| CVE # | Blueprint | Blueprint OS/Ver | URL Showing OS Patch Not Available | Contact Name | Contact Email | Comment | Vendor CVSS Score | Vendor Patch Available | Exception Status |
|---|
| CVE-2016-1585 | EALT-Edge | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2016-1585 | | srinivasanselvam2014@gmail.com |
| Medium | No | Approved |
| CVE-2017-18342 | EALT-Edge | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2017-18342 | | srinivasanselvam2014@gmail.com |
| Low | No | Approved |
| CVE-2017-8283 | EALT-Edge | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2017-8283 | | srinivasanselvam2014@gmail.com |
| Negligible | No | Approved |
| CVE-2018-20839 | EALT-Edge | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2018-20839 | | srinivasanselvam2014@gmail.com |
| Medium | No | Approved |
| CVE-2019-17041 | EALT-Edge | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2019-17041 | | srinivasanselvam2014@gmail.com |
| Low | No | Approved |
| CVE-2019-17042 | EALT-Edge | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2019-17042 | | srinivasanselvam2014@gmail.com |
| Low | No | Approved |
| CVE-2019-19814 | EALT-Edge | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2019-19814 | | srinivasanselvam2014@gmail.com |
| Low | No | Approved |
| CVE-2016-1585 | ELIOT IOT Gateway | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2016-1585 | | srinivasanselvam2014@gmail.com |
| Medium | No | Approved |
| CVE-2017-18342 | ELIOT IOT Gateway | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2017-18342 | | srinivasanselvam2014@gmail.com |
| Low | No | Approved |
| CVE-2017-8283 | ELIOT IOT Gateway | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2017-8283 | | srinivasanselvam2014@gmail.com |
| Negligible | No | Approved |
| CVE-2018-20839 | ELIOT IOT Gateway | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2018-20839 | | srinivasanselvam2014@gmail.com |
| Medium | No | Approved |
| CVE-2019-17041 | ELIOT IOT Gateway | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2019-17041 | | srinivasanselvam2014@gmail.com |
| Low | No | Approved |
| CVE-2019-17042 | ELIOT IOT Gateway | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2019-17042 | | srinivasanselvam2014@gmail.com |
| Low | No | Approved |
| CVE-2019-19814 | ELIOT IOT Gateway | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2019-19814 | | srinivasanselvam2014@gmail.com |
| Low | No | Approved |
| CVE-2016-1585 | ELIOT SD-WAN/WAN Edge/uCPE | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2016-1585 | | srinivasanselvam2014@gmail.com |
| Medium | No | Approved |
| CVE-2017-18342 | ELIOT SD-WAN/WAN Edge/uCPE | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2017-18342 | | srinivasanselvam2014@gmail.com |
| Low | No | Approved |
| CVE-2017-8283 | ELIOT SD-WAN/WAN Edge/uCPE | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2017-8283 | | srinivasanselvam2014@gmail.com |
| Negligible | No | Approved |
| CVE-2018-20839 | ELIOT SD-WAN/WAN Edge/uCPE | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2018-20839 | | srinivasanselvam2014@gmail.com |
| Medium | No | Approved |
| CVE-2019-17041 | ELIOT SD-WAN/WAN Edge/uCPE | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2019-17041 | | srinivasanselvam2014@gmail.com |
| Low | No | Approved |
| CVE-2019-17042 | ELIOT SD-WAN/WAN Edge/uCPE | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2019-17042 | | srinivasanselvam2014@gmail.com |
| Low | No | Approved |
| CVE-2019-19814 | ELIOT SD-WAN/WAN Edge/uCPE | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2019-19814 | | srinivasanselvam2014@gmail.com |
| Low | No | Approved |
| CVE-2016-1585 | ICN | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2016-1585 | @Kuralamdhan Ramakrishnan | kuralamudhan.ramakrishnan@intel.com |
| Medium | No | Approved |
| CVE-2017-18342 | ICN | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2017-18342 | @Kuralamdhan Ramakrishnan | kuralamudhan.ramakrishnan@intel.com |
| Low | No | Approved |
| CVE-2017-8283 | ICN | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2017-8283 | @Kuralamdhan Ramakrishnan | kuralamudhan.ramakrishnan@intel.com |
| Negligible | 18.04 Not vulnerable 1.18..24ubuntu1 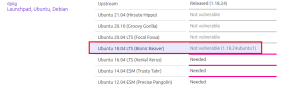 Image Modified Image Modified
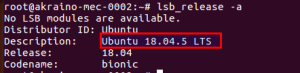 Image Modified Image Modified
| Approved |
| CVE-2018-20839 | ICN | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2018-20839 | @Kuralamdhan Ramakrishnan | kuralamudhan.ramakrishnan@intel.com |
| Medium | No | Approved |
| CVE-2019-19814 | ICN | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2019-19814 | @Kuralamdhan Ramakrishnan | kuralamudhan.ramakrishnan@intel.com |
| Low | No | Approved |
| CVE-2019-17041 | ICN | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2019-17041 | @Kuralamdhan Ramakrishnan | kuralamudhan.ramakrishnan@intel.com |
| Low | No | Approved |
| CVE-2019-17042 | ICN | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2019-17042 | @Kuralamdhan Ramakrishnan | kuralamudhan.ramakrishnan@intel.com |
| Low | No | Approved |
| CVE-2016-1585 | Public Cloud Edge Interface (PCEI) | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2016-1585 | | oberzin@equinix.com |
| Medium | No | Approved |
| CVE-2017-18342 | Public Cloud Edge Interface (PCEI) | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2017-18342 | | oberzin@equinix.com |
| Low | No | Approved |
| CVE-2017-8283 | Public Cloud Edge Interface (PCEI) | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2017-8283 | | oberzin@equinix.com |
| Negligible | No | Approved |
| CVE-2018-20839 | Public Cloud Edge Interface (PCEI) | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2018-20839 | | oberzin@equinix.com |
| Medium | No | Approved |
| CVE-2019-17041 | Public Cloud Edge Interface (PCEI) | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2019-17041 | | oberzin@equinix.com |
| Low | No | Approved |
| CVE-2019-17042 | Public Cloud Edge Interface (PCEI) | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2019-17042 | | oberzin@equinix.com |
| Low | No | Approved |
| CVE-2019-19814 | Public Cloud Edge Interface (PCEI) | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2019-19814 | | oberzin@equinix.com |
| Low | No | Approved |
| CVE-2016-1585 | ICN - Multi-Tenant Secure Cloud Native Platform | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2016-1585 | | salvador.fuentes@intel.com |
| Medium | No | Approved |
| CVE-2017-18342 | ICN - Multi-Tenant Secure Cloud Native Platform | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2017-18342 | | salvador.fuentes@intel.com |
| Low | No | Approved |
| CVE-2017-8283 | ICN - Multi-Tenant Secure Cloud Native Platform | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2017-8283 | | salvador.fuentes@intel.com |
| Negligible | No | Approved |
| CVE-2018-20839 | ICN - Multi-Tenant Secure Cloud Native Platform | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2018-20839 | | salvador.fuentes@intel.com |
| Medium | No | Approved |
| CVE-2019-17041 | ICN - Multi-Tenant Secure Cloud Native Platform | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2019-17041 | | salvador.fuentes@intel.com |
| Low | No | Approved |
| CVE-2019-17042 | ICN - Multi-Tenant Secure Cloud Native Platform | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2019-17042 | | salvador.fuentes@intel.com |
| Low | No | Approved |
| CVE-2019-19814 | ICN - Multi-Tenant Secure Cloud Native Platform | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2019-19814 | | salvador.fuentes@intel.com |
| Low | No | Approved |
| CVE-2019-12900 | The AI Edge: Federated ML application at edge | CentOS 7.9 | https://access.redhat.com/security/cve/cve-2019-12900 | | wuzifan0817@gmail.com |
| Low | No | Approved |
| CVE-2017-12652 | AI Edge: School/Education Video Security | CentOS 7.9 | https://access.redhat.com/security/cve/cve-2017-12652 | Yu, Liya | yulia@baidu.com |
| Low | Yes, however, patch has been installed (see below) however, vuls still reporting CVE. 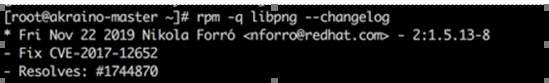 Image Modified Image Modified | |
| CVE-2019-5482 | AI Edge: School/Education Video Security | CentOS 7.9 | https://access.redhat.com/security/cve/cve-2019-5482 | Yu, Liya | yulia@baidu.com |
| Medium | Yes, however, patch has been installed (see below) however, vuls still reporting CVE. 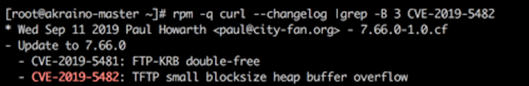 Image Modified Image Modified
| |
| CVE-2016-1585 | Smart Data Transaction for CPS | Ubuntu 20.04 | https://ubuntu.com/security/CVE-2016-1585 | Colin Peters | colin.peters@fujitsu.com |
| Medium | No |
|
| CVE-2021-20236 | Smart Data Transaction for CPS | Ubuntu 20.04 | https://ubuntu.com/security/CVE-2021-20236 | | colin.peters@fujitsu.com |
| Medium | No |
|
| CVE-2021-31870 | Smart Data Transaction for CPS | Ubuntu 20.04 | https://ubuntu.com/security/CVE-2021-31870 | | colin.peters@fujitsu.com |
| Low | No |
|
| CVE-2021-31872 | Smart Data Transaction for CPS | Ubuntu 20.04 | https://ubuntu.com/security/CVE-2021-31872 | | colin.peters@fujitsu.com |
| Low | No |
|
| CVE-2021-31873 | Smart Data Transaction for CPS | Ubuntu 20.04 | https://ubuntu.com/security/CVE-2021-31873 | | colin.peters@fujitsu.com |
| Low | No |
|
| CVE-2021-33574 | Smart Data Transaction for CPS | Ubuntu 20.04 | https://ubuntu.com/security/CVE-2021-33574 | | colin.peters@fujitsu.com |
| Low | No |
|
| CVE-2021-45951 | Smart Data Transaction for CPS | Ubuntu 20.04 | https://ubuntu.com/security/CVE-2021-45951 | | colin.peters@fujitsu.com |
| Medium | No |
|
| CVE-2021-45952 | Smart Data Transaction for CPS | Ubuntu 20.04 | https://ubuntu.com/security/CVE-2021-45952 | | colin.peters@fujitsu.com |
| Medium | No |
|
| CVE-2021-45953 | Smart Data Transaction for CPS | Ubuntu 20.04 | https://ubuntu.com/security/CVE-2021-45953 | | colin.peters@fujitsu.com |
| Medium | No |
|
| CVE-2021-45954 | Smart Data Transaction for CPS | Ubuntu 20.04 | https://ubuntu.com/security/CVE-2021-45954 | | colin.peters@fujitsu.com |
| Medium | No |
|
| CVE-2021-45955 | Smart Data Transaction for CPS | Ubuntu 20.04 | https://ubuntu.com/security/CVE-2021-45955 | | colin.peters@fujitsu.com |
| Medium | No |
|
| CVE-2021-45956 | Smart Data Transaction for CPS | Ubuntu 20.04 | https://ubuntu.com/security/CVE-2021-45956 | | colin.peters@fujitsu.com |
| Medium | No |
|
| CVE-2021-45957 | Smart Data Transaction for CPS | Ubuntu 20.04 | https://ubuntu.com/security/CVE-2021-45957 | | colin.peters@fujitsu.com |
| Medium | No |
|
| CVE-2022-23218 | Smart Data Transaction for CPS | Ubuntu 20.04 | https://ubuntu.com/security/CVE-2022-23218 | | colin.peters@fujitsu.com |
| Low | Reported fixed in 2.31-0ubuntu9.7 (installed), but still reported by Vuls. |
|
| CVE-2022-23219 | Smart Data Transaction for CPS | Ubuntu 20.04 | https://ubuntu.com/security/CVE-2022-23219 | | colin.peters@fujitsu.com |
| Low | Reported fixed in 2.31-0ubuntu9.7 (installed), but still reported by Vuls. |
|
| CVE-2016-9180 | Smart Data Transaction for CPS | Ubuntu 20.04 | https://ubuntu.com/security/CVE-2016-9180 | | colin.peters@fujitsu.com |
| Low | No |
|
| CVE-2021-35942 | Smart Data Transaction for CPS | Ubuntu 20.04 | https://ubuntu.com/security/CVE-2021-35942 | | colin.peters@fujitsu.com |
| Low | Reported fixed in 2.31-0ubuntu9.7 (installed), but still reported by Vuls. |
|
CVE-2016-1585 | Robot basic architecture based on SSES | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2016-1585 | | inoue.reo@fujitsu.com
|
| Medium | No |
|
CVE-2017-18201 | Robot basic architecture based on SSES | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2017-18201 | | inoue.reo@fujitsu.com
|
| Low | No |
|
CVE-2017-7827 | Robot basic architecture based on SSES | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2017-7827 | | inoue.reo@fujitsu.com |
| Medium | No |
|
CVE-2018-5090 | Robot basic architecture based on SSES | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2018-5090 | | inoue.reo@fujitsu.com |
| Medium | Reported fixed in 58 and later version (installed), but still reported by Vuls |
|
CVE-2018-5126 | Robot basic architecture based on SSES | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2018-5126 | | inoue.reo@fujitsu.com |
| Medium | Reported fixed in 58 and later version (installed), but still reported by Vuls |
|
CVE-2018-5145 | Robot basic architecture based on SSES | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2018-5145 | | inoue.reo@fujitsu.com |
| Medium | Reported fixed in 1:52.7.0 and later version (installed), but still reported by Vuls |
|
CVE-2018-5151 | Robot basic architecture based on SSES | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2018-5151 | | inoue.reo@fujitsu.com |
| Medium | Reported fixed in 60 and later version (installed), but still reported by Vuls |
|
CVE-2019-17041 | Robot basic architecture based on SSES | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2019-17041 | | inoue.reo@fujitsu.com |
| Low | No |
|
CVE-2019-17042 | Robot basic architecture based on SSES | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2019-17042 | | inoue.reo@fujitsu.com |
| Low | No |
|
CVE-2021-31870 | Robot basic architecture based on SSES | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2021-31870 | | inoue.reo@fujitsu.com |
| Low | No |
|
CVE-2021-31872 | Robot basic architecture based on SSES | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2021-31872 | | inoue.reo@fujitsu.com |
| Low | No |
|
CVE-2021-31873 | Robot basic architecture based on SSES | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2021-31873 | | inoue.reo@fujitsu.com |
| Low | No |
|
CVE-2021-39713 | Robot basic architecture based on SSES | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2021-39713 | | inoue.reo@fujitsu.com |
| Low | No |
|
CVE-2022-22822 | Robot basic architecture based on SSES | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2022-22822 | | inoue.reo@fujitsu.com |
| Medium | No |
|
CVE-2022-22823 | Robot basic architecture based on SSES | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2022-22823 | | inoue.reo@fujitsu.com |
| Medium | No |
|
CVE-2022-22824 | Robot basic architecture based on SSES | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2022-22824 | | inoue.reo@fujitsu.com |
| Medium | No |
|
CVE-2022-23852 | Robot basic architecture based on SSES | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2022-23852 | | inoue.reo@fujitsu.com |
| Medium | No |
|
CVE-2022-23990 | Robot basic architecture based on SSES | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2022-23990 | | inoue.reo@fujitsu.com |
| Medium | No |
|
CVE-2022-25235 | Robot basic architecture based on SSES | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2022-25235 | | inoue.reo@fujitsu.com |
| High | No |
|
CVE-2022-25236 | Robot basic architecture based on SSES | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2022-25236 | | inoue.reo@fujitsu.com |
| High | No |
|
CVE-2022-25315 | Robot basic architecture based on SSES | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2022-25315 | | inoue.reo@fujitsu |



