...
This document describes the blueprint test environment for the Smart Data Transaction for CPS blueprint. The test results and logs are posted in the Akraino Nexus at the link below:
https://nexus.akraino.org/content/sites/logs/fujitsu/job/sdt/r7
Akarino Test Group Information
...
The robot command should report success for all test cases.
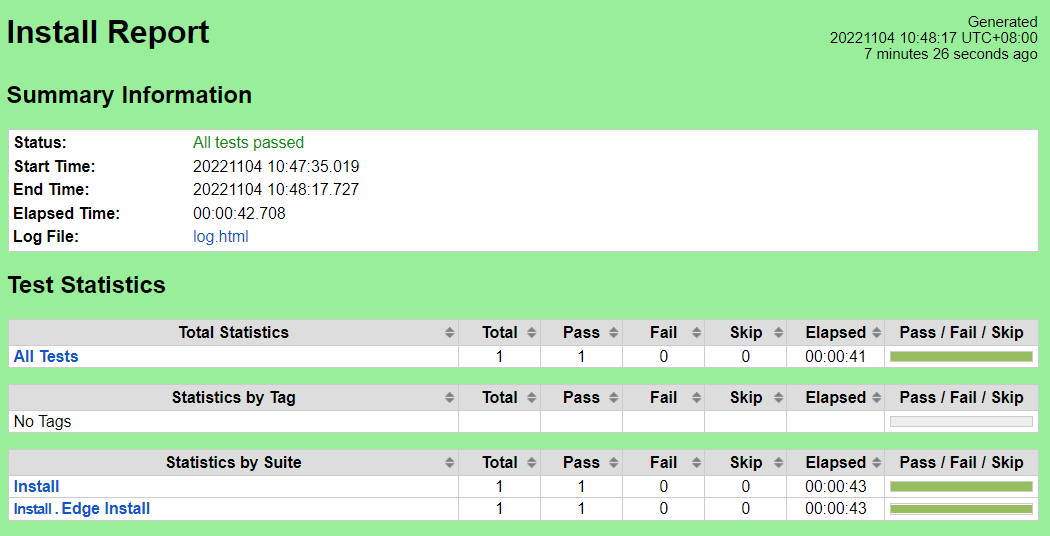
Test Results
Nexus URL: https://nexus.akraino.org/content/sites/logs/fujitsu/job/sdt/r7/lfedge-install/14/
Pass (1/1 test case)
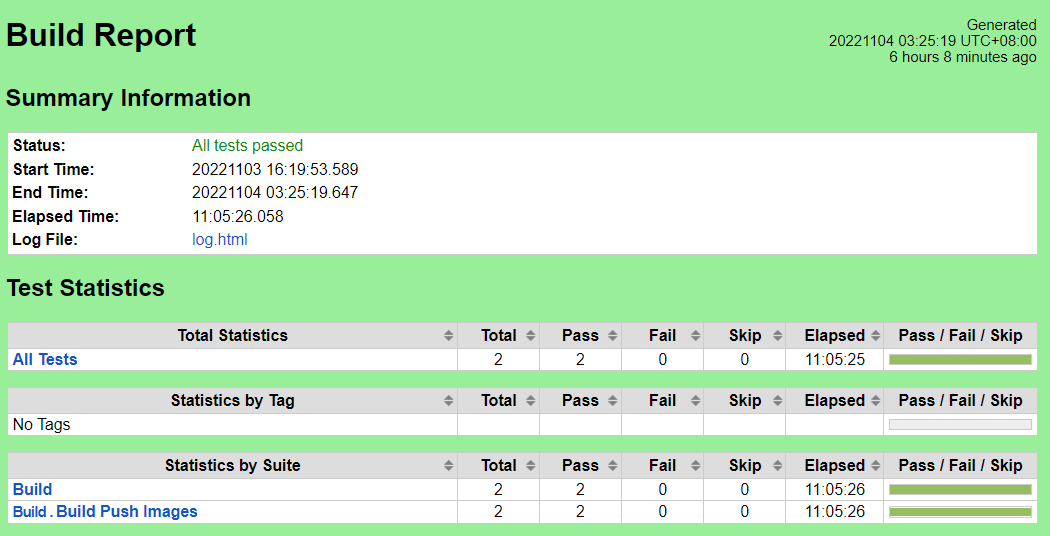
CI/CD Regression Tests: Images Build & Push
...
The robot command should report success for all test cases.
Test Results
Nexus URL: https://nexus.akraino.org/content/sites/logs/fujitsu/job/sdt/r7/lfedge-build/5
Pass (2/2 test cases)
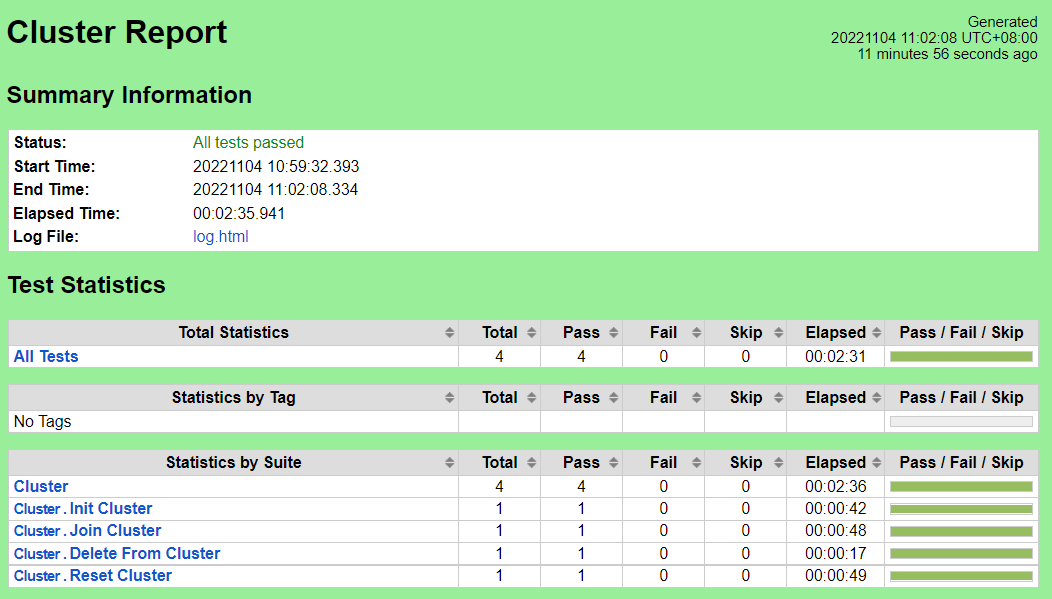
CI/CD Regression Tests: Cluster Setup & Teardown
...
The robot command should report success for all test cases.
Test Results
Nexus URL:
https://nexus.akraino.org/content/sites/logs/fujitsu/job/sdt/r7/lfedge-cluster/6
Pass (4/4 Pass (4/4 test cases)
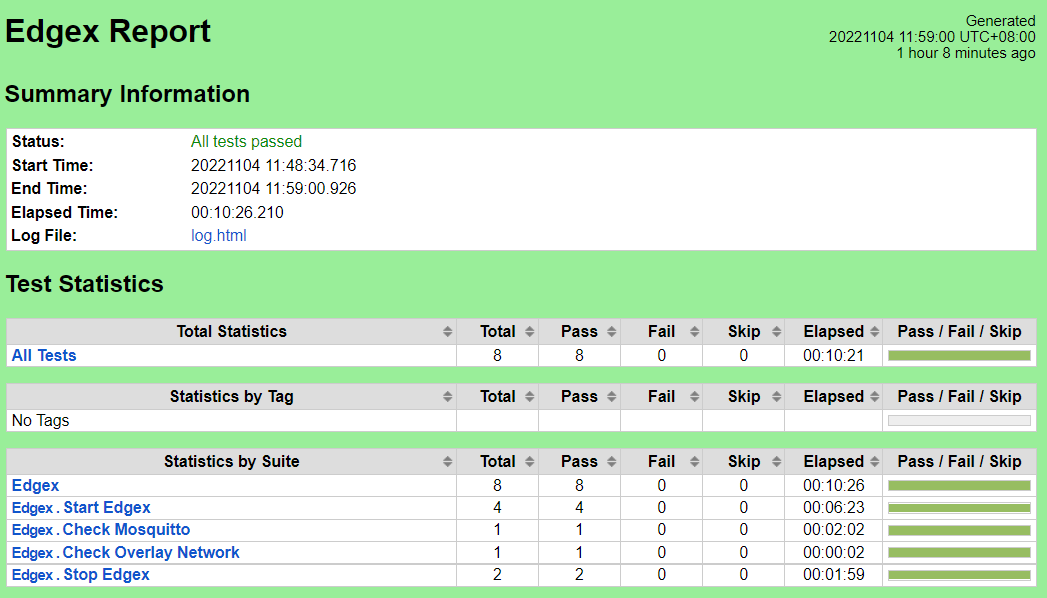
CI/CD Regression Tests: EdgeX Services
...
The robot command should report success for all test cases.
Test Results
Nexus URL: https://nexus.akraino.org/content/sites/logs/fujitsu/job/sdt/r7/edgex-install/7/
Pass (8/8 test cases)
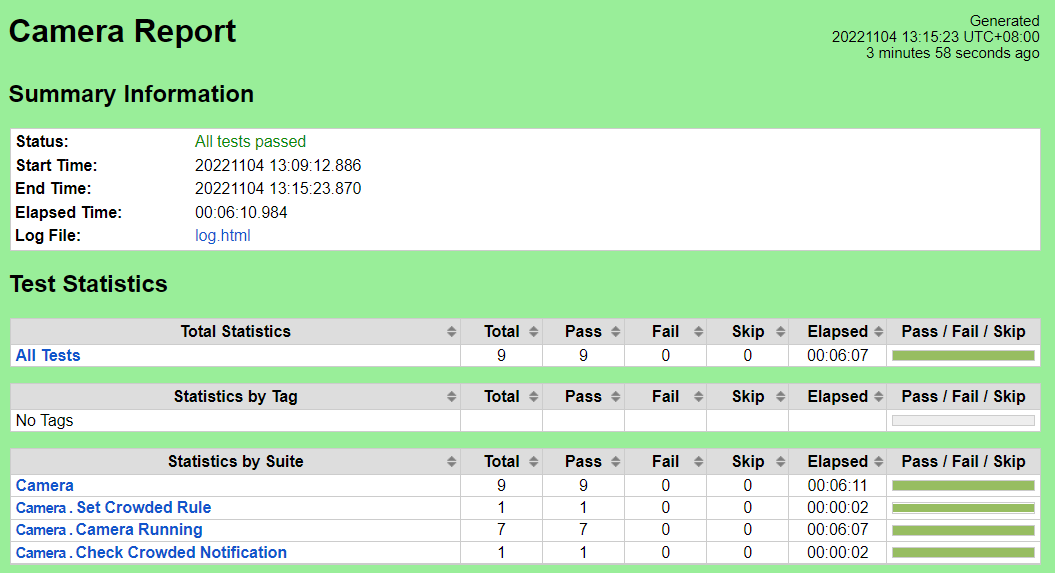
CI/CD Regression Tests: Camera Device Service
...
The Robot Framework should report success for all test cases
Test Results
Nexus URL:
https://nexus.akraino.org/content/sites/logs/fujitsu/job/sdt/r7/camera/10
Pass (9/9 Pass (9/9 test cases)
Feature Project Tests
...
- Copy the folder ~/.kube from Kubernetes master node to Build VM
- Create SSH Key on Build VM to access Kubernetes master node
Vuls
We use Ubuntu 20.04, and behind a proxy, so we run Vuls test as follows:
Create directory
$ mkdir ~/vuls $ cd ~/vuls $ mkdir go-cve-dictionary-log goval-dictionary-log gost-log
Fetch NVD
$ docker run --rm -it \ -v $PWD:/go-cve-dictionary \ -v $PWD/go-cve-dictionary-log:/var/log/go-cve-dictionary \ vuls/go-cve-dictionary fetch nvd --http-proxy $http_proxyFetch OVAL
$ docker run --rm -it \ -v $PWD:/goval-dictionary \ -v $PWD/goval-dictionary-log:/var/log/goval-dictionary \ vuls/goval-dictionary fetch ubuntu 14 16 17 18 19 20 --http-proxy $http_proxyFetch gost
$ docker run --rm -iit \
-v $PWD:/e http_proxy=$http_proxy \
-e https_proxy=$https_proxy \ -v $PWD:/gost \ -v $PWD/gost-log:/var/log/gost \ vuls/gost fetch ubuntu --http-proxy $http_proxyCreate config.toml
[servers] [servers.master] host = "192.168.51.22" port = "22" user = "test-user" keyPath = "/root/.ssh/id_rsa" # path to ssh private key in docker
Start vuls container to run tests
$ docker run --rm -it \ -v ~/.ssh:/root/.ssh:ro \ -v $PWD:/vuls \ -v $PWD/vuls-log:/var/log/vuls \ -v /etc/localtime:/etc/localtime:ro \ -v /etc/timezone:/etc/timezone:ro \ vuls/vuls scan \ -config=./config.toml \
--http-proxy $http_proxyGet the report
$ docker run --rm -it \ -v ~/.ssh:/root/.ssh:ro \ -v $PWD:/vuls \ -v $PWD/vuls-log:/var/log/vuls \ -v /etc/localtime:/etc/localtime:ro \ vuls/vuls report \ -format-list \ -config=./config.toml
Lynis
We use Ubuntu 20.04, so we run Lynis test manually as follows:
Login to master node, and get the latest Lynis from GitHub
\
--http-proxy $http_proxy
Lynis/Kube-Hunter
Create ~/validation/bluval/bluval-sdtfc.yaml to customize the Test
blueprint: name: sdtfc layers: - k8s
-
...
$ git clone https://github.com/CISOfy/lynis
Modify the permissions of the “lynis” directory
...
$ chmod -R 0:0 lynis
Run the command below to test the security of system
...
$ cd lynis; sudo ./lynis audit system
Lynis/Kube-Hunter
Create ~/validation/bluval/bluval-sdtfc.yaml to customize the Test
blueprint: name: sdtfc layers: - k8s
- os k8s: &k8s - name: kube-hunter what: kube-hunter optional: "False"
os: &os
-
name: lynis
what: lynis
optional: "False"Update ~/validation/bluval/volumes.yaml file
volumes: # location of the ssh key to access the cluster ssh_key_dir: local: '/home/ubuntu/.ssh' target: '/root/.ssh' # location of the k8s access files (config file, certificates, keys) kube_config_dir: local: '/home/ubuntu/kube' target: '/root/.kube/' # location of the customized variables.yaml custom_variables_file: local: '/home/ubuntu/validation/tests/variables.yaml' target: '/opt/akraino/validation/tests/variables.yaml' # location of the bluval-<blueprint>.yaml file blueprint_dir: local: '/home/ubuntu/validation/bluval' target: '/opt/akraino/validation/bluval' # location on where to store the results on the local jumpserver results_dir: local: '/home/ubuntu/results' target: '/opt/akraino/results' # location on where to store openrc file openrc: local: '' target: '/root/openrc' # parameters that will be passed to the container at each layer layers: # volumes mounted at all layers; volumes specific for a different layer are below common: - custom_variables_file - blueprint_dir - results_dir hardware: - ssh_key_dir os: - ssh_key_dir networking: - ssh_key_dir docker: - ssh_key_dir k8s: - ssh_key_dir - kube_config_dir k8s_networking: - ssh_key_dir - kube_config_dir openstack: - openrc sds: sdn: vim:Update ~/validation/tests/variables.yaml file
### Input variables cluster's master host host: <IP Address> # cluster's master host address username: <username> # login name to connect to cluster password: <password> # login password to connect to cluster ssh_keyfile: /root/.ssh/id_rsa # Identity file for authentication
Run Blucon
$ bash validation/bluval/blucon.sh sdtfc
...
Vuls results (manual) Nexus URL:
Lynis results (manual) Nexus URL:
Kube-Hunter results Nexus URL:
Vuls
Nexus URL:
https://nexus.akraino.org/content/sites/logs/fujitsu/job/sdt/r7/sdt-vuls/2/
Lynis results (manual) Nexus URL: https://nexus.akraino.org/content/sites/logs/fujitsu/job/sdt/r7/sdt-lynis/2/
Kube-Hunter results Nexus URL: https://nexus.akraino.org/content/sites/logs/fujitsu/job/sdt/r7/sdt-bluval/1/
Vuls
Nexus URL: https://nexus.akraino.org/content/sites/logs/fujitsu/job/sdt/r7/sdt-vuls/2/
There are 4 CVEs with There are 5 CVEs with a CVSS score >= 9.0. These These are exceptions requested here:
Release 7: Akraino CVE and KHV Vulnerability Exception Request
| CVE-ID | CVSS | NVD | Fix/Notes | ||||||
| CVE- | 20162022- | 15853643 | 910. | 80 | https://nvd.nist.gov/vuln/detail/CVE- | 20162022- | 1585No fix3643 | Fix not yet available | TODO: File exception request|
| CVE-20222016-03181585 | 9.8 | https://nvd.nist.gov/vuln/detail/CVE-20222016-03181585 | No fix Fix not yet available TODO: File exception request | ||||||
| CVE-2022-19270318 | 9.8 | https://nvd.nist.gov/vuln/detail/CVE-2022-19270318 | Fix not yet available TODO: File exception request | ||||||
| CVE-2022-203853649 | 9.8 | https://nvd.nist.gov/vuln/detail/CVE-2022-203853649 | Fix not yet No fix available TODO: File exception request | CVE-2022-37434 | 9.8 |
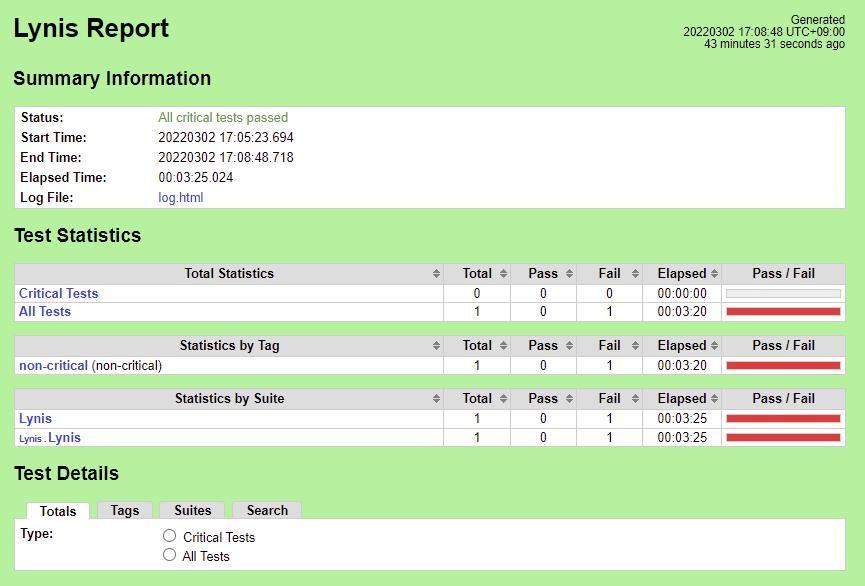
Lynis
Nexus URL (manual run, with fixes): https://
...
...
No fix available (for zlib1g, zlib1g-dev)
TODO: File exception request
akraino.org/content/sites/logs/fujitsu/job/sdt/r7/lynis/3/
The results compare with the Lynis Incubation: PASS/FAIL Criteria, v1.0 as follows.
Lynis
Nexus URL (run via Bluval, without fixes):
Nexus URL (manual run, with fixes):
The initial results compare with the Lynis Incubation: PASS/FAIL Criteria, v1.0 as follows.
The Lynis Program Update test MUST pass with no errors.
2022-09-14 16:19:49 Test: Checking for program update...
2022-09-14 16:19:49 Result: Update check failed. No network connection?
2022-09-14 16:19:49 Info: to perform an automatic update check, outbound DNS connections should be allowed (TXT record).
2022-09-14 16:19:49 Suggestion: This release is more than 4 months old. Check the website or GitHub to see if there is an update available. [test:LYNIS] [details:-] [solution:-]
The test environment is a proxied private network inside the Fujitsu corporate network which does not allow direct DNS lookups using tools such as dig. Therefore the update check cannot be performed automatically.
The latest version of Lynis, 3.0.8 at time of execution, was downloaded and run directly on the TODO Fix: Download and run the latest Lynis directly on SUT. See the link below:
Steps To Implement Security Scan Requirements#InstallandExecute
The following list of tests MUST complete as passing
| No. | Test | ResultFix | Notes | ||||||
|---|---|---|---|---|---|---|---|---|---|
| 1 | Test: Checking PASS_MAX_DAYS option in /etc/login.defs | 2022-0912-14 16 18:2045:32 Result: password aging limits are not configured TODO: Set PASS05 Test: Checking PASS_MAX_DAYS 180option in /etc/login.defs and rerun.
| Required configuration | ||||||
| 2 | Performing test ID AUTH-9328 (Default umask values) | 2022-0912-14 16 18:20:32 Result: found umask 022, which could be improved TODO: Set UMASK 027 in45:05 Performing test ID AUTH-9328 (Default umask values) 2022-12-16 18:45:05 Test: Checking /etc/login.defs | 3 | Performing test ID SSH-7440 (Check OpenSSH option: AllowUsers and AllowGroups) | TODO: Configure AllowUsers in /etc/ssh/sshd_config (allow only the admin account). | 4 | Test: checking for file /etc/network/if-up.d/ntpdate | 2022-09-14 16:20:46 Result: file /etc/network/if-up.d/ntpdate does not exist | Required configuration |
| 3 | OK | 5 | Performing test ID KRNLSSH- 60007440 (Check sysctl key pairs in scan profile) : Following sub-tests required | N/A | N/A | 5a | OpenSSH option: AllowUsers and AllowGroups) | 2022-12-16 18:45:14 Performing test ID SSH-7440 (Check OpenSSH option: AllowUsers and AllowGroups sysctl key fs.suid_dumpable contains equal expected and current value (0) | OK |
| 5b | sysctl key kernel.dmesg_restrict contains equal expected and current value (1) | 2022-09-14 16:20:58 Result: sysctl key kernel.dmesg_restrict has a different value than expected in scan profile. Expected=1, Real=0 | TODO: Add kernel.dmesg_restrict=1 to /etc/sysctl.d/90-lynis-hardening.conf | ||||||
| 5c | sysctl key net.ipv4.conf.default.accept_source_route contains equal expected and current value (0) | 2022-09-14 16:20:58 Result: sysctl key net.ipv4.conf.default.accept_source_route has a different value than expected in scan profile. Expected=0, Real=1 | TODO: Add net.ipv4.conf.default.accept_source_route=0 to /etc/sysctl.d/90-lynis-hardening.conf | ||||||
| 6 | Test: Check if one or more compilers can be found on the system | 2022-09-14 16:20:59 Result: found installed compiler. See top of logfile which compilers have been found or use /usr/bin/grep to filter on 'compiler' | TODO: Uninstall gcc and remove /usr/bin/as (installed with binutils) |
Results after the above fixes are as follows:
The Lynis Program Update test MUST pass with no errors.
TODO
The following list of tests MUST complete as passing
14 Result: AllowUsers set, with value sdt-admin | Required configuration | ||
| 4 | Test: checking for file /etc/network/if-up.d/ntpdate | 2022-12-16 18:45:16 Test: checking for file /etc/network/if-up.d/ntpdate 2022-12-16 18:45:16 Result: file /etc/network/if-up.d/ntpdate does not exist 2022-12-16 18:45:16 Result: Found a time syncing daemon/client. 2022-12-16 18:45:16 Hardening: assigned maximum number of hardening points for this item (3). Currently having 173 points (out of 246) | |
| 5 | Performing test ID KRNL-6000 (Check sysctl key pairs in scan profile) : Following sub-tests required | N/A | |
| 5a | sysctl key fs.suid_dumpable contains equal expected and current value (0) | 2022-12-16 18:45:27 Result: sysctl key fs.suid_dumpable contains equal expected and current value (0) | Required configuration |
| 5b | sysctl key kernel.dmesg_restrict contains equal expected and current value (1) | 2022-12-16 18:45:27 Result: sysctl key kernel.dmesg_restrict contains equal expected and current value (1) | Required configuration |
| 5c | sysctl key net.ipv4.conf.default.accept_source_route contains equal expected and current value (0) | 2022-12-16 18:45:27 Result: |
| No. | Test | Result | |||
|---|---|---|---|---|---|
| 1 | Test: Checking PASS_MAX_DAYS option in /etc/login.defs | TODO | |||
| 2 | Performing test ID AUTH-9328 (Default umask values) | TODO | |||
| 3 | Performing test ID SSH-7440 (Check OpenSSH option: AllowUsers and AllowGroups) | TODO | |||
| 4 | Test: checking for file /etc/network/if-up.d/ntpdate | TODO | 5 | Performing test ID KRNL-6000 (Check sysctl key pairs in scan profile) : Following sub-tests required | |
| 5a | sysctl key fs.suid_dumpable contains equal expected and current value (0) | TODO | |||
| 5b | sysctl key kernel.dmesg_restrict contains equal expected and current value (1) | TODO | |||
| 5c | sysctl key net.ipv4.conf.default.accept_source_route contains equal expected and | current value (0)TODO | current value (0) | Required configuration | |
| 6 | Test: Check if one or more compilers can be found on the system | 2022-12-16 18:45:28 Performing test ID HRDN-7220 (Check if one or more compilers are installed) | 6 | Test: Check if one or more compilers can be found on the system | TODO |
...
be found on the system | Required removal of build-essential package and apt autoremove, and /bin/as |
Kube-Hunter
Nexus URL: TODOhttps://nexus.akraino.org/content/sites/logs/fujitsu/job/sdt/r7/sdt-bluval/1/
There are no reported vulnerabilities. Note, this release includes fixes for vulnerabilities found in release 6. See the release 6 test document for details on those vulnerabilities and the fixes.
...
Note that the results still show one test failure. The "Inside-a-Pod Scanning" test case reports failure, apparently because the log ends with "Kube Hunter couldn't find any clusters" instead of "No vulnerabilities were found." This also occurred during release 6 testing. Because vulnerabilities were detected and reported in release 6 by this test case, and those vulnerabilities are no longer reported, we believe this is a false negative, and may be caused by this issue: https://github.com/aquasecurity/kube-hunter/issues/358
...