...
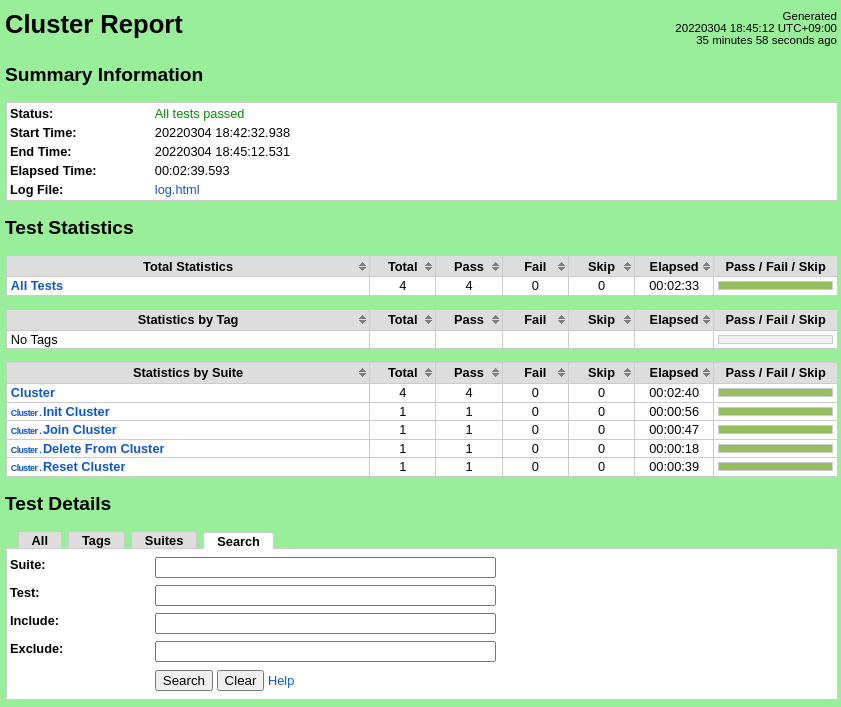
The test scripts will start the cluster, add all configured edge nodes, remove the edge nodes, and reset the cluster. The robot command should report success for all test cases.
Test Results
Nexus URL: https://nexus.akraino.org/content/sites/logs/fujitsu/job/lfedge-cluster/7/
Pass (4/4 test cases)
CI/CD Regression Tests: EdgeX Services
...
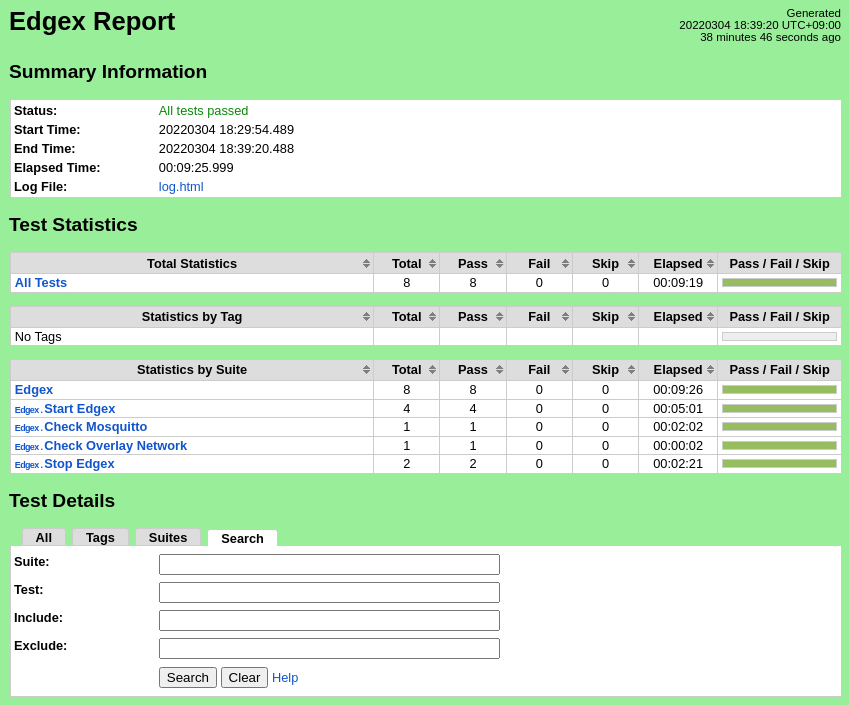
The test scripts will start the EdgeX micro-services on all edge nodes, confirm that MQTT messages are being delivered from the edge nodes, and stop the EdgeX micro-services. The robot command should report success for all test cases.
Test Results
Nexus URL: https://nexus.akraino.org/content/sites/logs/fujitsu/job/edgex-install/7/
Pass (8/8 test cases)
CI/CD Regression Tests: LoRa Device Service
...
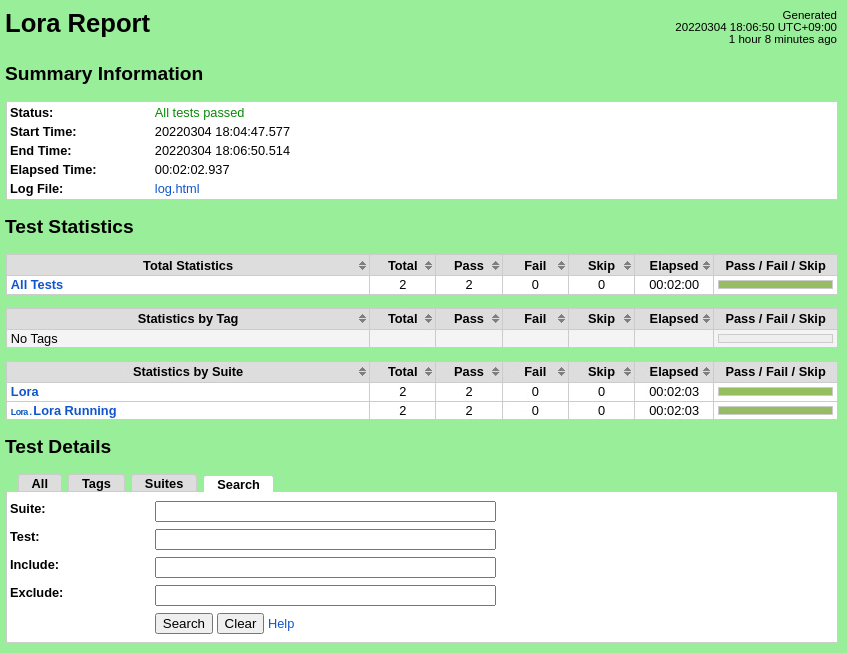
The Robot Framework should report success for all test cases.
Test Results
Nexus URL: https://nexus.akraino.org/content/sites/logs/fujitsu/job/edgex-lora/3/
Pass (2/2 test Pass (2/2 test cases)
Feature Project Tests
...
BluVal tests should report success for all test cases.
Test Results
Insert Results URL
Vuls
There are 17 CVEs with a CVSS score >= 9.0. These are exceptions requested here:
Release 5: Akraino CVE Vulnerability Exception Request
Vuls results (manual) Nexus URL: https://nexus.akraino.org/content/sites/logs/fujitsu/job/sdt-vuls/2/
Lynis results (manual) Nexus URL: https://nexus.akraino.org/content/sites/logs/fujitsu/job/sdt-lynis/2/
Kube-Hunter results Nexus URL: https://nexus.akraino.org/content/sites/logs/fujitsu/job/sdt-bluval/2/
Vuls
Nexus URL: https://nexus.akraino.org/content/sites/logs/fujitsu/job/sdt-vuls/2/
There are 17 CVEs with a CVSS score >= 9.0. These are exceptions requested here:
Release 5: Akraino CVE Vulnerability Exception Request
| CVE-ID | CVSS | NVD | Fix/Notes | ||
|---|---|---|---|---|---|
| CVE-2016-1585 | |||||
| CVE-ID | CVSS | NVD | Fix/Notes | ||
| CVE-2016-1585 | 9.8 | https://nvd.nist.gov/vuln/detail/CVE-2016-1585 | No fix available | ||
| CVE-2021-20236 | 9.8 | https://nvd.nist.gov/vuln/detail/CVE-2021-20236 | No fix available (latest release of ZeroMQ for Ubuntu 20.04 is 4.3.2-2ubuntu1) | ||
| CVE-2021-31870 | 9.8 | https://nvd.nist.gov/vuln/detail/CVE-2021-31870 | No fix available (latest release of klibc for Ubuntu 20.04 is 2.0.7-1ubuntu5) | ||
| CVE-2021-31872 | 9.8 | https://nvd.nist.gov/vuln/detail/CVE-2021-31872 | No fix available (latest release of klibc for Ubuntu 20.04 is 2.0.7-1ubuntu5) | ||
| 9.8 | https://nvd.nist.gov/vuln/detail/CVE- | 20212016- | 318731585 | No fix available (latest release of klibc for Ubuntu 20.04 is 2.0.7-1ubuntu5) | |
| CVE-2021- | 3357420236 | 9.8 | https://nvd.nist.gov/vuln/detail/CVE-2021-20236 | No fix available (latest release of ZeroMQ for Ubuntu 20.04 is 4.3.2-2ubuntu1)33574Will not be fixed in Ubuntu stable releases | |
| CVE-2021- | 4595131870 | 9.8 | https://nvd.nist.gov/vuln/detail/CVE-2021- | 4595131870 | No fix available (vendor disputedlatest release of klibc for Ubuntu 20.04 is 2.0.7-1ubuntu5) |
| CVE-2021-4595231872 | 9.8 | https://nvd.nist.gov/vuln/detail/CVE-2021-4595231872 | No fix available (vendor disputedlatest release of klibc for Ubuntu 20.04 is 2.0.7-1ubuntu5) | ||
| CVE-2021-4595331873 | 9.8 | https://nvd.nist.gov/vuln/detail/CVE-2021-4595331873 | No fix available (vendor disputed)latest release of klibc for Ubuntu 20.04 is 2.0.7-1ubuntu5) | ||
| CVE-2021-33574 | 9.8 | https://nvd.nist.gov/vuln/detail/CVE-2021-33574 | Will not be fixed in Ubuntu stable releases | ||
| CVE-2021-45951CVE-2021-45954 | 9.8 | https://nvd.nist.gov/vuln/detail/CVE-2021-4595445951 | No fix available (vendor disputed) | ||
| CVE-2021-4595545952 | 9.8 | https://nvd.nist.gov/vuln/detail/CVE-2021-4595545952 | No fix available (vendor disputed) | ||
| CVE-2021-4595645953 | 9.8 | https://nvd.nist.gov/vuln/detail/CVE-2021-4595645953 | No fix available (vendor disputed) | ||
| CVE-2021-4595745954 | 9.8 | https://nvd.nist.gov/vuln/detail/CVE-2021-4595745954 | No fix available (vendor disputed) | ||
| CVE-20222021-2321845955 | 9.8 | https://nvd.nist.gov/vuln/detail/CVE-20222021-2321845955 | No fix available (vendor disputed)Reported fixed in 2.31-0ubuntu9.7 (installed), but still reported by Vuls | ||
| CVE-20222021-2321945956 | 9.8 | https://nvd.nist.gov/vuln/detail/CVE-20222021-2321945956 | No fix available (vendor disputed)Reported fixed in 2.31-0ubuntu9.7 (installed), but still reported by Vuls | ||
| CVE-20162021-918045957 | 9.18 | https://nvd.nist.gov/vuln/detail/CVE-20162021-918045957 | No fix available (vendor disputed) | ||
| CVE-20212022-3594223218 | 9.18 | https://nvd.nist.gov/vuln/detail/CVE-20212022-3594223218 | Reported fixed in 2.31-0ubuntu9.7 (installed), but still reported by Vuls |
Lynis
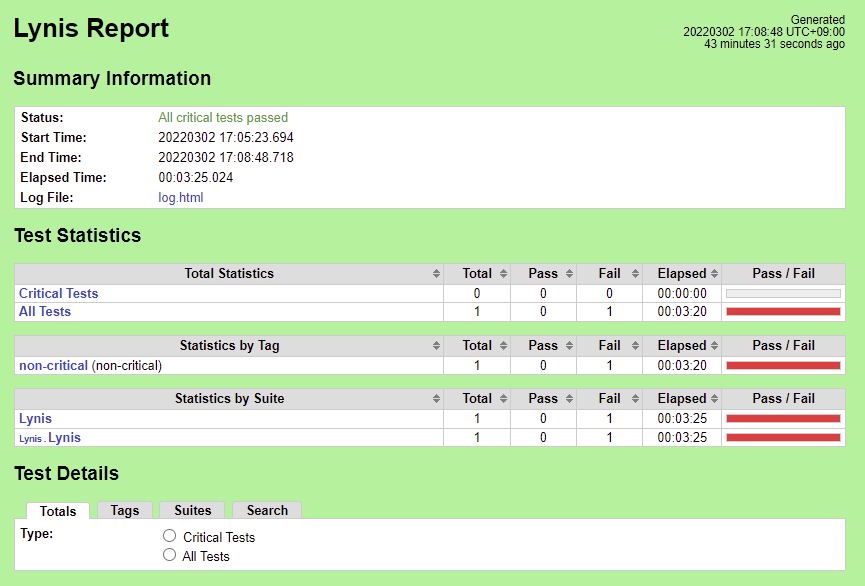
The initial results compare with the Lynis Incubation: PASS/FAIL Criteria, v1.0 as follows.
The Lynis Program Update test MUST pass with no errors.
| CVE-2022-23219 | 9.8 | https://nvd.nist.gov/vuln/detail/CVE-2022-23219 | Reported fixed in 2.31-0ubuntu9.7 (installed), but still reported by Vuls |
| CVE-2016-9180 | 9.1 | https://nvd.nist.gov/vuln/detail/CVE-2016-9180 | No fix available |
| CVE-2021-35942 | 9.1 | https://nvd.nist.gov/vuln/detail/CVE-2021-35942 | Reported fixed in 2.31-0ubuntu9.7 (installed), but still reported by Vuls |
Lynis
Nexus URL (run via Bluval, without fixes): https://nexus.akraino.org/content/sites/logs/fujitsu/job/sdt-bluval/2/
Nexus URL (manual run, with fixes): https://nexus.akraino.org/content/sites/logs/fujitsu/job/sdt-lynis/2/
The initial results compare with the Lynis Incubation: PASS/FAIL Criteria, v1.0 as follows.
The Lynis Program Update test MUST pass with no errors.
2022-03-04 15:33:28 Test: Checking for program update...
2022-03-04 15:33:31 Current installed version : 301
2022-03-04 15:33:312022-03-04 15:33:28 Test: Checking for program update...
2022-03-04 15:33:31 Current installed version : 301
2022-03-04 15:33:31 Latest stable version : 307
2022-03-04 15:33:31 Minimum required version : 297
2022-03-04 15:33:31 Result: newer Lynis release available!
2022-03-04 15:33:31 Suggestion: Version of Lynis outdated, consider upgrading to the latest version [test:LYNIS] [details:-] [solution:-]
...
| No. | Test | Result |
|---|---|---|
| 1 | Test: Checking PASS_MAX_DAYS option in /etc/login.defs | Result: max password age is 180 days |
| 2 | Performing test ID AUTH-9328 (Default umask values) | Result: umask is 027, which is fine |
| 3 | Performing test ID SSH-7440 (Check OpenSSH option: AllowUsers and AllowGroups) | Result: SSH is limited to a specific set of users, which is good |
| 5a | sysctl key fs.suid_dumpable contains equal expected and current value (0) | Result: sysctl key fs.suid_dumpable contains equal expected and current value (0) Hardening: assigned maximum number of hardening points for this item (1). |
| 5b | sysctl key kernel.dmesg_restrict contains equal expected and current value (1) | Result: sysctl key kernel.dmesg_restrict contains equal expected and current value (1) Hardening: assigned maximum number of hardening points for this item (1). |
| 6 | Test: Check if one or more compilers can be found on the system | Result: no compilers found |
The post-fix manual logs can be found at insert nexus link here.
...
| ). | ||
| 6 | Test: Check if one or more compilers can be found on the system | Result: no compilers found |
The post-fix manual logs can be found at https://nexus.akraino.org/content/sites/logs/fujitsu/job/sdt-lynis/2/.
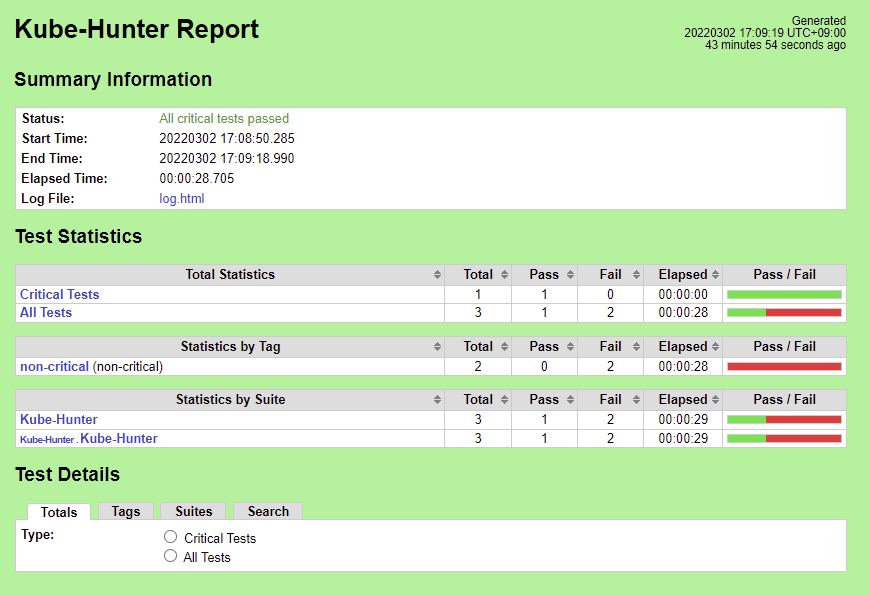
Kube-Hunter
Nexus URL (initial run without fixes): https://nexus.akraino.org/content/sites/logs/fujitsu/job/sdt-bluval/1/
Nexus URL (with fixes): https://nexus.akraino.org/content/sites/logs/fujitsu/job/sdt-bluval/2/
There are 5 Vulnerabilities.
...
*One Kube-Hunter failure is counted as a pass. See above.
Vuls and Lynis test cases are failing, an exception request is filed for Vuls-detected vulnerabilities that cannot be fixed. The Lynis results have been confirmed to pass the Incubation criteria.
Additional Testing
None at this time.
...