| CVE/KHV # | Blueprint | Blueprint OS/Ver | URL Showing OS Patch Not Available | Contact Name | Contact Email | Comment | Vendor CVSS Score | Vendor Patch Available | Exception Status |
|---|
| CVE-2016-1585 | Smart Data Transaction for CPS | Ubuntu 20.04 | https://ubuntu.com/security/CVE-2016-1585 | Colin Peters | colin.peters@fujitsu.com |
| Medium | No | Approved |
| CVE-2021-20236 | Smart Data Transaction for CPS | Ubuntu 20.04 | https://ubuntu.com/security/CVE-2021-20236 | | colin.peters@fujitsu.com |
| Medium | No | Approved |
| CVE-2021-31870 | Smart Data Transaction for CPS | Ubuntu 20.04 | https://ubuntu.com/security/CVE-2021-31870 | | colin.peters@fujitsu.com |
| Low | No | Approved |
| CVE-2021-31872 | Smart Data Transaction for CPS | Ubuntu 20.04 | https://ubuntu.com/security/CVE-2021-31872 | | colin.peters@fujitsu.com |
| Low | No | Approved |
| CVE-2021-31873 | Smart Data Transaction for CPS | Ubuntu 20.04 | https://ubuntu.com/security/CVE-2021-31873 | | colin.peters@fujitsu.com |
| Low | No | Approved |
| CVE-2021-33574 | Smart Data Transaction for CPS | Ubuntu 20.04 | https://ubuntu.com/security/CVE-2021-33574 | | colin.peters@fujitsu.com |
| Low | No | Approved |
| CVE-2021-45951 | Smart Data Transaction for CPS | Ubuntu 20.04 | https://ubuntu.com/security/CVE-2021-45951 | | colin.peters@fujitsu.com |
| Medium | No | Approved |
| CVE-2021-45952 | Smart Data Transaction for CPS | Ubuntu 20.04 | https://ubuntu.com/security/CVE-2021-45952 | | colin.peters@fujitsu.com |
| Medium | No | Approved |
| CVE-2021-45953 | Smart Data Transaction for CPS | Ubuntu 20.04 | https://ubuntu.com/security/CVE-2021-45953 | | colin.peters@fujitsu.com |
| Medium | No | Approved |
| CVE-2021-45954 | Smart Data Transaction for CPS | Ubuntu 20.04 | https://ubuntu.com/security/CVE-2021-45954 | | colin.peters@fujitsu.com |
| Medium | No | Approved |
| CVE-2021-45955 | Smart Data Transaction for CPS | Ubuntu 20.04 | https://ubuntu.com/security/CVE-2021-45955 | | colin.peters@fujitsu.com |
| Medium | No | Approved |
| CVE-2021-45956 | Smart Data Transaction for CPS | Ubuntu 20.04 | https://ubuntu.com/security/CVE-2021-45956 | | colin.peters@fujitsu.com |
| Medium | No | Approved |
| CVE-2021-45957 | Smart Data Transaction for CPS | Ubuntu 20.04 | https://ubuntu.com/security/CVE-2021-45957 | | colin.peters@fujitsu.com |
| Medium | No | Approved |
| CVE-2022-23218 | Smart Data Transaction for CPS | Ubuntu 20.04 | https://ubuntu.com/security/CVE-2022-23218 | | colin.peters@fujitsu.com |
| Low | Reported fixed in 2.31-0ubuntu9.7 (installed), but still reported by Vuls. | Approved |
| CVE-2022-23219 | Smart Data Transaction for CPS | Ubuntu 20.04 | https://ubuntu.com/security/CVE-2022-23219 | | colin.peters@fujitsu.com |
| Low | Reported fixed in 2.31-0ubuntu9.7 (installed), but still reported by Vuls. | Approved |
| CVE-2016-9180 | Smart Data Transaction for CPS | Ubuntu 20.04 | https://ubuntu.com/security/CVE-2016-9180 | | colin.peters@fujitsu.com |
| Low | No | Approved |
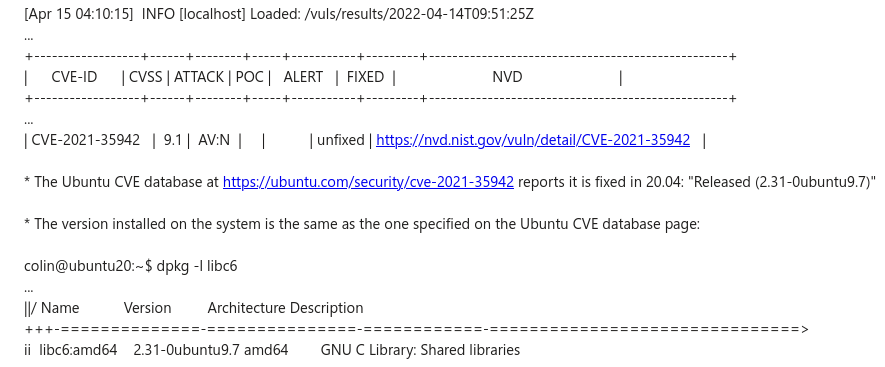
| CVE-2021-35942 | Smart Data Transaction for CPS | Ubuntu 20.04 | https://ubuntu.com/security/CVE-2021-35942 | | colin.peters@fujitsu.com | | Low | Reported fixed in 2.31-0ubuntu9.7 (installed), but still reported by Vuls. | Approved |
CVE-2016-1585 | Robot basic architecture based on SSES | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2016-1585 | | inoue.reo@fujitsu.com
|
| Medium | No | Approved |
CVE-2017-18201 | Robot basic architecture based on SSES | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2017-18201 | | inoue.reo@fujitsu.com
|
| Low | No | Approved |
CVE-2017-7827 | Robot basic architecture based on SSES | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2017-7827 | | inoue.reo@fujitsu.com |
| Medium | No | Approved |
CVE-2018-5090 | Robot basic architecture based on SSES | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2018-5090 | | inoue.reo@fujitsu.com |
| Medium | Reported fixed in 58 and later version (installed), but still reported by Vuls | Approved |
CVE-2018-5126 | Robot basic architecture based on SSES | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2018-5126 | | inoue.reo@fujitsu.com |
| Medium | Reported fixed in 58 and later version (installed), but still reported by Vuls | Approved |
CVE-2018-5145 | Robot basic architecture based on SSES | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2018-5145 | | inoue.reo@fujitsu.com |
| Medium | Reported fixed in 1:52.7.0 and later version (installed), but still reported by Vuls | Approved |
CVE-2018-5151 | Robot basic architecture based on SSES | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2018-5151 | | inoue.reo@fujitsu.com |
| Medium | Reported fixed in 60 and later version (installed), but still reported by Vuls | Approved |
CVE-2019-17041 | Robot basic architecture based on SSES | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2019-17041 | | inoue.reo@fujitsu.com |
| Low | No | Approved |
CVE-2019-17042 | Robot basic architecture based on SSES | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2019-17042 | | inoue.reo@fujitsu.com |
| Low | No | Approved |
CVE-2021-31870 | Robot basic architecture based on SSES | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2021-31870 | | inoue.reo@fujitsu.com |
| Low | No | Approved |
CVE-2021-31872 | Robot basic architecture based on SSES | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2021-31872 | | inoue.reo@fujitsu.com |
| Low | No | Approved |
CVE-2021-31873 | Robot basic architecture based on SSES | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2021-31873 | | inoue.reo@fujitsu.com |
| Low | No | Approved |
CVE-2021-39713 | Robot basic architecture based on SSES | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2021-39713 | | inoue.reo@fujitsu.com |
| Low | No | Approved |
CVE-2022-23852 | Robot basic architecture based on SSES | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2022-23852 | | inoue.reo@fujitsu.com |
| Medium | No | Approved |
CVE-2022-23990 | Robot basic architecture based on SSES | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2022-23990 | | inoue.reo@fujitsu.com |
| Medium | No | Approved |
CVE-2022-25235 | Robot basic architecture based on SSES | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2022-25235 | | inoue.reo@fujitsu.com |
| High | No | Approved |
CVE-2022-25236 | Robot basic architecture based on SSES | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2022-25236 | | inoue.reo@fujitsu.com |
| High | No | Approved |
CVE-2022-25315 | Robot basic architecture based on SSES | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2022-25315 | | inoue.reo@fujitsu.com |
| Medium | No | Approved |
CVE-2016-9180 | Robot basic architecture based on SSES | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2016-9180 | | inoue.reo@fujitsu.com |
| Low | No | Approved |
CVE-2019-20433 | Robot basic architecture based on SSES | Ubuntu 18.04 | https://ubuntu.com/security/CVE-2019-20433 | | inoue.reo@fujitsu.com |
| Low | No | Approved |
CVE-2005-2541 | Robot basic architecture based on SSES | Raspberry Pi OS(Debian 11) | https://security-tracker.debian.org/tracker/CVE-2005-2541 | | inoue.reo@fujitsu.com |
| High | No | Approved |
CVE-2014-2830 | Robot basic architecture based on SSES | Raspberry Pi OS(Debian 11) | https://security-tracker.debian.org/tracker/CVE-2014-2830 | | inoue.reo@fujitsu.com |
| High | No | Approved |
CVE-2016-1585 | Robot basic architecture based on SSES | Raspberry Pi OS(Debian 11) | https://security-tracker.debian.org/tracker/CVE-2016-1585 | | inoue.reo@fujitsu.com |
| High | No | Approved |
CVE-2017-17479 | Robot basic architecture based on SSES | Raspberry Pi OS(Debian 11) | https://security-tracker.debian.org/tracker/CVE-2017-17479 | | inoue.reo@fujitsu.com |
| High | No | Approved |
CVE-2017-9117 | Robot basic architecture based on SSES | Raspberry Pi OS(Debian 11) | https://security-tracker.debian.org/tracker/CVE-2017-9117 | | inoue.reo@fujitsu.com |
| High | No | Approved |
CVE-2018-13410 | Robot basic architecture based on SSES | Raspberry Pi OS(Debian 11) | https://security-tracker.debian.org/tracker/CVE-2018-13410 | | inoue.reo@fujitsu.com |
| High | No | Approved |
CVE-2019-1010022 | Robot basic architecture based on SSES | Raspberry Pi OS(Debian 11) | https://security-tracker.debian.org/tracker/CVE-2019-1010022 | | inoue.reo@fujitsu.com |
| High | No | Approved |
CVE-2019-8341 | Robot basic architecture based on SSES | Raspberry Pi OS(Debian 11) | https://security-tracker.debian.org/tracker/CVE-2019-8341 | | inoue.reo@fujitsu.com |
| High | No | Approved |
CVE-2020-27619 | Robot basic architecture based on SSES | Raspberry Pi OS(Debian 11) | https://security-tracker.debian.org/tracker/CVE-2020-27619 | | inoue.reo@fujitsu.com |
| High |
| Approved |
CVE-2021-29462 | Robot basic architecture based on SSES | Raspberry Pi OS(Debian 11) | https://security-tracker.debian.org/tracker/CVE-2021-29462 | | inoue.reo@fujitsu.com |
| High | No | Approved |
CVE-2021-29921 | Robot basic architecture based on SSES | Raspberry Pi OS(Debian 11) | https://security-tracker.debian.org/tracker/CVE-2021-29921 | | inoue.reo@fujitsu.com |
| High | Reported fixed in python3.9 (installed), but still reported by Vuls | Approved |
CVE-2021-30473 | Robot basic architecture based on SSES | Raspberry Pi OS(Debian 11) | https://security-tracker.debian.org/tracker/CVE-2021-30473 | | inoue.reo@fujitsu.com |
| High | No | Approved |
CVE-2021-30474 | Robot basic architecture based on SSES | Raspberry Pi OS(Debian 11) | https://security-tracker.debian.org/tracker/CVE-2021-30474 | | inoue.reo@fujitsu.com |
| High | No | Approved |
CVE-2021-30475 | Robot basic architecture based on SSES | Raspberry Pi OS(Debian 11) | https://security-tracker.debian.org/tracker/CVE-2021-30475 | | inoue.reo@fujitsu.com |
| High | No | Approved |
CVE-2021-30498 | Robot basic architecture based on SSES | Raspberry Pi OS(Debian 11) | https://security-tracker.debian.org/tracker/CVE-2021-30498 | | inoue.reo@fujitsu.com |
| High | No | Approved |
CVE-2021-30499 | Robot basic architecture based on SSES | Raspberry Pi OS(Debian 11) | https://security-tracker.debian.org/tracker/CVE-2021-30499 | | inoue.reo@fujitsu.com |
| High | No | Approved |
CVE-2021-42377 | Robot basic architecture based on SSES | Raspberry Pi OS(Debian 11) | https://security-tracker.debian.org/tracker/CVE-2021-42377 | | inoue.reo@fujitsu.com |
| Medium | No | Approved |
CVE-2021-45951 | Robot basic architecture based on SSES | Raspberry Pi OS(Debian 11) | https://security-tracker.debian.org/tracker/CVE-2021-45951 | | inoue.reo@fujitsu.com |
| High | No | Approved |
CVE-2021-45952 | Robot basic architecture based on SSES | Raspberry Pi OS(Debian 11) | https://security-tracker.debian.org/tracker/CVE-2021-45952 | | inoue.reo@fujitsu.com |
| High | No | Approved |
CVE-2021-45953 | Robot basic architecture based on SSES | Raspberry Pi OS(Debian 11) | https://security-tracker.debian.org/tracker/CVE-2021-45953 | | inoue.reo@fujitsu.com |
| High | No | Approved |
CVE-2021-45954 | Robot basic architecture based on SSES | Raspberry Pi OS(Debian 11) | https://security-tracker.debian.org/tracker/CVE-2021-45954 | | inoue.reo@fujitsu.com |
| High | No | Approved |
CVE-2021-45955 | Robot basic architecture based on SSES | Raspberry Pi OS(Debian 11) | https://security-tracker.debian.org/tracker/CVE-2021-45955 | | inoue.reo@fujitsu.com |
| High | No | Approved |
CVE-2021-45956 | Robot basic architecture based on SSES | Raspberry Pi OS(Debian 11) | https://security-tracker.debian.org/tracker/CVE-2021-45956 | | inoue.reo@fujitsu.com |
| High | No | Approved |
CVE-2022-23303 | Robot basic architecture based on SSES | Raspberry Pi OS(Debian 11) | https://security-tracker.debian.org/tracker/CVE-2022-23303 | | inoue.reo@fujitsu.com |
| Medium | No | Approved |
CVE-2022-23304 | Robot basic architecture based on SSES | Raspberry Pi OS(Debian 11) | https://security-tracker.debian.org/tracker/CVE-2022-23304 | | inoue.reo@fujitsu.com |
| Medium | No | Approved |
CVE-2021-4048 | Robot basic architecture based on SSES | Raspberry Pi OS(Debian 11) | https://security-tracker.debian.org/tracker/CVE-2021-4048 | | inoue.reo@fujitsu.com |
| Medium | No | Approved |
CVE-2021-43400 | Robot basic architecture based on SSES | Raspberry Pi OS(Debian 11) | https://security-tracker.debian.org/tracker/CVE-2021-43400 | | inoue.reo@fujitsu.com |
| Medium | No | Approved |
| CVE-2021-33574 | ICN | Ubuntu 20.04 | https://ubuntu.com/security/CVE-2021-33574 | Kuralamudhan Ramakrishnan | kuralamudhan.ramakrishnan@intel.com |
| Low | No | Approved |
| CVE-2019-19814 | ICN | Ubuntu 20.04 | https://ubuntu.com/security/CVE-2019-19814 | | kuralamudhan.ramakrishnan@intel.com |
| Low | No | Approved |
CVE-2021-35942 | ICN | Ubuntu 20.04 | https://ubuntu.com/security/CVE-2021-35942 | | kuralamudhan.ramakrishnan@intel.com | Vendor status is "Released" and ICN is using the referenced glibc version, however vuls is still reporting this. lsb_release -a; dpkg -l libc6 output: Distributor ID: Ubuntu
Description: Ubuntu 20.04.4 LTS
Release: 20.04
Codename: focal
No LSB modules are available.
Desired=Unknown/Install/Remove/Purge/Hold
| Status=Not/Inst/Conf-files/Unpacked/halF-conf/Half-inst/trig-aWait/Trig-pend
|/ Err?=(none)/Reinst-required (Status,Err: uppercase=bad)
||/ Name Version Architecture Description
+++-==============-===============-============-=================================
ii libc6:amd64 2.31-0ubuntu9.7 amd64 GNU C Library: Shared libraries | Low | Yes | Approved |
| KHV044 | ELIOT - IOTGateway |
|
|
| khemendra.kumar@huawei.com | KHV044 - Privileged Container
Minimize the use of privileged containers. Use Pod Security Policies to enforce using privileged: false policy. Calico pod is running in privileged Mode.
Exception Reason: Calico deployed by manifest file, can not be set to non privileged mode. Here is a link regarding the Calico Privilege Mode issue.
“Replace Kubernetes privileged=true with more precise permissions” It seems after long time they have make option to disable recently but only if calico deployed with Calic Operator.
And there is a doc about non-priviledged use of running Calico node for operator only.
In our ELIOT IOT Gateway BP, it is deployed by calico.yaml file.
and with manifest file, they don't support to disable it. So due to Calico limitation, and our ustream project dependency on calico.yaml manifest file, we can not fix it. IN future, we can ask the upstream EdgeGallery community to use calico operator for deployment and if they use operator, then it will be able to fix in our BPs, |
|
|
|
| KHV044 | EALTEdge - Enterprise application on 5G light weight telco edge |
|
|
| khemendra.kumar@huawei.com | KHV044 - Privileged Container
Minimize the use of privileged containers. Use Pod Security Policies to enforce using privileged: false policy. Calico pod is running in privileged Mode.
Exception Reason: Calico deployed by manifest file, can not be set to non privileged mode. Here is a link regarding the Calico Privilege Mode issue.
“Replace Kubernetes privileged=true with more precise permissions” It seems after long time they have make option to disable recently but only if calico deployed with Calic Operator.
And there is a doc about non-priviledged use of running Calico node for operator only.
In our EALTEdge BP, it is deployed by calico.yaml file.
and with manifest file, they don't support to disable it. So due to Calico limitation, and our ustream project dependency on calico.yaml manifest file, we can not fix it. IN future, we can ask the upstream EdgeGallery community to use calico operator for deployment and if they use operator, then it will be able to fix in our BPs, |
|
|
|
| CAP_NET_RAW | EALTEdge - Enterprise application on 5G light weight telco edge |
|
|
| khemendra.kumar@huawei.com | CAP_NET_RAW Enabled
CAP_NET_RAW is used to open a raw socket and is used by ping. If this is not required CAP_NET_RAW MUST be removed.
https://www.suse.com/c/demystifying-containers-part-iv-container-security/
For this BP, execption is approved in last release. plz refer last release exeception list Release 5 Blueprint Scanning Status |
|
|
|