...
The Lynis Program Update test MUST pass with no errors.
...
The following list of tests MUST complete as passing
...
Result: max password age is 180 days
Hardening: assigned maximum number of hardening points for this item (3).
...
Result: umask is 027, which is fine
Hardening: assigned maximum number of hardening points for this item (2).
...
Result: SSH is limited to a specific set of users, which is good
Hardening: assigned maximum number of hardening points for this item (2).
...
Result: sysctl key net.ipv4.conf.default.accept_source_route contains equal expected and current value (0)
Hardening: assigned maximum number of hardening points for this item (1).
...
Result: no compilers found
Hardening: assigned maximum number of hardening points for this item (3).
The post-fix manual logs can be found at https://nexus.akraino.org/content/sites/logs/fujitsu/job/sdt-lynis/3/.
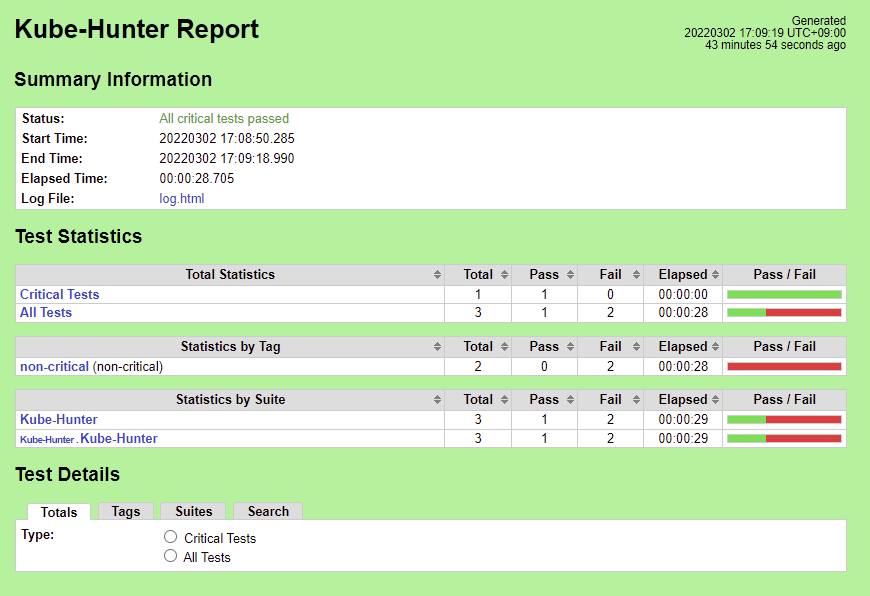
Kube-Hunter
Nexus URL (initial run without fixes): https://nexus.akraino.org/content/sites/logs/fujitsu/job/sdt-bluval/1/
Nexus URL (with fixes): https://nexus.akraino.org/content/sites/logs/fujitsu/job/sdt-bluval/2/
There are 5 Vulnerabilities.
- KHV002
- KHV005
- KHV050
- CAP_NET_RAW Enabled
- Access to pod's secrets
Fix for KHV002
...
$ kubectl replace -f - <<EOF
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
annotations:
rbac.authorization.kubernetes.io/autoupdate: "false"
labels:
kubernetes.io/bootstrapping: rbac-defaults
name: system:public-info-viewer
rules:
- nonResourceURLs:
- /healthz
- /livez
- /readyz
verbs:
- get
EOF
Fix for KHV005, KHV050, Access to pod's secrets
...
$ kubectl replace -f - <<EOF
apiVersion: v1
kind: ServiceAccount
metadata:
name: default
namespace: default
automountServiceAccountToken: false
EOF
TODO
The following list of tests MUST complete as passing
| No. | Test | Result |
|---|---|---|
| 1 | Test: Checking PASS_MAX_DAYS option in /etc/login.defs | TODO |
| 2 | Performing test ID AUTH-9328 (Default umask values) | TODO |
| 3 | Performing test ID SSH-7440 (Check OpenSSH option: AllowUsers and AllowGroups) | TODO |
| 4 | Test: checking for file /etc/network/if-up.d/ntpdate | TODO |
| 5 | Performing test ID KRNL-6000 (Check sysctl key pairs in scan profile) : Following sub-tests required | |
| 5a | sysctl key fs.suid_dumpable contains equal expected and current value (0) | TODO |
| 5b | sysctl key kernel.dmesg_restrict contains equal expected and current value (1) | TODO |
| 5c | sysctl key net.ipv4.conf.default.accept_source_route contains equal expected and current value (0) | TODO |
| 6 | Test: Check if one or more compilers can be found on the system | TODO |
The post-fix manual logs can be found at TODO.
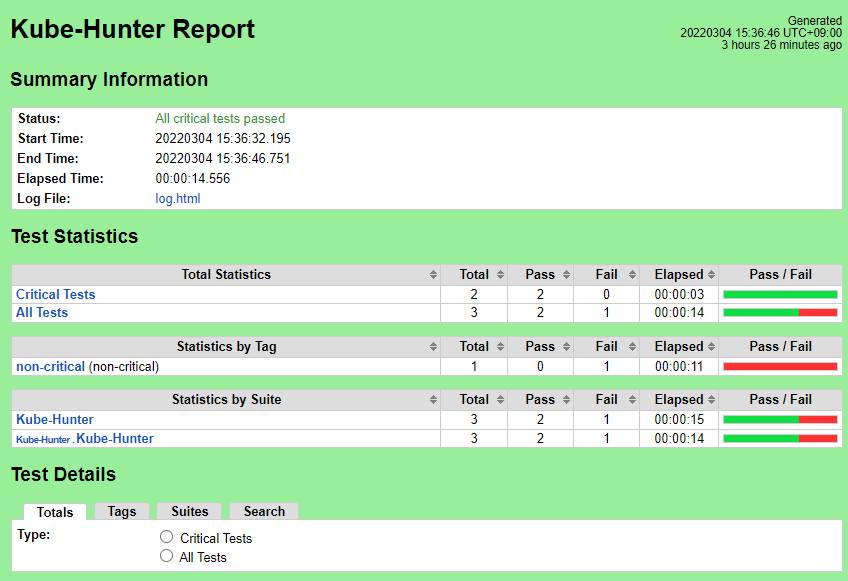
Kube-Hunter
Nexus URL: TODO
There are no reported vulnerabilities. Note, this release includes fixes for vulnerabilities found in release 6. See the release 6 test document for details on those vulnerabilities and the fixes.
Note that
The above fixes are implemented in the Ansible playbook deploy/playbook/init_cluster.yml and configuration file deploy/playbook/k8s/fix.yml
Fix for CAP_NET_RAW Enabled:
Create a PodSecurityPolicy with requiredDropCapabilities: NET_RAW. The policy is shown below. The complete fix is implemented in the Ansible playbook deploy/playbook/init_cluster.yml and configuration files deploy/playbook/k8s/default-psp.yml and deploy/playbook/k8s/system-psp.yml, plus enabling PodSecurityPolicy checking in deploy/playbook/k8s/config.yml.
...
apiVersion: policy/v1beta1
kind: PodSecurityPolicy
metadata:
name: psp-baseline
spec:
privileged: true
allowPrivilegeEscalation: true
allowedCapabilities:
- IPC_LOCK
- NET_ADMIN
requiredDropCapabilities:
- NET_RAW
hostIPC: true
hostNetwork: true
hostPID: true
hostPorts:
- max: 65535
min: 0
readOnlyRootFilesystem: false
fsGroup:
rule: 'RunAsAny'
runAsUser:
rule: 'RunAsAny'
seLinux:
rule: 'RunAsAny'
supplementalGroups:
rule: 'RunAsAny'
volumes:
- '*'
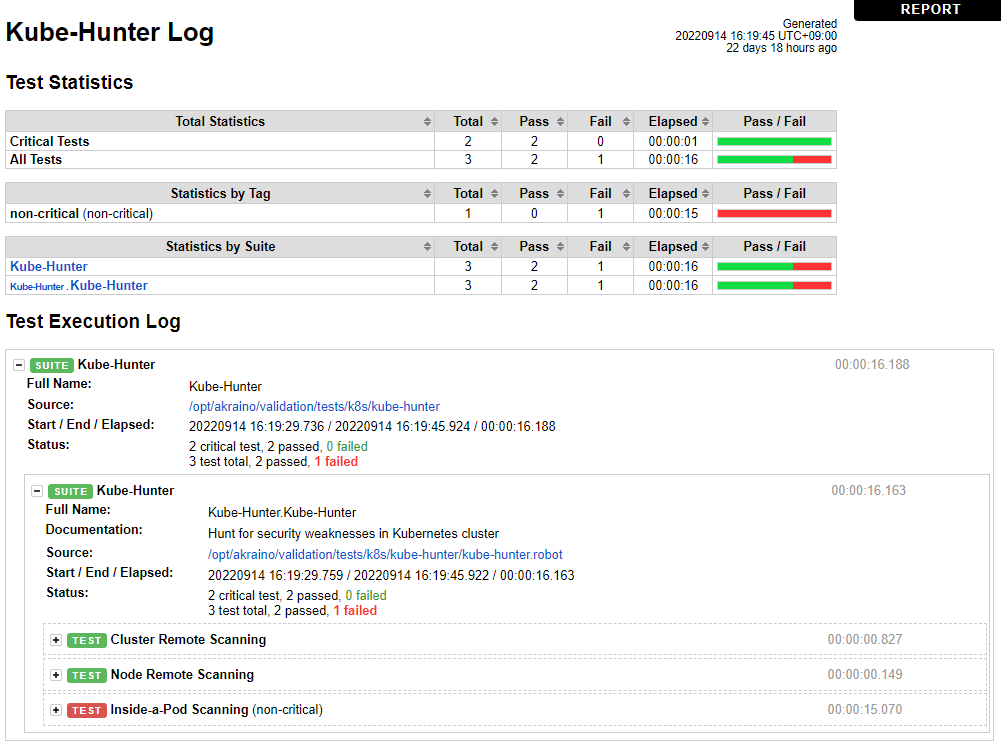
Results after fixes are shown below:
Note that in spite of all Kube-Hunter vulnerabilities being fixed, the results still show one test failure. The "Inside-a-Pod Scanning" test case reports failure, apparently because the log ends with "Kube Hunter couldn't find any clusters" instead of "No vulnerabilities were found." This also occurred during release 6 testing. Because vulnerabilities were detected and reported earlier in release 6 by this test case, and those vulnerabilities are no longer reported, we believe this is a false negative, and may be caused by this issue: https://github.com/aquasecurity/kube-hunter/issues/358
...