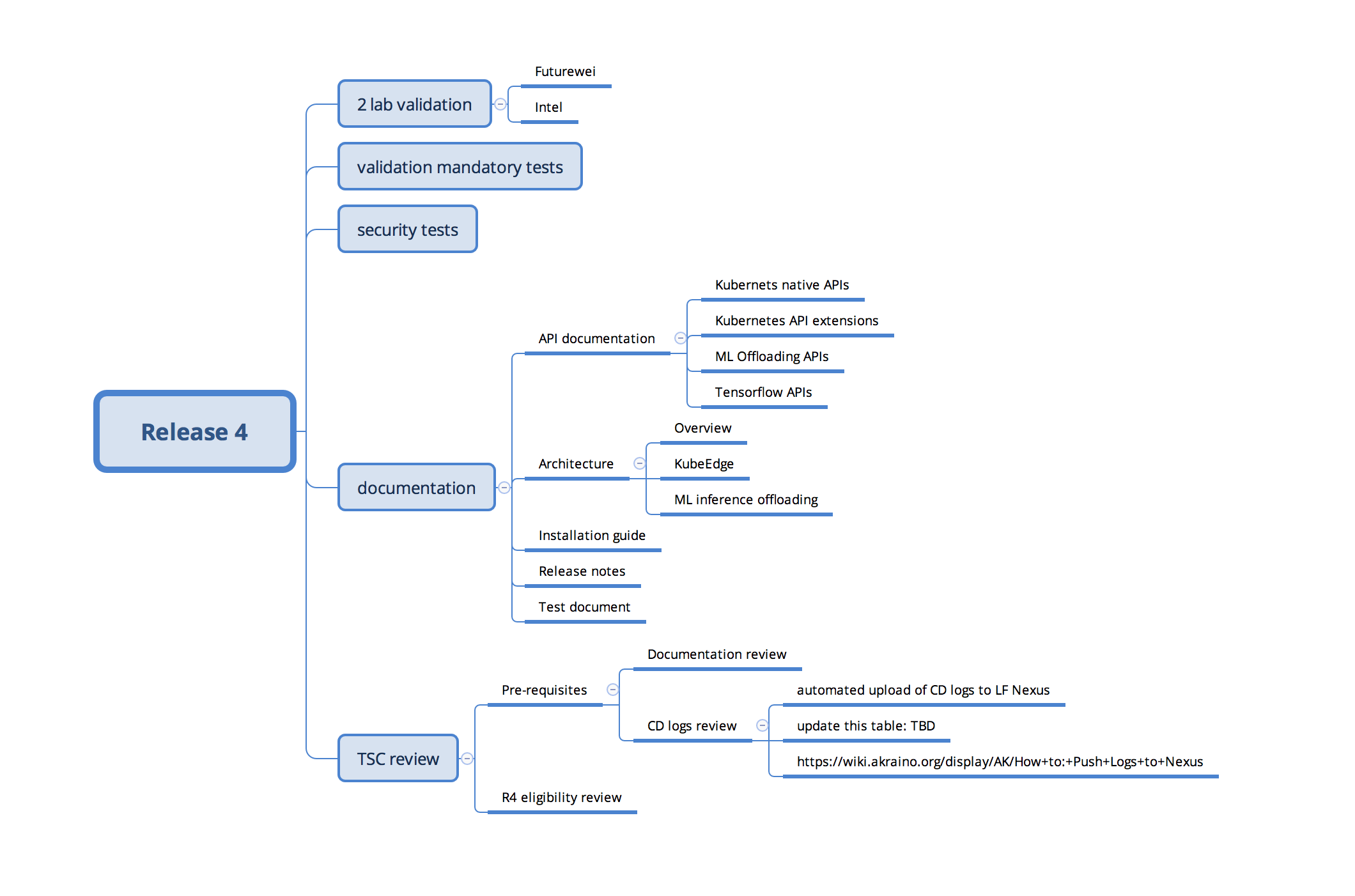
Tasks:
| Task | Owner | Status | Date | ||
|---|---|---|---|---|---|
| 1 | Test | Figure out mandatory Tests and security test list | Hao | Done | |
| Lab set up validation | TBD | ||||
| Test in Futurewei Lab | TBD | ||||
| Test in Intel Lab | TBD | ||||
| 2 | Documentation | Architecture (Add Pod Topology) | Yin, Jane | ||
| Supported Kubernetes native API | Yin, Jane | ||||
| ML Offloading API | Hao/Jiafeng, Jane | ||||
| Installation guide | Hao | ||||
| Release Notes | Yin, Jane | ||||
| 3 | TSC Review | Documentation review | |||
| Log review | |||||
| R4 eligibility |
Detailed Test Tasks:
| Category | Task | Owner | Status | ETA | Comments |
|---|---|---|---|---|---|
CI/CD Logs upload to Nexus | Register an LFID | Hao | Complete | https://jira.linuxfoundation.org/plugins/servlet/theme/portal/2 https://identity.linuxfoundation.org/ https://jira.linuxfoundation.org/plugins/servlet/theme/portal/2/IT-20459 | |
| Request permission for Nexus log | Yin/Hao | Complete | |||
| Set up CD pipelines | Yin | In Progress | |||
| Upload CD logs to Nexus | Hao | In Progress | |||
Bluval | Provision jumpserver | Yin/Hao | Complete | ||
| Test set up and run tests | Hao | In Progress | |||
| Fix issues for failed tests | |||||
| Report results | |||||
Security Scan | Vuls: test set up and run tests | Hao | In Progress | Steps To Implement Security Scan Requirements Reuse the jumpserver for Bluval tests. | |
| Lynis: test set up and run tests | Hao | In Progress | |||
| Kube-Hunter: test set up and run tests | Hao | In Progress | |||
| Fix issues for failed tests | Hao | In Progress | |||
| Upload test results to Nexus |
Test Results & Analysis:
| Test | Result | Applied Fixes | Comment |
|---|---|---|---|
| Lynis | Pass | 27 fixed applied, see Steps To Implement Security Scan Requirements | To maintain the pass result, need to restart the server if it's required |
| Vuls | 8 CVEs with score > 9.0 on Ubuntu 18.04 |
| |
| Kube-Hunter |
| https://aquasecurity.github.io/kube-hunter/kb/KHV002.html https://aquasecurity.github.io/kube-hunter/kb/KHV050.html Disabled CAP_NET_RAW for default pod security context (a tough one to fix!) | KubeEdge edgecore only listens on localhost, so log is not available from another machine. Tried to let edgecore listen on eth0, but kubectl logs still complains about SSL certificate. Workaround: nginx as a reverse proxy, listens on k8s advertised ip, and pass through the traffic to localhost. Added ssl certificate. |
| Conformance |
|