip | 192.168.1.2, %config | Sets the ip address of local site. The value can be set to '%config' if the site is going to request a dynamic ip from the counter party | |
| local_updown | String | ipsec.conf | leftupdown | The Updown plugin can be used to set custom firewall rules. | ||
| local_firewall | String | ipsec.conf | leftfirewall | yes, no(default) | ||
| remote_subnet | String | ipsec.conf | rightsubnet | 192.168.0.1/24 | Mostly used in site-to-site case. Sets the subnet of the counter party | |
| remote_sourceip | String | ipsec.conf | rightsourceip | 192.168.0.2, 192.168.0.3-192.168.0.15 | Sets the ip address of the remote site. An ip pool can also be assigned when using the virtual ip | |
| remote_updown | String | ipsec.conf | rightupdown | |||
| remote_firewall | String | ipsec.conf | rightfirewall | |||
| ikelifetime | String | ipsec.conf | ikelifetime | 60m | Sets the life time of the ike process before its re-negotiation | |
| lifetime | String | ipsec.conf | lifetime | 1h(default) | Set the life time of a particular instance would last | |
| margintime | String | ipsec.conf | margintime | 9m(default) | Sets how long before connection expiry or keying-channel expiry should attempts to negotiate a replacement begin | |
| keyingtries | String | ipsec.conf | keyingtries | 3(default) | Sets the maxium attempts to negotiate for a connection | |
| dpdaction | String | ipsec.conf | dpdaction | clear, hold, restart, none(default) | Sets the action against peer timeout, validated through Dead Peer Protection Protocol | |
| dpddelay | String | ipsec.conf | dpddelay | 30s(default) | Defines the time interval for the informational exchange sent to peer | |
| inactivity | boolean | ipsec.conf | inactivity | 30m | Defines the timeout interval, after which a CHILD_SA is closed if it did not send or receive any traffic | |
| keyexchange | String | ipsec.conf | keyexchange | ikev2, ikev1, ike(default, same as ikev2) | Defines the protocol being used to initialize the connection | |
| crypto_proposal | list | ipsec.conf | esp | aes128-sha256(default) | Defines the comma-separated list of ESP encryption/authentication algorithms to be used for the connection | |
| proposal | Define configuration for a proposal | |||||
| encryption_algorithm | String | ipsec.conf | ike/esp | aes128 | Defines the encryption algorithm(together in ike) | |
| hash_algorithm | String | ipsec.conf | ike/esp | sha256 | Defines the hash algorithm(together in ike) | |
| dh_group | String | ipsec.conf | ike/esp | modp3072 | Define the Diffie-Hellman group(together in ike) |
IPSec CRD
IPSec CRD will be created by EWAN config Agent to configurate a remote configuration. it is defined as below, with filed map to ipsec configuration.
apiVersion: sdewan.akraino.org/v1alpha1
kind: IPSecSite
metadata:
name: site1
spec:
node: node1
gateway:
pre_shared_key:
auth_method:
local_identifier:
remote_identifier:
crypto_proposal: "proposal1"
force_crypto_proposal: true
connection:
- type: tunnel/transport
mode:
local_subnet:
local_nat:
local_sourceip:
local_updown:
local_firewall:
remote_subnet:
remote_sourceip:
remote_updown:
remote_firewall:
keyexchange: "ikev2"
inactivity:
crypto_proposal: "proposal1 proposal2"
proposal:
- encryption_algorithm:
hash_algorithm:
dh_group:
IPSec Rest API
SD-EWAN IPSec Restful API provides support to get/create/update/delete IPSec Site, Proposal.
IPSec Proposal
GET /cgi-bin/luci/sdewan/ipsec/v1/proposals
Lists all defined proposals
Request: N/A
Response
- Normal response codes: 200
Response Parameters
Name
In
Type
Description
proposals body array a list of defined proposals Response Example
{
"proposals": [{
"name":"proposal1",
"encryption_algorithm": "aes128",
"hash_algorithm": "sha256",
"dh_group": "modp3072"
}
]
}
GET /cgi-bin/luci/sdewan/ipsec/v1/proposal/{proposal}
Get a proposal
Request: N/A
Request Parameters
Name
In
Type
Description
proposal path string proposal name
Response
- Normal response codes: 200
- Error response code: 404
Response Parameters
Name
In
Type
Description
name body string proposal name encryption_algorithm body string encryption algorithm hash_algorithm body string hash algorithm dh_group body string Diffie-Hellman group Response Example
{
"name":"proposal1",
"encryption_algorithm": "aes128",
"hash_algorithm": "sha256",
"dh_group": "modp3072"
}
POST /cgi-bin/luci/sdewan/ipsec/v1/proposal
create a new proposal
Request:
Request Parameters: same with GET's response request
- Request Example: same with GET's response example
Response
- Normal response codes: 201
- Error response codes: 400, 401
PUT /cgi-bin/luci/sdewan/ipsec/v1/proposal/{proposal}
update a proposal
Request:
Request Parameters:
Name
In
Type
Description
proposal path string proposal name encryption_algorithm body string encryption algorithm hash_algorithm body string hash algorithm dh_group body string Diffie-Hellman group - Request Example
{
"encryption_algorithm": "aes256",
"hash_algorithm": "sha256",
"dh_group": "modp4096"
}
Response
- Normal response codes: 204
- Error response codes: 400, 401, 404
DELETE /cgi-bin/luci/sdewan/ipsec/v1/proposal/{proposal}
delete a proposal
Request:
Request Parameters
Name
In
Type
Description
proposal path string proposal name
Response
- Normal response codes: 200
- Error response codes: 401, 404
IPSec Site
GET /cgi-bin/luci/sdewan/ipsec/v1/sites
Lists all defined sites
Request: N/A
Response
- Normal response codes: 200
Response Parameters
Name
In
Type
Description
sites body array a list of defined sites Response Example
{
"sites": [{
"name": "site1"
"gateway":"10.10.10.10",
"crypto_proposal": "proposal1"
"connections": [
{
"type": "tunnel"
"local_subnet": "192.168.1.1/24"
"remote_subnet": "192.168.0.1/24"
"crypto_proposal": "proposal1"
}
}
]
}
GET /cgi-bin/luci/sdewan/ipsec/v1/site/{site}
Get a site
Request: N/A
Request Parameters
Name
In
Type
Description
site path string remote site name
Response
- Normal response codes: 200
- Error response code: 404
Response Parameters
Name
In
Type
Description
name body string site name gateway body string pre_shared_key body string auth_method body string local_identifier body string remote_identifier body string crypto_proposal body string force_crypto_proposal body boolean connection body array type body string "tunnel" or "transport" mode body string local_subnet body string local_nat body string local_sourceip body string local_updown body string local_firewall body string firewall rule? remote_subnet body string remote_sourceip body string remote_updown body string remote_firewall body string keyexchange body string default: ikev2 inactivity body boolean crypto_proposal body string Response Example
{
"name": "site1"
"gateway":"10.10.10.10",
"crypto_proposal": "proposal1"
"connections": [
{
"type": "tunnel"
"local_subnet":
"remote_subnet":
"crypto_proposal": "proposal1"
}
}
POST /cgi-bin/luci/sdewan/ipsec/v1/site
create a new proposal
Request:
Request Parameters: same with GET's response request
- Request Example: same with GET's response example
Response
- Normal response codes: 201
- Error response codes: 400, 401
PUT /cgi-bin/luci/sdewan/ipsec/v1/site/{site}
update a site
Request:
Request Parameters:
Name
In
Type
Description
site path string remote site name other params body Same with Get's response - Request Example
{
"gateway":"10.10.10.10",
"crypto_proposal": "proposal1"
"connections": [
{
"type": "tunnel"
"local_subnet":
"remote_subnet":
"crypto_proposal": "proposal1"
}
}
Response
- Normal response codes: 204
- Error response codes: 400, 401, 404
DELETE /cgi-bin/luci/sdewan/ipsec/v1/site/{site}
delete a site
Request:
Request Parameters
Name
In
Type
Description
site path string remote site name
Response
- Normal response codes: 200
- Error response codes: 401, 404