This document covers Integrated Edge Cloud(IEC) Type 2.
Integrated Edge Cloud(IEC) is an Akraino approved blueprint family and part of Akraino Edge Stack, which intends to develop a fully integrated edge infrastructure solution, and the project is completely focused towards Edge Computing. This open source software stack provides critical infrastructure to enable high performance, reduce latency, improve availability, lower operational overhead, provide scalability, address security needs, and improve fault management. The IEC project will address multiple edge use cases and industry, not just Telco Industry. IEC intends to develop solution and support of carrier, provider, and the IoT networks.
Use Case
The purpose of this release is to automate the provisioning of lightweight MEC environments and application stack on managed Cloud platforms like AWS.
The stack utilizes terraform to provision the underlying cloud infrastructure, and install a multi-node cluster using Canonical’s ‘microk8s’ distribution. The stack can be extended to bring up add-ons like kubeflow and EdgeXFoundry to process big data and AI workloads at the edge.
Overall Architecture
MEC stack for release 5 comprises the edge cloud stack which includes MicroK8s. The stack components are installed using Terraform on AWS. Installation of Storidge, EdgeXFoundry and Kubeflow is in the roadmap.
MicroK8s:
Microk8s is a lightweight Kubernetes distribution from Canonical. Snap package manager can be used to bring up Kubernetes in a single command. As of microk8s version 1.21, a snap installation consumes 192 MB RAM and the Kubernetes distribution consumes as little as 540 MB, making it an attractive solution to run on edge devices with less than 1GM of RAM.
Terraform:
An Infrastructure as Code tool by Hashicorp that automates the provisioning of data centre or cloud infrastructure. Terraform requires two files to automate the infrastructure provisioning
- Variables file (variable.tf): Run time tunables that helps to customize the infrastructure configuration.
- terraform configuration file (main.tf) : The Terraform configuration file has the required information to create an infrastructure. The configuration file is provided by the user.
- terraform state file: Terraform maintains the current state of the infrastructure in the state file. The state file remains empty until the first terraform initialization.
Storidge:
- Highly available persistent storage for K8s with auto-failover & recovery. Storidge automates storage infrastructure as code, delivering a persistent storage platform for Docker Swarm and Kubernetes. Storidge’s software enables automated storage orchestration including provisioning, application performance, data consistency and data protection via software. Storidge’s storage orchestrator enables stress-free storage administration for modern DevOps workflows.
EdgeXFoundry
- Middleware for dual processing of data to/from edge devices. It takes the sensor input from the devices and delivers it to the applications over the network to the end-users. Edgex has the microservices packed as docker images. EdgeX can be installed using the docker-compose file or from the snap store in a Linux environment.
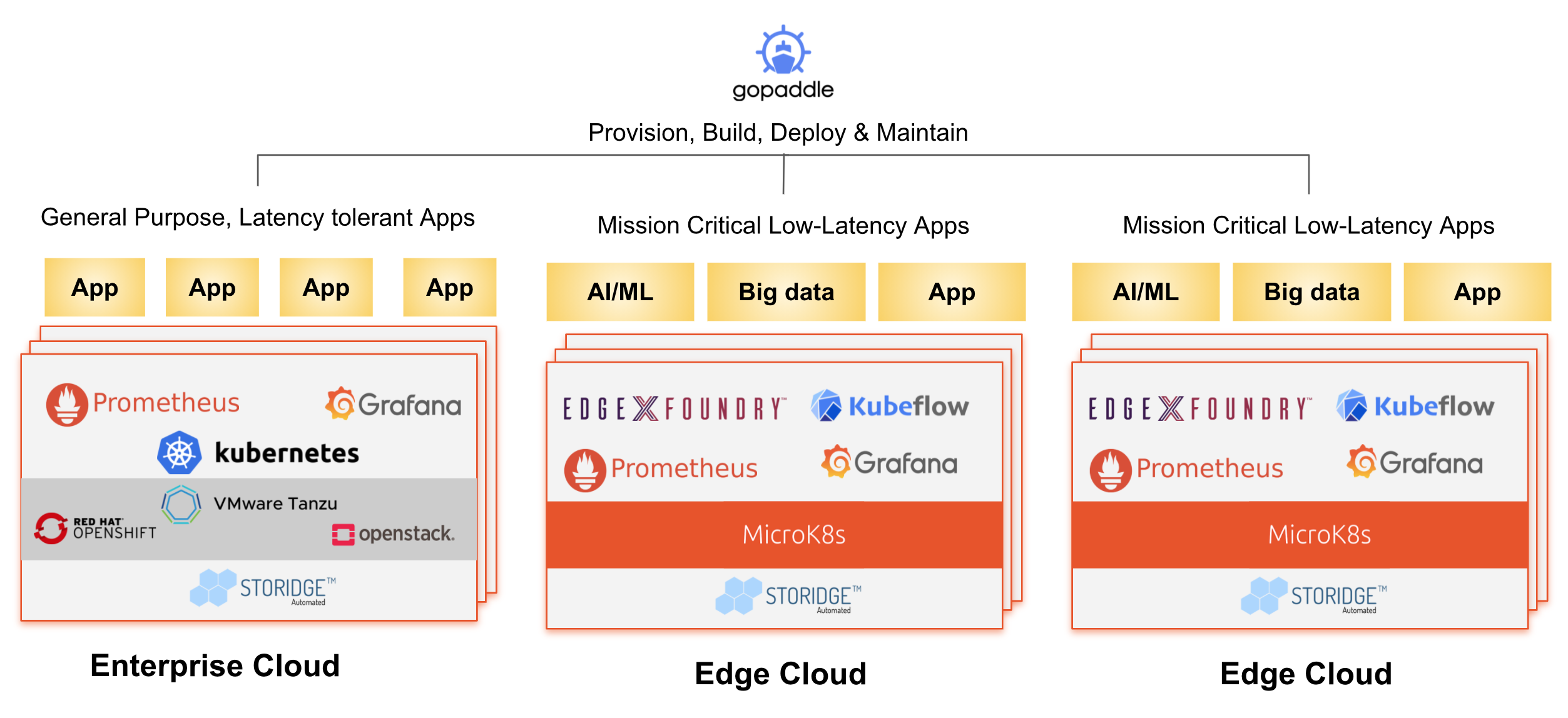
gopaddle
- A no-code platform that helps to build, deploy, and maintain cloud-native applications across hybrid environments. It reduces modernization efforts and automates DevOps workflows. It helps to provision MEC environments and centrally manage them.
AWS Infrastructure
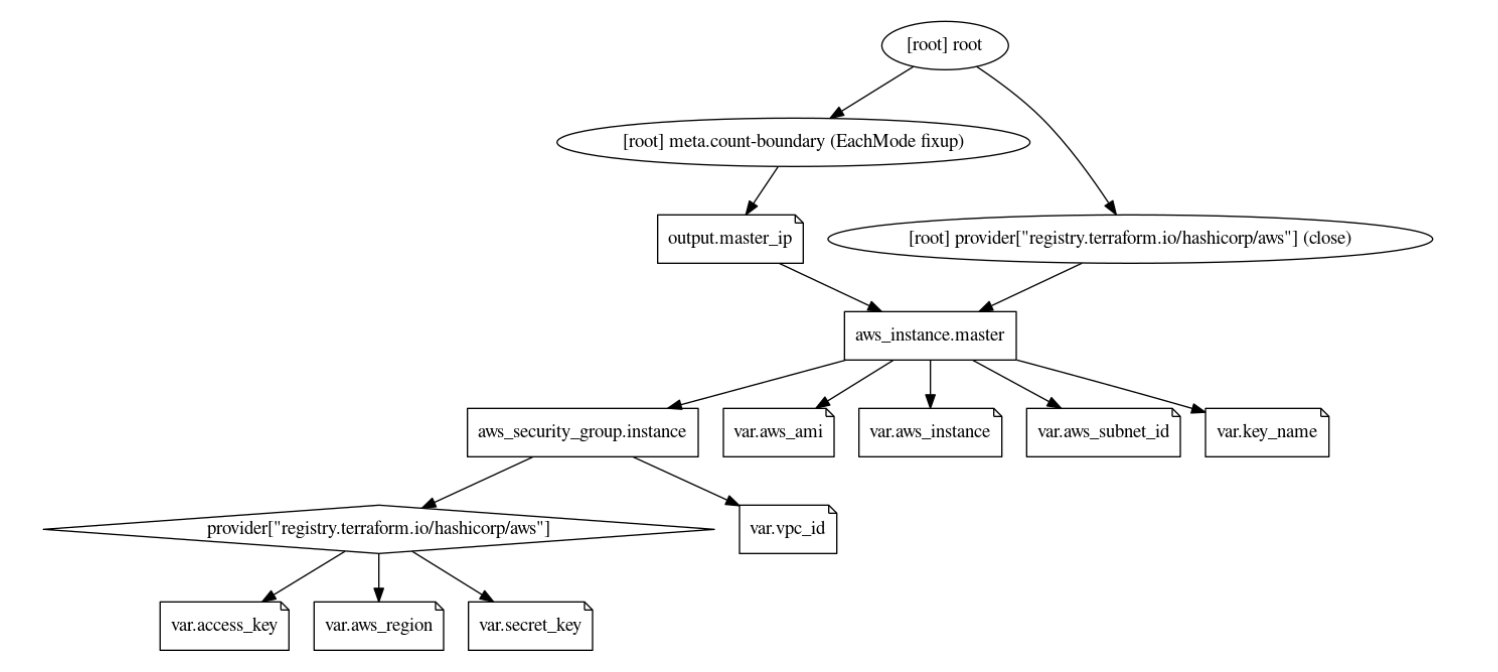
The below graph shows the infrastructure resources and their dependencies while provisioning the stack using terraform.
- The user provides the VPC ID, region, instance type, ami, subnet ID and the IAM access/secret as the input in the variable.tf file. The values are configurable at the time of applying the template.
- The variable ‘count’ indicates the number of worker node to be provisioned. A count of 2 brings up a 2 node cluster.
- We also need the PEM file to remote SSH into the EC2 instances. This file needs to be present in the same location as the main.tf and vairable.tf files.
- The security group is automatically provisioned based on the VPC and the Subnet ID provided.
- Currently, loadbalancer are not provisioned. Any workloads deployed in the cluster can be accessed via the Kubernetes Node port.
Workflow:
Master and Worker nodes are provisioned in this order:
- Provision master node. Execute user_data on the master node that installs microk8s.
- Once microk8s master is installed on the first node, generate a token to add nodes to the master node. We run the remote SSH command on the master node - ‘microk8s.join_token’ to generate the token. This makes use of the PEM file in the local directory to execute the remote command.
- Copy the generated token on the remote machine to the local machine. This is achieved using the terraform ‘datasource’ plugin.
- Now provision the worker nodes and install microk8s on the remaining nodes
- Use the local datasource to read the join token and add the worker nodes to the master node.